Internet Protocol (IP) is the protocol that the vast majority of networked devices use in order to communicate. IP version 6, often known as IPv6, is the most recent version of the Internet Protocol (IP), and it has many benefits over its predecessor, IP version 4. (IPv4). Most importantly, the address space provided by IPv4 is insufficient to handle the growing number of networked devices that require routable IP addresses, while IPv6 offers a wide address space that can fulfill both the demands of today and those that may arise in the future.
Although IPv6 will have a greater impact on some technologies, such as network infrastructure, than it will have on others, almost all pieces of networked hardware and software will be impacted in some manner. As a consequence of this, IPv6 has a wide range of effects on cybersecurity, all of which should be addressed by businesses with the utmost care.
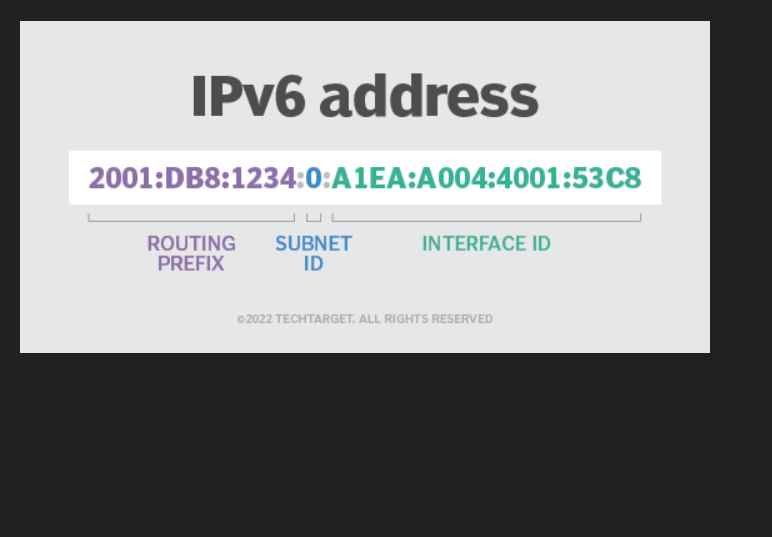
IPv6 security concerns are quite comparable to IPv4 security concerns. That is, the security procedures that are used with IPv4 should normally be used to IPv6, with changes made as necessary to handle the variations that are present in IPv6. In most cases, networks that are new to IPv6 or those that are in the beginning stages of the transition to IPv6 are the ones that will experience the first security problems connected with an IPv6 implementation.
These networks are not mature in terms of their IPv6 setups and the technologies used for network security. Most significantly, they do not have sufficient general expertise in the IPv6 protocol among their administrators. Due to the expanded attack surface that comes with having both IPv4 and IPv6, dual-stacked networks, which run both IPv4 and IPv6 concurrently, have extra security problems. As a result, additional countermeasures are required to reduce these risks in order to keep users safe.
The overall network security is heavily influenced by the network design as well as the competence of individuals who setup and operate an IPv6 implementation. As a direct consequence of this, the real security posture of an IPv6 implementation might differ from instance to instance.
Security problems about IPv6 and some suggestions
The following is what the National Security Agency (NSA) suggests you do to get off to a good start with installing IPv6 networks and the possible security risks they present:
Auto-configuration
Stateless address auto-configuration, often known as SLAAC, is an automated approach that allows a host to auto-assign itself an IPv6 address. It may be preferable to use static addresses in certain circumstances, such as when configuring essential servers; nevertheless, it is often simpler to enable devices to automatically self-assign or request an IPv6 address in a dynamic manner. Examples of such circumstances include: A host in SLAAC is responsible for configuring its own network address by using a network prefix that was obtained from a router. The media access control (MAC) address information is taken from the network interface and is included into the issued IPv6 address. This may make it possible for the host to be identified using the interface ID, the network interface card, or the host vendor. This raises privacy problems since it allows motions to be linked to a particular item and allows one to infer the identity of a person who is affiliated with that equipment. Additionally, it reveals the sorts of devices that are used inside a network.
