According to statistics gathered by the Carnegie Endowment for International Peace, there have been over 200 recorded cyber incidents against banks and financial organizations since 2007. Some of the most recent cyberattacks have targeted bitcoin exchanges. Jerome Powell, the chairman of the Federal Reserve, issued a warning about “cyber risk” as a major danger to financial institutions last year.
Researchers with the cybersecurity firm Group-IB came to the conclusion that the group, known as “OPERA1ER,” infiltrates numerous accounts, seizes control of them, and then moves money into accounts it controls before cashing out mostly through ATM withdrawals.
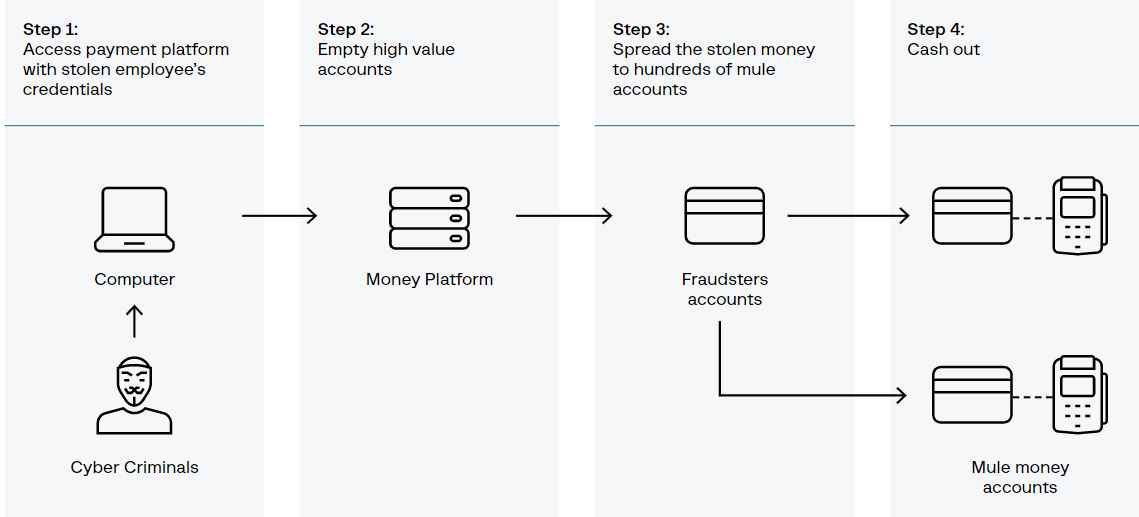
The attackers would gain access to networks and wait three to twelve months before stealing any money. During that time, they would identify important figures within the financial institutions, research the fraud-prevention measures in place, and comprehend how the back-end platform operated and how cash withdrawals worked. The attackers profited from their attacks by at least $11 million, however they may have taken home nearly three times that much.
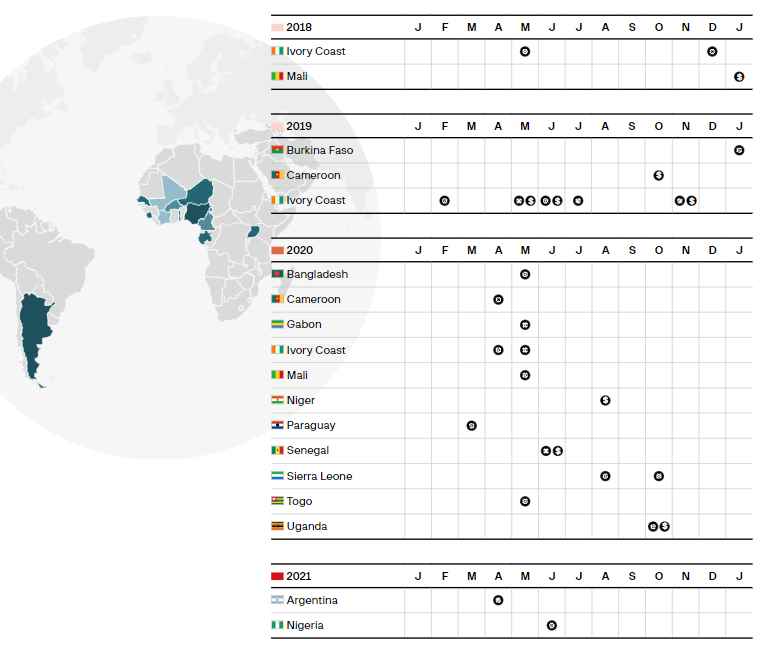
At least two of the target banks had their SWIFT messaging interfaces successfully breached by the attackers, allowing them to transmit information about financial transactions. The operations of OPERA1ER show how widespread this risk is. In at least 15 nations, including the Ivory Coast, Mali, Burkina Faso, Benin, Cameroon, Bangladesh, Gabon, Niger, Nigeria, Paraguay, Senegal, Sierra Leone, Uganda, Togo, and Argentina, the gang has successfully attacked banks and other institutions. Following a string of targeted cyberattacks on financial institutions in Africa, the researchers claimed they started following the cybercrime gang in 2019. The next year, the researchers were able to identify a single organization as being responsible for the attacks. By 2021, the researchers were ready to disclose their findings on the organization but decided against doing so since they thought the group had become aware of their presence and was attempting to hide their activities.
