Imagine that you get an email from DocuSign, which is a reputable and well-known electronic signature platform. If you clicked on the link in the email, you would most likely have a pleasant and secure experience, right? Users of DocuSign were the victim of a recent brand phishing attack, and unfortunately, the perpetrators of the attack were banking on precisely this kind of vulnerability.
The victims were supposed to feel a feeling of urgency by reading the subject line of the email, which read as follows: Please DocuSign: Approve Document 2023-01-11. The use of the term “Approve” inside the subject line of the email gives the impression that the receiver is expected to take some kind of prompt action in response to the message. The email attack made it seem as if the document being sent through was brand new and required inspection so as to increase the likelihood that the recipient would open the email. In order to do this, the malicious sender included the time and date that the email was sent inside the subject line (January 11, 2023 at 11:01 AM; although experts believe the time stamp was coincidental).
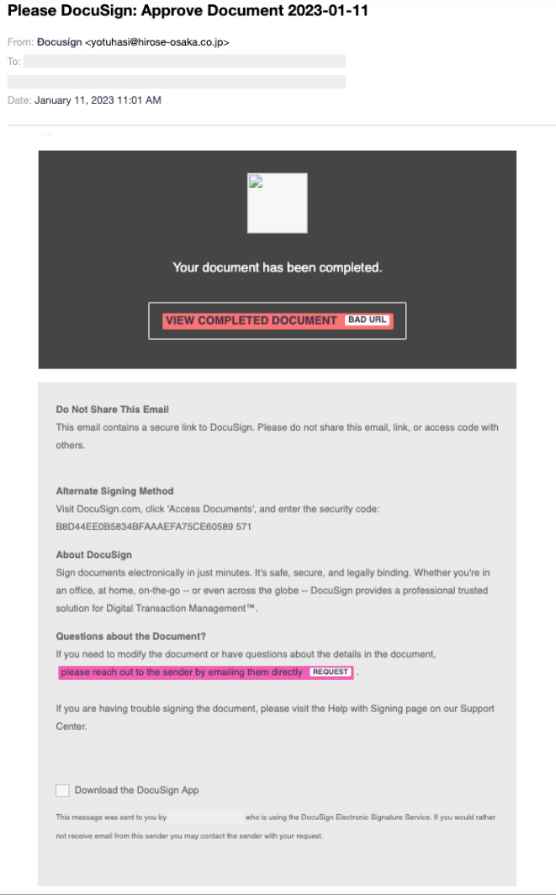
At first look, the email seems to be a genuine message from DocuSign; however, the sender identity has been spoofed by the malicious actor who is reading Docusign. The body of the email continues to make an attempt to spoof the well-known brand DocuSign via the terminology that is utilized. Unsuspecting victims who fell for the manipulative techniques of the attackers and opened the email would have been provided with extra language and material designed to generate confidence in the victims and persuade them to click on the primary link that reads: VIEW COMPLETED DOCUMENT. For example, the attackers may have included words about different shipping ways, a paragraph about the organization DocuSign, and even a disclaimer to not share this email with anyone else.