The National Security Agency (NSA) suggests using a Dynamic Host Configuration Protocol version 6 (DHCPv6) server to provide IP addresses to hosts as a solution to the SLAAC privacy problem. This problem may also be solved by using a randomly generated interface ID, as described in RFC 4941: Privacy Extensions for Stateless Address Auto-configuration in IPv6 which changes throughout the course of time, making it impossible to link activity while yet providing network defenders the visibility they need
Automatic tunnels
Tunneling is a transition mechanism that enables one protocol to be transferred, or tunneled, into another protocol. Tunneling may be done within another protocol. For instance, one may use a tunnel to move IPv6 packets inside of IPv4 packets while they are being transported. Tunneling might be the method that a network employs in order to connect to the Internet. Additionally, some devices and applications could be built to tunnel IPv6 data. When a client connects to a server, some operating systems may automatically construct an IPv6 tunnel. This might result in an unwelcome access point to the host.
If transition tunnels are not necessary, the National Security Agency (NSA) advises eliminating tunnels altogether to cut down on complexity and the attack surface they provide. Configure the security devices that are placed around the perimeter to detect and prevent the usage of tunneling protocols as transition mechanisms. In addition, it is recommended that tunneling protocols such as 6to4, ISATAP, Teredo, and others be disabled on all devices whenever it is feasible to do so. Tunneling protocols may be permitted if doing so is necessary during a transition; nevertheless, their use should be restricted to just those systems that have been pre-approved, during which their use can be easily comprehended and in which they are expressly set.
Dual stack
There is said to be a dual stack environment present when devices concurrently execute both the IPv4 and IPv6 protocols. This is the strategy that is recommended for phased IPv6 deployment; nevertheless, it may be more costly and typically results in an increase in the attack surface. This method provides a transition method to IPv6 because it enables devices to use IPv6 for communications that support IPv6 while maintaining the ability to use IPv4 for communications that do not support IPv6. In other words, it allows devices to use IPv6 for communications that support IPv6 while maintaining the ability to use IPv4 for communications that do not support IPv A dual stack environment will migrate to IPv6-focused operations as IPv6 deployments rise. This will be accomplished by increasing the usage of IPv6 while simultaneously lowering the use of IPv4.
Organizations should build IPv6 cybersecurity methods that reach parity with existing IPv4 mechanisms or better before adopting a dual stack network. A matching security mechanism has to be built for IPv6 for any security mechanism that is established for IPv4, and the IPv6 mechanism needs to address any differences that are specific to IPv6. [5] For instance, rules for the firewall that filter higher-level protocols (like TCP or UDP, for instance) should be implemented to the IPv6 and IPv4 protocols simultaneously. There are a lot of current network security techniques that support both IPv4 and IPv6, but managers need to make sure that individual products are compatible with each other. In addition, additional transition techniques like tunneling and translation need to be avoided at this stage of the transition plan since the added complexity they bring to both transport and cybersecurity should be avoided.
Hosts that include more than one IPv6 address
IPv6 allows many network addresses to be issued to a single interface, in contrast to IPv4’s single-address model.
When compared to having a single address, having many addresses results in a larger attack surface. The process of generating filtering rules or access control lists (ACLs) might be difficult at times. In order for it to be successful, it is necessary for firewalls and other intermediary security devices to have complete awareness of all of the addresses.
Review the Access Control Lists (ACLs) very carefully to verify that they are set to reject all traffic by default. This will guarantee that only traffic coming from authorized addresses will be allowed via the firewalls and any other security devices. Make sure that every bit of traffic is recorded, and check the logs on a regular basis to check that the regulations of the company are being followed by the traffic that is permitted.
IPv6 training
A basic understanding of the ways in which IPv4 and IPv6 function, in addition to the distinctions between the two protocols, is a bare minimum need for properly securing an IPv6 network. The absence of this information may result in IPv6 setups that are incorrect. IPv6-enabled devices that have been improperly setup (as a consequence of a mistake in the configuration) may expose vulnerabilities, hence making the devices more susceptible to being compromised.
