A new research focuses on a newly discovered set of attacks against Active Directory (AD) using Microsoft DHCP servers, which could lead to a full AD takeover. This vulnerability is significant because it involves the exploitation of DHCP DNS Dynamic Updates, a process integral to many network configurations. The researchers at Akamai have delved into the technical aspects of these attacks, providing insights into how they can be executed and the potential risks they pose to organizations relying on Active Directory for their network infrastructure.
The vulnerability discovered by Akamai researchers revolves around exploiting DHCP DNS Dynamic Updates in Microsoft Active Directory environments. Here’s a breakdown of how this vulnerability works and its implications:
DHCP DNS Dynamic Updates:
Dynamic Host Configuration Protocol (DHCP) is commonly used in networks to automatically assign IP addresses to devices. In many configurations, DHCP servers are also responsible for dynamically updating DNS records. This is where the vulnerability lies. The exploit targets the process by which DHCP servers update DNS records. In a typical scenario, when a device connects to a network, the DHCP server assigns it an IP address and updates the DNS records accordingly. However, if an attacker can manipulate this update process, they can potentially redirect network traffic or impersonate other devices on the network. Active Directory (AD) is heavily reliant on DNS for its functioning. It uses DNS to locate domain controllers, manage services, and direct user and computer authentication processes. By spoofing DNS records, an attacker could redirect AD processes to malicious servers, intercept sensitive information, or even gain unauthorized access to network resources.The primary risk of this vulnerability is that it allows attackers to perform man-in-the-middle attacks or impersonate legitimate network services. This can lead to data breaches, unauthorized access to sensitive information, and potentially full control over the AD domain. Detecting such attacks can be challenging because the malicious activities may appear as legitimate DNS updates. This makes it crucial for network administrators to monitor DNS records and DHCP logs closely for any unusual activities.
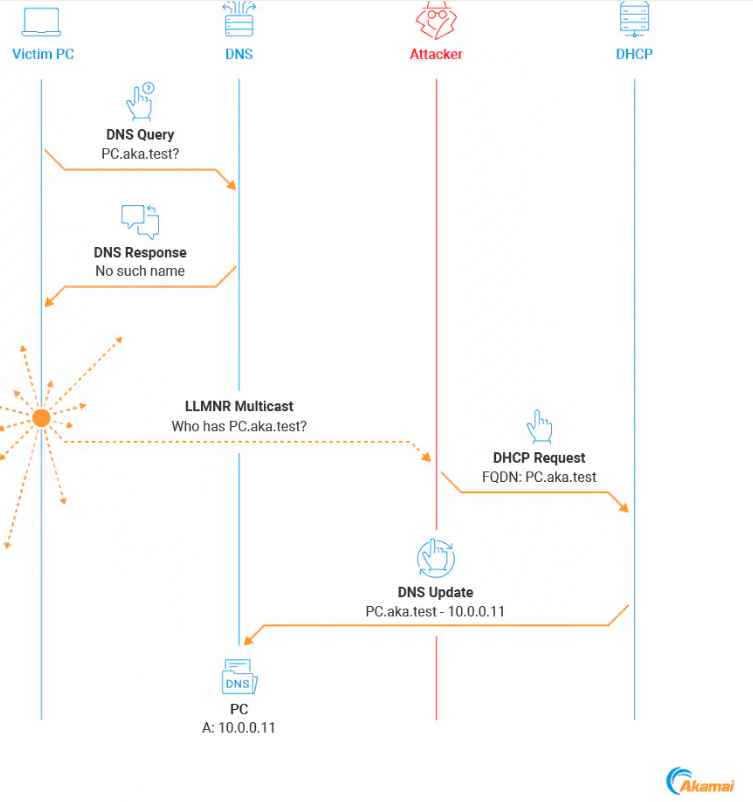
The Akamai blog post outlines several attack techniques exploiting DHCP DNS Dynamic Updates in Active Directory environments:
- DHCP DNS Spoofing: Attackers create non-existent DNS records using DHCP DNS Dynamic Updates, redirecting network traffic to their machine. DHCP DNS Spoofing involves an attacker leveraging the DHCP server to create false DNS records. Imagine a scenario where a computer asks the network for the address of a specific server (like asking for directions to a store). Normally, the network’s DHCP server gives the correct address. However, in this attack, the hacker tricks the DHCP server into giving out the hacker’s address instead. So when the computer tries to connect to that server, it actually connects to the hacker, unknowingly handing over sensitive information.