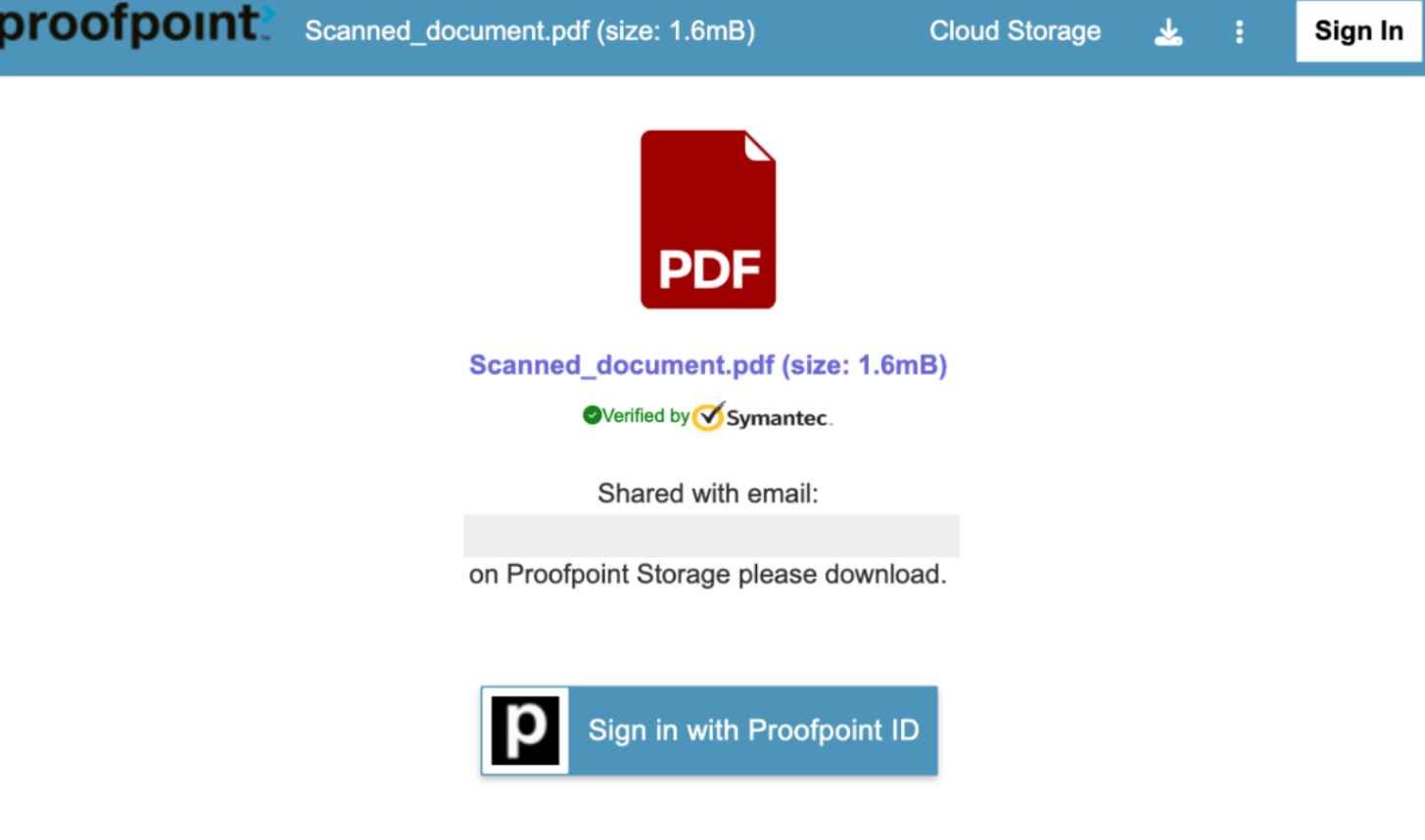
Users on the receiving end are unable to detect the fact that this button led to a broken URL due to the blind eye. When users clicked on the malicious link, they were sent to a phony landing page that was made to seem like a Proofpoint Storage application. The phony landing page included Proofpoint branding and displayed an icon in the form of a PDF document that was supposed to represent the finished document that the victim was supposed to read. When crafting this spoofed page, the attackers’ primary objective was to win the victims’ trust. To that end, they included a preview of the document file name and size, a checkmark indicating that the file had been verified by Symantec, and the victim’s email address in order to continue validating that this file was intended to be viewed by that particular person. All of this is done with the intention of persuading victims to sign in with their Proofpoint ID, inadvertently supplying the attacker with sensitive user login information.
The objective is to steal sensitive information, such as login passwords. According to the specialists at Armorblox who reported this attack, the brand impersonation attack circumvented native cloud and inline email security systems and targeted over 10,000 end users across several enterprises.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
