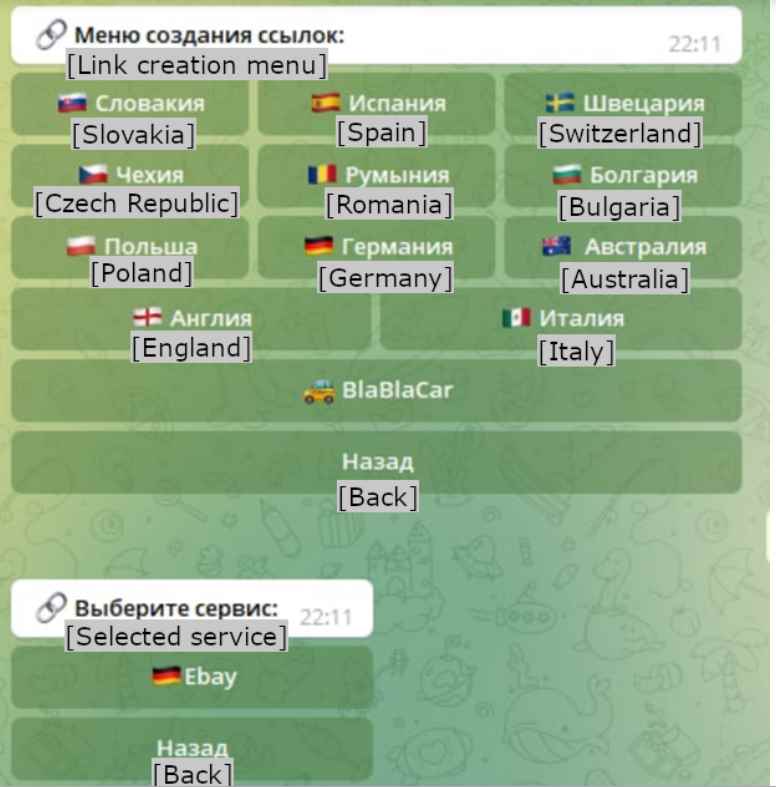
This telegram bot is like ChatGPT for scammers to steal money from victims easily
A recently launched enterprise driven by financial gain is using a malicious Telegram bot to assist threat actors in defrauding unsuspecting victims. The criminals referred to prospective victims as MammothsRead More →