A recently launched enterprise driven by financial gain is using a malicious Telegram bot to assist threat actors in defrauding unsuspecting victims.
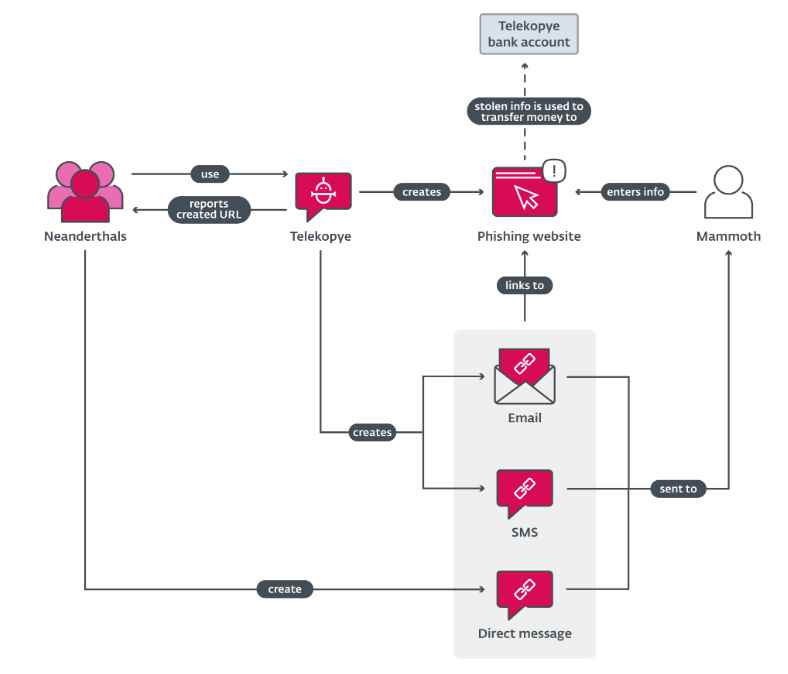
The criminals referred to prospective victims as Mammoths and gave the toolkit the name Telekopye, which is a combination of the words Telegram and kopye, which means “spear” in Russian as per the research. The toolkit serves as an automated way of creating a phishing web page using a preset template and sending the URL to possible victims. Each and every Telegram group that makes use of Telekopye is composed of one or more Neanderthals who function concurrently and autonomously. The functionality is provided via buttons, which is expected to make it simpler for Neanderthals to commit fraud. Neanderthals can also be called as Threat actors or scammers.
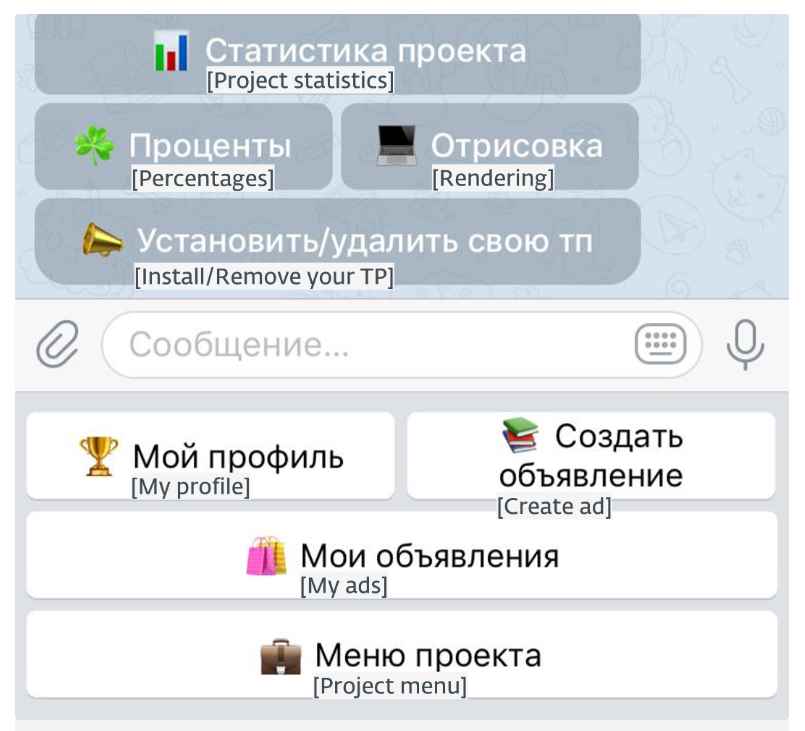
This figure is one of the menus that may be accessed with Telekopye inside an operational Telegram group. Notable buttons include “My ads,” which displays all opened listings (ongoing scam advertisements) that each Neanderthal has, and “My profile,” which enables Neanderthals to view their profile information on this platform, including the number of scams they have successfully pulled off, the amount of money that is ready for the next payout, and other relevant information. These buttons are particularly noteworthy. The most important function of Telekopye is that it can generate phishing websites on demand by using preset HTML templates as a starting point.
A Neanderthal is required to indicate the amount of money, the product name, and, depending on the template, extra information such as the location to which the product will be transported, a photo of the product, the product’s weight, and the name of the buyer. After that, Telekopye compiles all of this data into a fake website in order to commit phishing. These phishing web pages are meant to replicate the appearance of other payment and bank login sites, credit card and debit card payment gateways, or simply the payment pages of other websites.
