The recent findings from McAfee Labs have unveiled a worrying trend in the cybersecurity landscape: a significant increase in malware distribution through PDF files. This revelation is particularly concerning because it challenges the conventional wisdom that malware primarily spreads through suspicious websites or downloads. Instead, it appears that seemingly innocuous emails, especially those with PDF attachments, are becoming a favored vector for cybercriminals.
Why PDFs?
The shift towards exploiting PDF files can be traced back to Microsoft’s implementation of macro-blocking measures for Office files delivered via the internet. This move forced threat actors to seek alternative avenues for distributing email-based malware. PDFs, with their complex structure, have proven to be particularly susceptible to exploitation. Their widespread use as a medium for distributing documents via email makes them an attractive target for attackers looking to leverage the trust users place in them. By embedding payloads within these PDFs, which are then hosted on malicious websites, attackers can easily trick users into downloading malware.
The Infection Chain
A notable example of this emerging threat involves the malware known as Agent Tesla. The infection process begins with an email containing a malicious PDF attachment. Depending on the version of Acrobat Reader installed on the victim’s device, the attack unfolds in different ways. In outdated versions of Acrobat Reader, the PDFs can directly execute embedded JavaScript, leading to the automatic launch of malicious payloads. For users with the latest version of Acrobat Reader, the PDF instead redirects them to a malicious website from which the malware is downloaded.
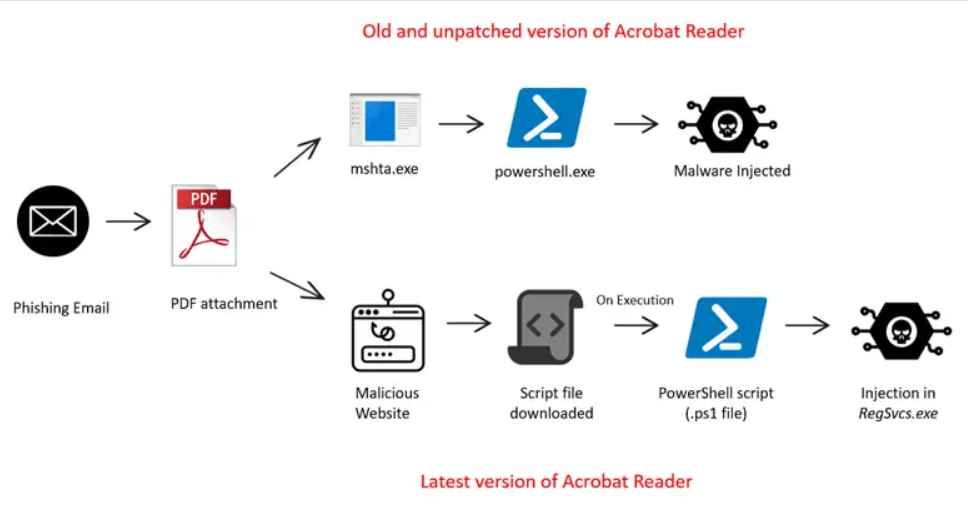
A recent attack utilized a PDF named “Booking.com-1728394029.pdf,” masquerading as a legitimate communication from Booking.com. This PDF contained embedded URLs and hex data designed to redirect users to a deceptive website, further illustrating the sophistication of these attacks.
Execution and Defense Evasion
Upon execution, the malware follows a complex process designed to evade detection and establish persistence on the infected system. This includes disabling system defenses, creating registry entries for persistence, and injecting the final payload into legitimate processes. The use of heavily obfuscated JavaScript files complicates the analysis and detection of the malicious code.
Privilege Escalation and Persistence
The attackers employ various techniques for privilege escalation and to ensure the malware remains active on the system. This includes creating scheduled tasks and registry entries that trigger the malware to execute at regular intervals, ensuring its persistence even after system reboots.
Exfiltration
One of the most alarming aspects of these attacks is the use of Telegram bots for data exfiltration. By leveraging the secure and anonymous nature of Telegram, attackers can siphon off sensitive information from the infected system without raising suspicion. This method of exfiltration underscores the need for robust security measures that can detect and block such unconventional data theft techniques.The rise in malware distribution through PDF files is a stark reminder of the evolving threat landscape. Cybercriminals continue to find innovative ways to exploit trusted file formats and bypass security measures. This trend underscores the importance of maintaining up-to-date security software, practicing cautious email hygiene, and educating users about the potential risks associated with seemingly harmless attachments. As attackers refine their methods, the cybersecurity community must remain vigilant and proactive in developing defenses against these sophisticated threats.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
