Threat actors could exploit a critical zero-day vulnerability in Windows Search to run remotely hosted malware just by automatically opening a search window with a Word document. According to the report, the flaw can be exploited because Windows supports a URI protocol driver called ‘search-ms’, which allows applications and HTML links to initiate custom searches on the system.
Although searches on the Windows system will scan the index of the local device, it is also possible to force the Windows Search function to query file shares on remote hosts, using a custom title for the search window.
An example of this is the popular Sysinternals toolset, which allows you to remotely mount live.sysinternals.com as a network share to start its utilities. To search for this share and list only the files that match a particular name, the ‘search-ms’ URI can be used:
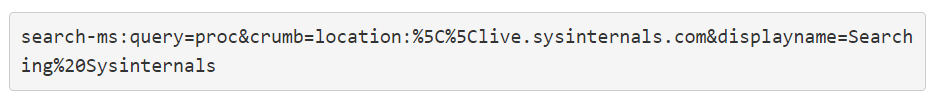
In this command, the search-ms ‘crumb’ variable specifies the location to search, while ‘displayname’ specifies the search title. A custom search window will appear when you run this command from a Run dialog box or from the web browser’s address bar in Windows 7, Windows 10, and Windows 11:
The window title is set to the display name ‘Searching Sysinternals’, specified in the search-ms URI. A malicious hacker could use this approach for attack scenarios, sending phishing emails that hide malware disguised as system updates.
Although it may sound relatively simple, the attack becomes complex considering how uncommon it is for users to click on a URL like this. However, researcher Matthew Hickey found a method to exploit the flaw in combination with another recently detected vulnerability in the Microsoft Support Diagnosis Tool (MSDT).
Employing the proof of concept developed by Hickey, when you open a Word document, a ‘search-ms’ command will be automatically launched to open a Windows search window that lists the executable files on a remote SMB share. Hackers can customize this share with any name, making the process of tricking the user easier.
Like the MSDT vulnerabilities, Hickey also demonstrated that RTF versions can be created that automatically open a Windows search window when the document is rendered in the Explorer preview pane.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
