The $2 Chip That Can Hack the World: ESP32 Bluetooth Backdoor Exposed!”
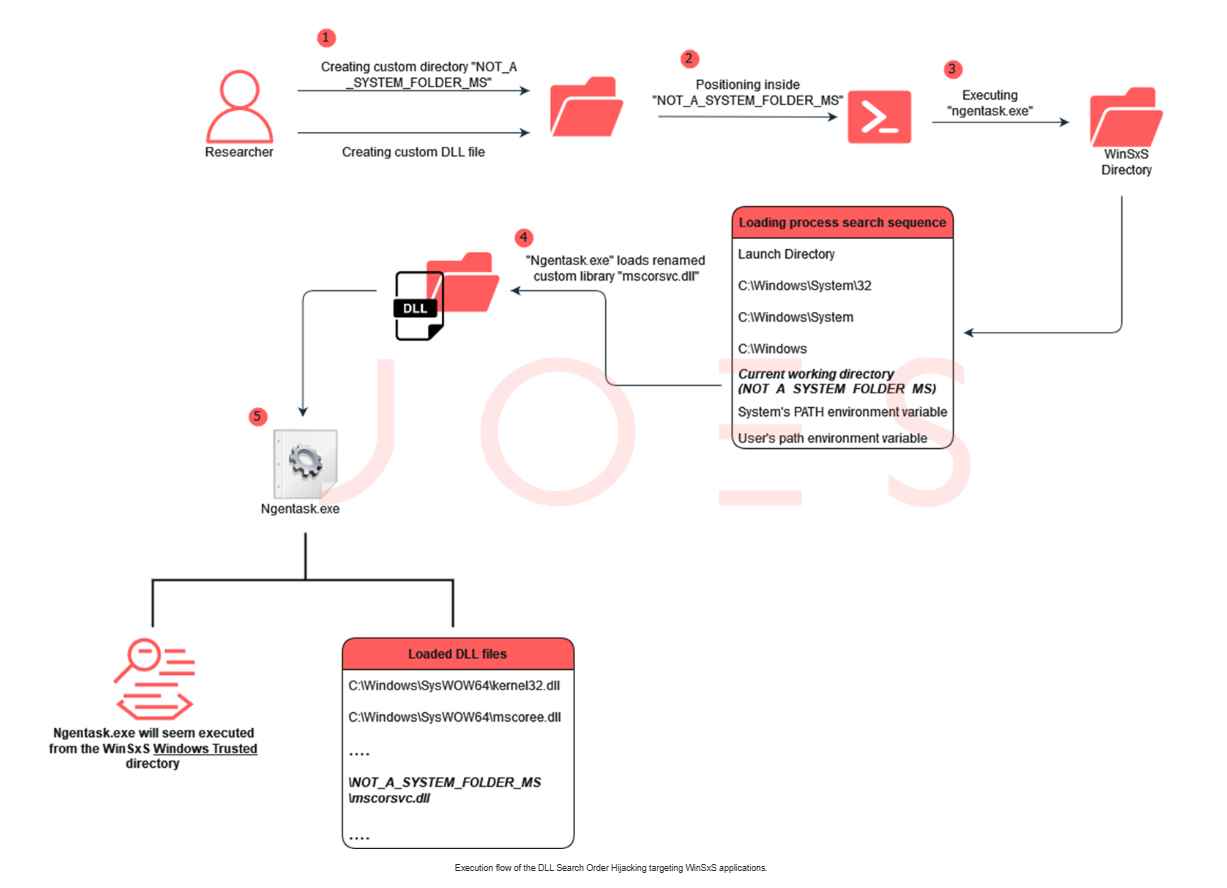
A newly discovered set of undocumented commands in the widely used ESP32 microcontroller has raised significant cybersecurity concerns, with potential risks spanning consumer electronics, industrial control systems, and critical infrastructure.Read More →