- Overwriting Existing Records: A technique where attackers attempt to overwrite existing DNS records via DHCP updates. Overwriting Existing Records involves an attacker changing an already existing DNS record to point to their own system. For example, let’s say a company’s computer regularly contacts a server named “companyserver.com” for updates. In this attack, the hacker modifies the DNS record for “companyserver.com” so that it now points to a server controlled by the hacker. When the company’s computer next tries to contact “companyserver.com”, it is unknowingly connected to the hacker’s server, potentially compromising sensitive information.
- Managed Record Overwrite: Specifically targets DNS records created by DHCP servers, exploiting their ownership settings. Managed Record Overwrite involves an attacker exploiting the fact that a DHCP server can create DNS records on behalf of clients. For example, if a non-Windows device joins a network, it might ask the DHCP server to create a DNS record for it. The DHCP server, being the owner of this record, can update it. An attacker, by manipulating the DHCP server, can overwrite this record with their own details, redirecting traffic intended for the original device to a system controlled by the attacker.
- DHCP Self-Overwrite: Involves the DHCP server overwriting its own DNS records, redirecting traffic meant for the server to the attacker. DHCP Self-Overwrite is an attack where the hacker manipulates a DHCP server to overwrite its own DNS record. For example, suppose a DHCP server is named “networkserver.com” and has a DNS record pointing to its IP address. In a self-overwrite attack, the hacker tricks the DHCP server into updating its DNS record so that “networkserver.com” now points to the hacker’s IP address. This redirection could allow the hacker to intercept or manipulate traffic intended for the DHCP server.
- DHCP DC Arbitrary Overwrite: If a DHCP server is installed on a Domain Controller, attackers can potentially overwrite any DNS A record in the Active Directory Integrated DNS zone. DHCP DC Arbitrary Overwrite occurs when a DHCP server is installed on a Domain Controller (DC) and the attacker manipulates it to overwrite any DNS record in the Active Directory Integrated DNS zone. For instance, if “companywebsite.com” is a DNS record in the zone, the attacker can make the DHCP server change this record to point to the attacker’s IP. This means anyone trying to access “companywebsite.com” within the network would be redirected to the attacker’s server.
- Bypassing Mitigations: Discusses ways to bypass Name Protection and other security measures implemented to prevent unauthorized DNS record modifications. Bypassing Mitigations in this context refers to circumventing security measures put in place to prevent unauthorized DNS updates. For example, an attacker might exploit weaknesses in the Name Protection feature of DHCP servers. Name Protection is designed to prevent unauthorized DNS record updates, but if an attacker can figure out the client’s unique identifier (like a MAC address), they can impersonate the client and change the DNS record. This could allow the attacker to redirect network traffic intended for a legitimate device to their own malicious server.
Mitigations
Mitigations for DHCP DNS attacks include disabling DHCP DNS Dynamic Updates if not needed, using weak user credentials for DNS updates, enabling Name Protection, and avoiding the use of the DNSUpdateProxy group. However, attackers can bypass these mitigations, such as exploiting the lack of authentication in DHCP DNS Dynamic Updates or finding ways to impersonate legitimate network clients. Akamai recommends implementing mitigation strategies until a patch is available from Microsoft. However you can do the following meantime.
- Regularly Update and Patch Systems: Ensure that all systems, especially those related to DHCP and DNS services, are regularly updated and patched. This helps in fixing known vulnerabilities that could be exploited.
- Monitor Network Traffic: Implement robust monitoring of network traffic, particularly focusing on DHCP and DNS communications. Unusual patterns or anomalies could indicate attempts at exploitation.
- Restrict Dynamic DNS Updates: Configure systems to restrict dynamic DNS updates. This can be done by allowing only authorized DHCP servers to update DNS records.
- Implement DNSSEC: Deploy DNS Security Extensions (DNSSEC) to protect against DNS spoofing. DNSSEC adds an additional layer of security by validating the authenticity of the DNS data.
- Enhanced Access Controls: Strengthen access controls to critical network infrastructure. Limiting access to DHCP and DNS configurations to only those who require it can reduce the risk of internal threats.
- Regular Audits and Compliance Checks: Conduct regular audits of network configurations and compliance checks to ensure that security measures are up-to-date and effective.
- Employee Training and Awareness: Educate staff about the risks associated with DNS spoofing and the importance of following security protocols.
- Incident Response Plan: Have a well-defined incident response plan in place to quickly address any breaches or exploits that occur.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
