Recent investigations suggest that malicious actors have been spreading the DarkGate Loader malware by exploiting Microsoft Teams as a delivery mechanism.
The campaign was started by two external Office 365 accounts that were hacked and their identities have been revealed to be “Akkaravit Tattamanas” (63090101@my.buu.ac.th) and “ABNER DAVID RIVERA ROJAS” (adriverar@unadvirtual.edu.co). “Unfortunately, the currently available security features for Microsoft Teams, such as Safe Attachments or Safe Links, were not able to detect or block this attack.” reads the message that was posted by Truesec. This campaign was uncovered as a result of the beneficiaries’ prior participation in security awareness training.
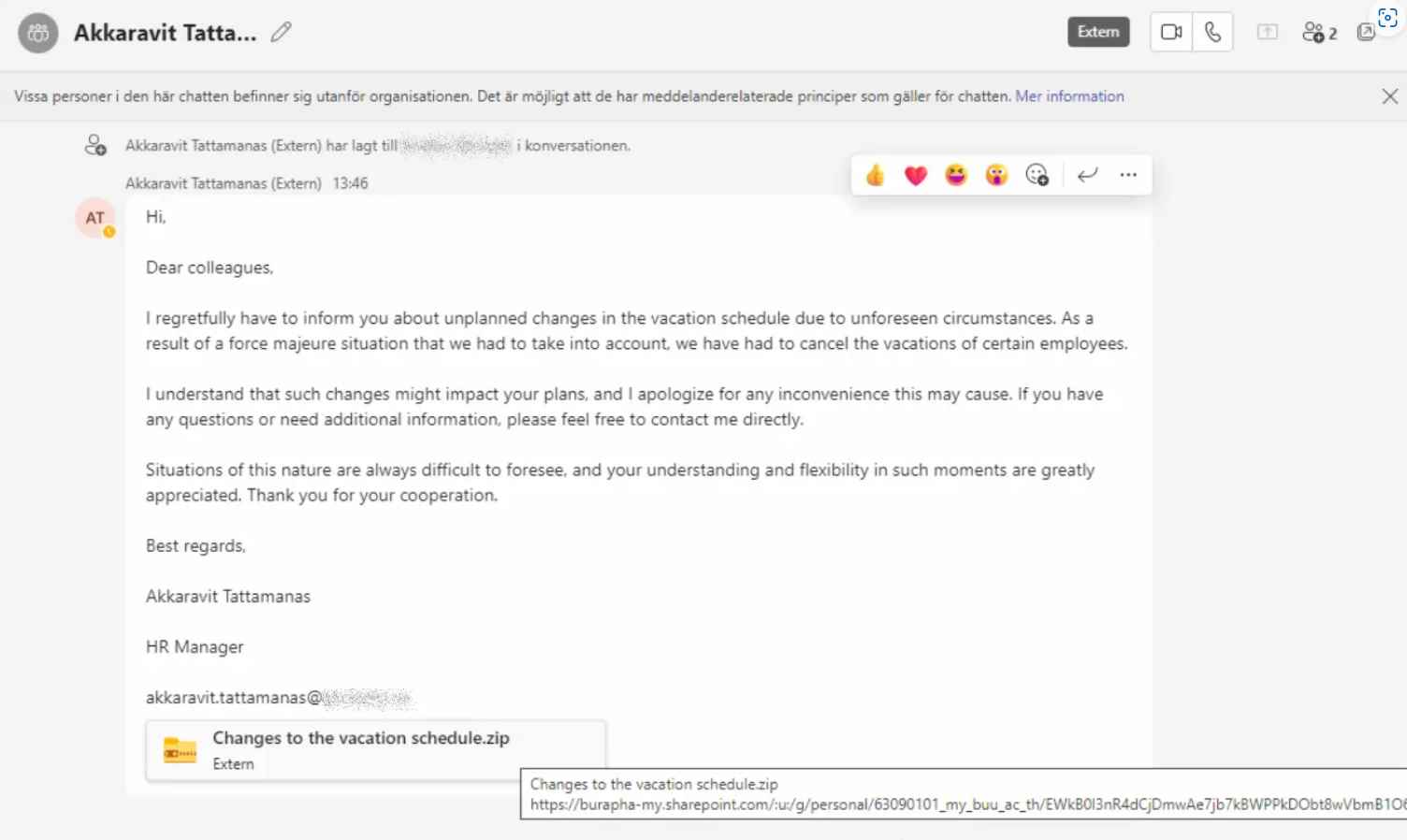
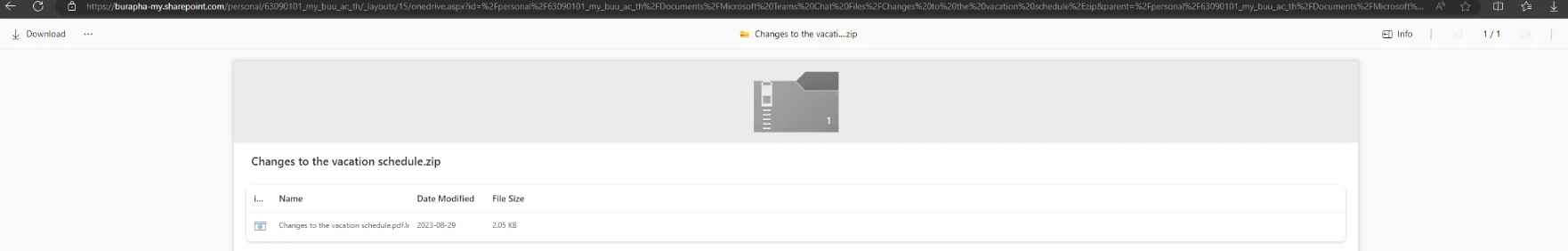
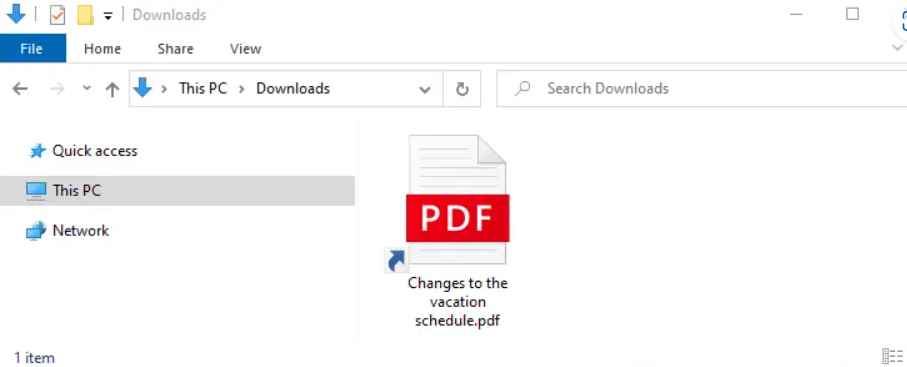
After further examination, it was discovered that the chat messages were composed of a link to an externally hosted Sharepoint site. This Sharepoint link leads to a ZIP file that is titled “Changes to the vacation schedule.zip.” After the victims have downloaded this ZIP file, they will find that it contains an LNK file (a kind of shortcut) that is disguised as a PDF document. The LNK file bears the name “Changes to the vacation schedule.pdf.lnk.” Further investigation of the LNK file showed that, when opened, the file contains numerous instructions for a chain of execution. If the file is opened, the chain of execution will begin by creating a VBScript file in the C:tpgh directory with the name “asrxmp.vbs” and then automatically executing that file.
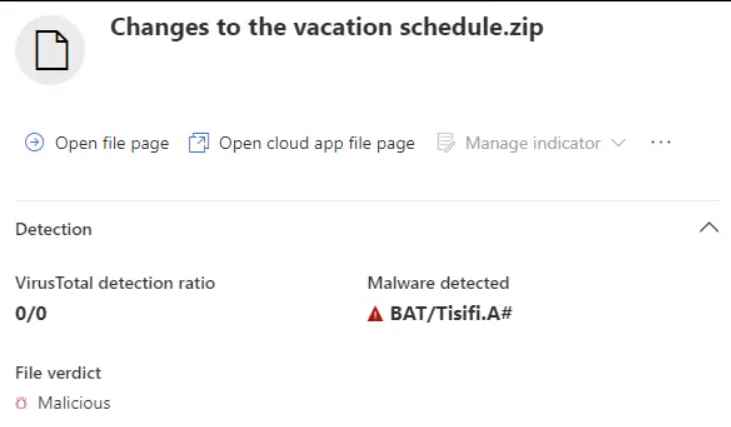