The most important things to do in order to maintain and improve IPv6 security on a network are to get familiar with the IPv6 protocol and to have a good understanding of how to successfully setup IPv6. The National Security Agency (NSA) suggests making it a requirement that all network administrators have enough knowledge and training in order to effectively run IPv6 networks.
Although there are compelling arguments in favor of making the switch from IPv4 to IPv6, security is not the primary reason for doing so. There are security concerns associated with IPv6 and they will be faced; nevertheless, these risks need to be addressed by a mix of configuration advice that is rigorously implemented and training for system owners and administrators throughout the transition. The following is a list of additional things to keep in mind while trying to protect IPv6 networks, in addition to the possible security vulnerabilities that were discussed earlier:
Use split domain name system (Split DNS)
A new AAAA record that gives IPv6 addresses has been added to the Domain Name System (DNS), which provides IPv6 addresses in addition to the A record that provides IPv4 addresses. This expansion was made for IPv6.
As a consequence of this, an implementation of a dual stack DNS could need to handle both A and AAAA entries. There is the potential for sensitive information to be included in the AAAA records for internal hosts as a result of SLAAC and other processes. A Split DNS configuration utilizes two distinct DNS servers, one for the external network and one for the internal network. These servers are configured for the same domain. The purpose of a split DNS, as opposed to a single DNS, is to increase both security and privacy by preventing the accidental disclosure of sensitive information contained within a DNS record that is sent from an internal network to an external network. This is accomplished by separating the internal network from the internet. The NSA suggests use split DNS for both IPv4 and IPv6 network configurations.
Filter IPv6 traffic (boundary protection)
It is recommended that IPv6 traffic be filtered in accordance with the network regulations of the company. Any IPv6 traffic, including IPv6 that is tunneled in IPv4, should be blocked at the network border by a network that has not yet implemented IPv6. A network that has implemented IPv6 should only admit IPv6 traffic that is approved by policy. Authorization control lists (ACLs) should only allow authorized flows and protocols, and they should block all other traffic by default. Even though the IPv6 filtering policy could be modeled after an existing IPv4 policy, the IPv6 policy need to take into account problems that are unique to IPv6. In addition, the strategy for filtering should take into account the fact that the Internet Control Message Protocol for IPv6 (ICMPv6) is more vital to communications over IPv6 than its counterpart, the ICMP for IPv4.
Even though the matching message in ICMP for IPv4 is being blocked, some ICMPv6 messages, such as neighbor discovery and router advertising, may need to be allowed.
Keep the local connection secure
IPv6 outlines the operations of a network that are carried out on the local connection. Address resolution at the link layer, detection of routers, and stateless auto-configuration of addresses are all included in this category. IPv6 has more complicated local-link procedures than IPv4, which results in a larger attack surface. As a result, any appropriate preventative measures (such as the Router Advertisement (RA) Guard), Dynamic Host Configuration Protocol for IPv6 (DHCPv6) Shield could be considered to guard against rogue RA messages to protect against rogue DHCPv6 servers given by switches and routers.
Avoid doing anything that involves network address or protocol translation
IPv6-only networks will probably implement translation in order to communicate with other networks that do not yet support IPv6, such as NAT64/DNS64 (Network Address Translation between IPv6 hosts and IPv4 servers and synthesizing DNS AAAA records from A records) or 464XLAT (translation between IPv4 private addresses, IPv6 addresses, and IPv4 global addresses). The number of installations that utilize solely IPv6 will rise, which will lead to a reduction in the need for translation. Eventually, the translation functions won’t be needed at all and will be able to be deleted.
In general, address translation should not be employed; the only exceptions to this rule are IPv6-only networks that make use of NAT64/DNS64 or 464XLAT . A significant number of IPv4 networks, in particular, make use of NAT, more especially NAT44, in order to translate between internal and external addresses. On the other hand, IPv6 networks ought to make use of global addresses on all of the systems that call for external connections, and they ought to make use of non-routable addresses inside the network itself. Any system that has to communicate with the outside world need to have a global address in addition to its unique local address, in the event that internal systems employ unique local addresses .
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