Security experts have monitored several facets of the group’s work in recent years. Beginning in 2019, Swiss security researcher Tom Ueltschi started making information on a group he termed “DESKTOP-Group” available to the public, including email headers, malware hashes, and command and control information. The cybersecurity company Rewterz, located in Dubai, provided hashes from a file used by a group it identified as “Common Raven” in 2020. The messaging platform SWIFT, which banks use for international transactions, released an alert on group activities in 2021. One of the many commercial tools used by OPERA1ER was the adversary emulation tool Cobalt Strike, which was linked to the group in August 2022 by a researcher. This discovery allowed the researchers to identify an additional five attacks that took place in four different countries after the initial research was finished. In addition to fingerprints pointing to earlier OPERA1ER tools, the August finding produced updated information on domains and numerous additional IP addresses connected to the organization.
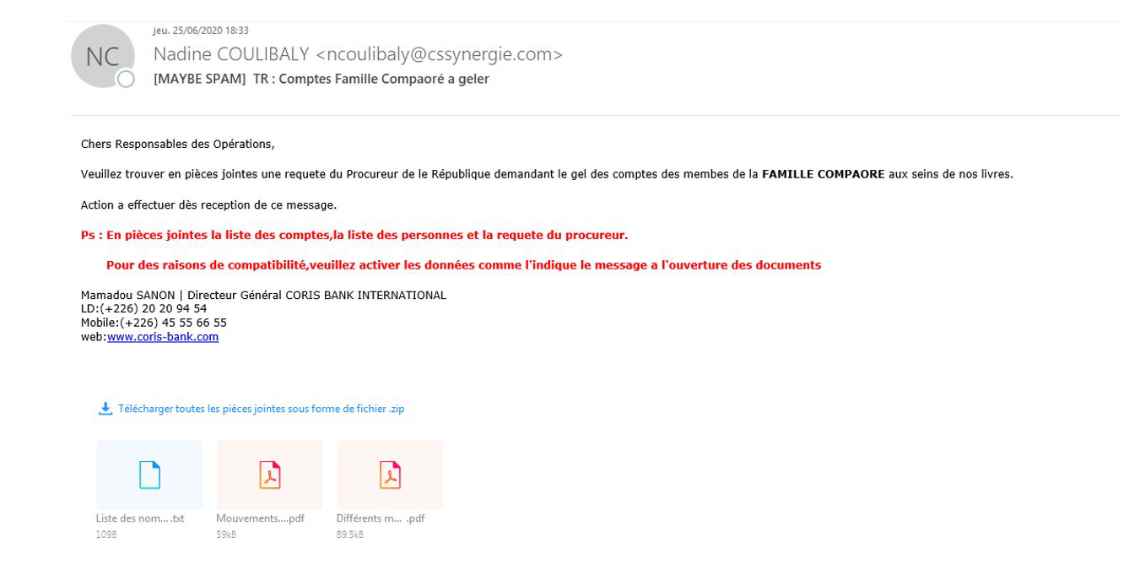
The organization has carried out over 30 assaults against banks, financial services companies, and telecommunications companies using high-quality spear phishing and commercially available technologies, potentially reaping $30 million from businesses in Africa, Asia, and Latin America.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