When the VBScript file is run, it will download the file from the remote server located at hXXp:// 5[.]188[.]87[.]58:2351/wbzadczl and run it once it has been downloaded. This execution results in the use of the Windows version of cURL, which has been renamed to wbza, in order to download and run the bundled script eszexz.au3, as well as Autoit3.exe. This AutoIT script will first delete an additional shellcode file and then check to see whether Sophos is already installed before actually running the script. In the event that this is not the case, the AutoIT script decrypts its code even more and then executes the shellcode.
This last execution of shellcode generates a file that is byte for byte designed to load a new Windows executable that has been referred to as the “DarkGate loader” malware.
Malware known as DarkGate loader was first discovered in 2017, however at the time it was only being used by its initial creator. Malware-as-a-service (MaaS) was a marketing term that was introduced in June 2023 by the producer of the malicious software, and it was used in a number of online cybercrime forums.
Email was the primary method of transmission until one of the operators came up with an alternative plan and began using Microsoft Teams as a delivery mechanism for the virus. A social engineering chat message with a human resources (HR) topic was what was delivered to the victims as the message context.
It is advised that organizations and IT managers add various security measures, such as permitting chat requests from particular external domains to be sent to Microsoft Teams and building a whitelist of trustworthy domains. Other security features may also be implemented.
It is also essential that companies teach their personnel in cyber security awareness. This training may educate all of the employees and help avoid future attacks.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