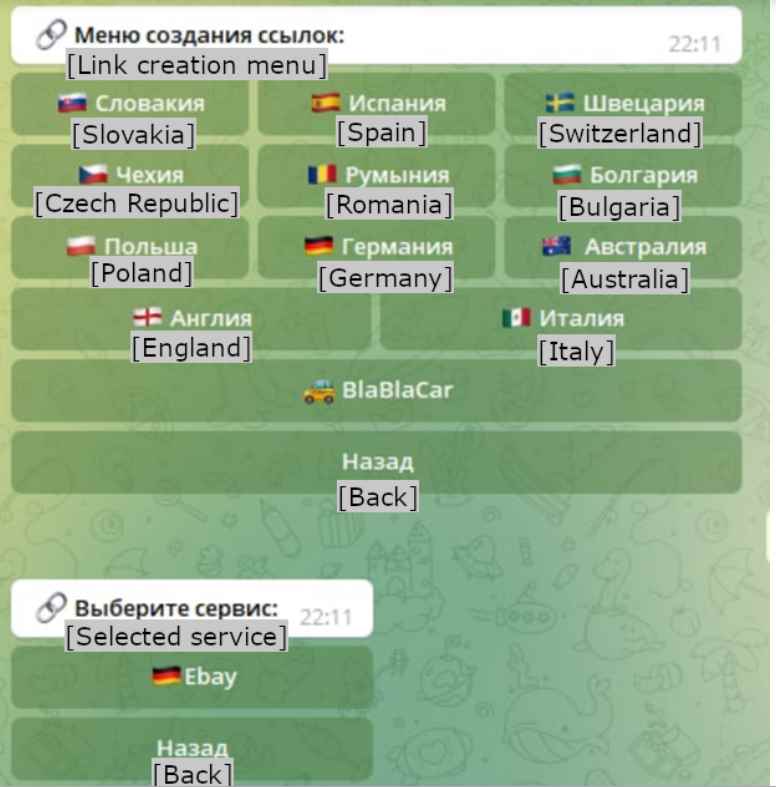
These website templates are arranged according to the nations that they target so that the process of creating phishing websites may be completed more quickly. This figure illustrates a straightforward creation menu, in which several templates are arranged in accordance with the various nations. In terms of car-sharing services that are not country-specific, BlaBlaCar is the lone exception.
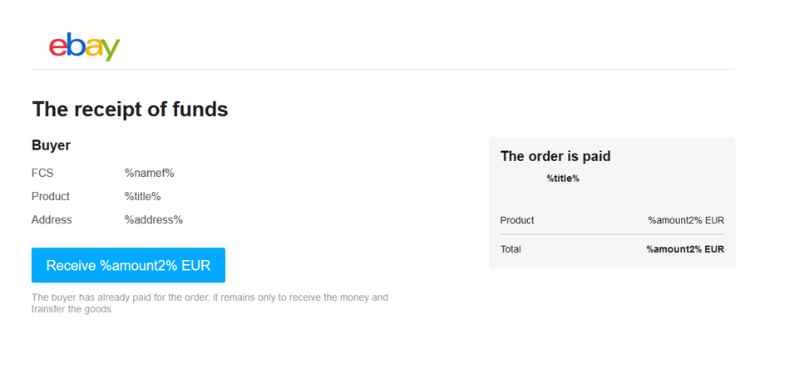
A look-alike eBay web page that is almost indistinguishable from the original (or at the very least seems to be something that one would anticipate seeing on the genuine website). If a Mammoth clicks the button labeled Receive %amount2% EUR, it will be presented with a sham credit and debit card gateway.
Neanderthals are able to teach Telekopye to compose and send email messages following their instructions. The message was sent using a preconfigured email address that was accessible to all Neanderthals. Typically, these email accounts are related with the phishing websites that were established by Neanderthals. The code that may be used to spoof the email headers From and Reply-To in order to make the email messages seem to be more authentic. In addition to phishing emails, Telekopye enables Neanderthals to generate and deliver SMS texts in a way that is similar to what is done with emails. Even preset SMS messages in a variety of languages are available in certain implementations of the Telekopye protocol. The standard text message templates all convey more or less the same information, such as “Your item has been paid for.”
Image modification is yet another feature that is included in this section of Telekopye and is not any less vital for it. It is conceivable to deduce, based on the code and the comments that accompany it, that it has the capability of altering photos of promoted products in such a way that search engines are unable to cross-reference them. We presume that artificial intelligence antispam protection would identify the picture as harmful if it was discovered in an online marketplace. This modification is really straightforward and consists of inverting the picture vertically and making a minute adjustment to the contrast.

Users and operators of Telekopye are structured in a clear hierarchy, which is another indication that the criminal organization is becoming more professionalized. This hierarchy includes positions such as administrators, moderators, good workers (or support bots), workers, and banned – users.
Blocked users are those who are not allowed to use Telekopye because it is suspected that they have violated some of the project’s guidelines.
Workers is the standard job description for all newly created Neanderthals.
Good employees get a promotion to the Worker job, which results in a greater reward and a reduction in the commission fees that are required.
Moderators are users who have the ability to promote and demote other members, as well as authorize new members, but they do not have access to the settings for the toolkit.
Administrators are users with the greatest rights, with the ability to create phishing web page designs and change reward rates. Administrators may also change the payout rates.
If a text message or email contains a link, you should exercise extreme caution before clicking on it, even if the sender seems to be a trustworthy organization. The Neanderthals are not unfamiliar with the practice of email spoofing. Asking yourself if you purchased anything that would cause credible sources to send you emails like that is a solid rule of thumb to follow. Visit the website of the purported service directly (rather than utilizing the link provided in the email or SMS) and inquire if you have any doubts. The majority of these websites provide customer service, and the representatives there will be more than happy to assist you.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
