OpenWRT developers disclosed the detection of a security incident over the past weekend, allegedly occurring because a threat actor managed to access the account of an administrator of their forum. OpenWRT is an open source project that provides free firmware, mainly for the use of home routers.
Project managers still do not determine how it was possible to abuse this account, as it had a very secure password although it was not backed by a multi-factor authentication mechanism: “Although the attacker failed to download copies of our database, the incident resulted in the download of a list of forum users, which includes personal details such as usernames and email addresses”, the developers mentioned.
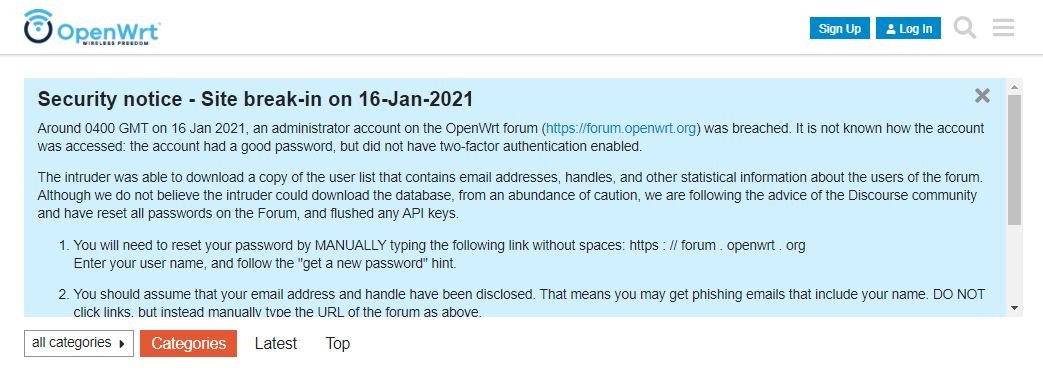
The compromised data does not include user passwords, although to take extreme precautions the developers decided to reset the passwords of all forum members, so users will need to complete this process the next time they log in. This measure also applies to those who use OAuth tokens.
Cybersecurity specialists believe that there could be an increase in phishing attacks against affected users, as their email addresses were obtained by the attackers. It is important to note that the OpenWRT forum is mainly frequented by developers working for the vast majority of companies collaborating with this project.
“We urge forum users not to click on any links contained in emails from unknown users; Instead, you can verify the authenticity of the link or attachments received,” the developers conclude. The message concludes by emphasizing that the rest of OpenWRT’s IT infrastructure is completely safe.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
