A critical vulnerability identified as CVE-2023-45866, along with CVE-2024-21306, has been discovered in the Bluetooth technology used across various operating systems, including Android, Linux, macOS, iOS, and Windows. This flaw, which exploits an “unauthenticated pairing mechanism” in the Bluetooth specification, allows attackers to connect to a device as a Bluetooth keyboard without the user’s consent or knowledge.
The Nature of the Vulnerability
The vulnerability lies in the way Bluetooth handles pairing, specifically the unauthenticated pairing mechanism. This loophole enables an attacker within Bluetooth range to connect to a device by masquerading as a Bluetooth keyboard. The attacker can then execute arbitrary commands, install applications, and control the device without any physical interaction or alert to the user.
Discovery and Impact
The vulnerabilities were uncovered by security researcher Marc Newlin, who also provided proof-of-concept exploitation scripts available on GitHub. These scripts enable attackers to inject keystrokes into any unpatched Android and Linux device within Bluetooth range by impersonating a Bluetooth keyboard. This type of attack forces a targeted device to pair with the malicious keyboard without any user interaction or notification, making it a 0-click exploit.
Vulnerable Devices
The list of affected operating systems is extensive. Notably, Android versions up to 10 are vulnerable, with no fix currently available. For Android versions 11 and above, the vulnerability is addressed in the 2023-12-05 security patch. Linux distributions using BlueZ, macOS versions 12 and 13, iOS 16, and Windows versions 10, 11, and Server 2022 are also impacted, with varying degrees of patch availability.
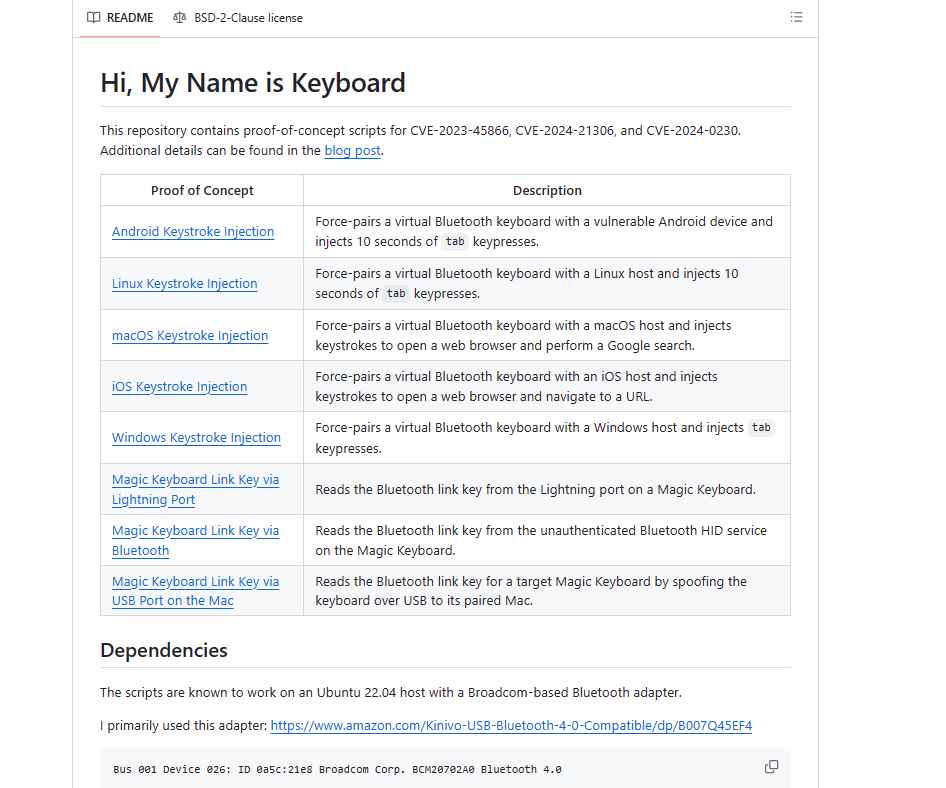
Exploitation Prerequisites and Methodology
To exploit an unpatched Android device, an attacker would typically use a rooted Android smartphone with a custom NetHunter Kernel supporting Bluetooth scanning. The attacker first needs to discover the target device’s Bluetooth MAC address. This is possible when the target device is in discoverable mode, which is usually activated when a user opens Bluetooth settings.
