In order to avoid being discovered, hackers used a novel technique that they named “MalDoc in PDF” to embed a malicious Word file inside of a PDF document.
A file that was generated using MalDoc in PDF may still be opened in Word, despite the fact that it contains magic numbers and uses a file format that is unique to PDF.
If the file has a macro that has been configured, opening it in Word will force VBS to start and carry out any malicious activities that have been set for it.
The “.doc” file extension was used in the attacks that were reported by JPCERT/CC. The MalDoc that was embedded in the PDF file that was produced will open in Word if Windows is configured to recognize the “.doc” extension as being connected with Word.
The dump view of the file that was generated by this method is seen in Figure 1. The adversary follows the PDF file object with an MHT file that was made in Word and has a macro connected to it before saving the document. The document that was prepared may be opened in Word in addition to being recognized by the file signature as being in PDF format.
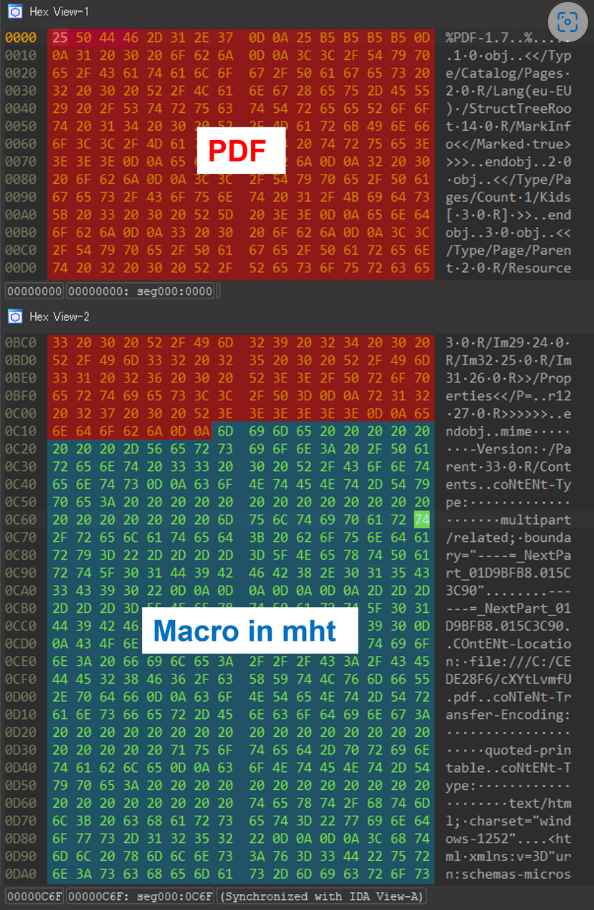
As can be shown in Figure 2, there is a strong probability that PDF analysis tools such as pdfid[1] would be unable to identify any malicious components inside a PDF file that was made using MalDoc. In addition, it is important to note that when this file is viewed in Word, it exhibits behaviors that were not intended, yet when it is opened in PDF readers, etc., it is impossible to determine whether or not it exhibits harmful behaviors. In addition, given that the document may be identified as a PDF file, it is possible that sandbox or antivirus software already in use would not identify it.
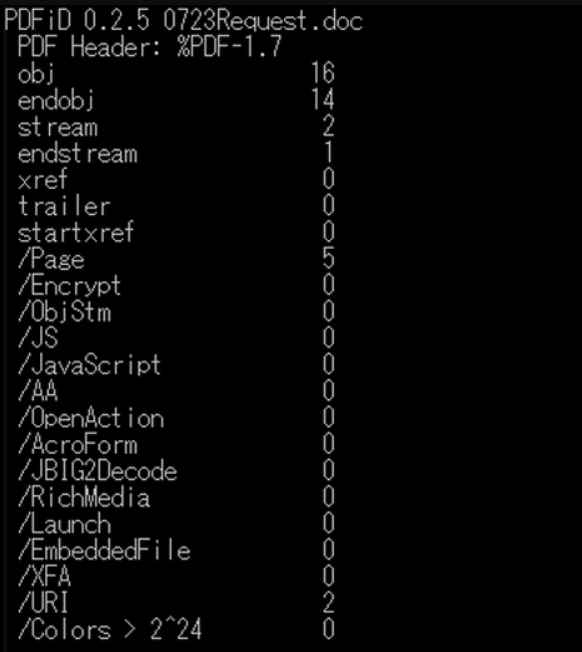
The method that is outlined in this piece is not capable of getting around the setting that inhibits auto-execution in Word macro. However, due to the fact that the files are identified as PDFs, you should be cautious of the detection findings if you are undertaking automated malware analysis using certain tools, such as a sandbox or similar environment.
However, JPCERT states that other analysis tools such as ‘OLEVBA’ may still identify the malicious information lurking within the polyglot, which indicates that multi-layered defenses and extensive detection sets should be successful against this threat.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