Once the MAC address is obtained, the attacker can use the keystroke-injection-android-linux.py script to inject keystrokes. The script requires specifying the Bluetooth interface and the target’s MAC address. By default, it injects a series of Tabulator key presses.
The exploitation technique for the 0-click Android Bluetooth vulnerability, as outlined in the Mobile Hacker article, involves several key steps. This technique allows an attacker to inject keystrokes into a vulnerable Android device without the need for pairing. Here’s a step-by-step breakdown:
Step 1: Preparation and Prerequisites
- Attacker’s Device Setup:
- The attacker uses a rooted Android smartphone. In the article, a OnePlus 7 Pro flashed with a custom NetHunter Kernel supporting Bluetooth scanning is mentioned. This kernel is crucial as it allows the device to perform the necessary Bluetooth operations.
- Alternatively, an external Bluetooth dongle connected to the Android device via an OTG adapter can be used, provided the kernel supports it.
Step 2: Discovering Target Devices
- Enabling Discoverable Mode on Target:
- For the attack to be successful, the target Android device must be in discoverable mode. This mode is typically activated when a user accesses Bluetooth settings on their device.
- In discoverable mode, the device broadcasts its Bluetooth MAC address, making it visible to nearby devices, including the attacker’s.
- Scanning for Devices:
- The attacker uses the ‘Bluetooth Arsenal’ menu in Kali NetHunter to scan for nearby Bluetooth devices. This step is crucial to find the target device and obtain its Bluetooth MAC address.
Step 3: Exploitation
- Cloning Exploitation Scripts:
- The attacker clones the exploitation scripts from Marc Newlin’s GitHub repository using the command:
git clone https://github.com/marcnewlin/hi_my_name_is_keyboard.git.
- The attacker clones the exploitation scripts from Marc Newlin’s GitHub repository using the command:
- Installing Required Libraries:
- The
pydbuslibrary is required for the script to run. It can be installed using the command:pip3 install pydbus.
- The
- Running the Exploit Script:
- The attacker navigates to the cloned directory and runs the
keystroke-injection-android-linux.pyscript. - The script requires specifying the Bluetooth interface (internal
hci0or externalhci1) and the target’s MAC address. - By default, the script injects a series of Tabulator key presses.
- The attacker navigates to the cloned directory and runs the
Step 4: Injecting Keystrokes
- Execution of the Attack:
- Upon running the script with the correct parameters, keystrokes are injected into the target device. This can result in various actions depending on the keystrokes sent.
Step 5: Potential Device Takeover
- Installing Malicious Payloads:
- The vulnerability can be further exploited to take over the target device by remotely installing spyware or other malicious applications.
- This involves opening a browser on the target device, downloading, installing, and executing a payload, all done over Bluetooth without any user interaction.
Potential for Device Takeover
This vulnerability can be exploited to take over a targeted device by remotely installing spyware applications. An attacker could open a browser on the target device, download, install, and execute a payload that backdoors the smartphone over Bluetooth without any user interaction.
Mitigation and Safety Measures
For Android users running version 11 or higher, applying the 2023-12-05 security patch is crucial. Users with Android 10 or below are advised to turn off Bluetooth, especially if the device is in discoverable mode, to mitigate the risk of Bluetooth attacks. Keeping devices updated and avoiding unnecessary pairing or discoverable modes are key to staying safe from such vulnerabilities.
The discovery of the 0-click Android Bluetooth vulnerability highlights the ever-present need for vigilance in the digital world. It underscores the importance of regular software updates and cautious use of Bluetooth functionalities to protect against such sophisticated cyber threats.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
