A sophisticated phishing tool called SquarePhish employs a method that combines QR codes with the OAuth Device code authentication procedure.
A malicious QR code email may be sent to a target by an attacker using SquarePhish’s email module. The standard excuse is that in order to keep using mobile email, the sufferer must upgrade their Microsoft MFA authentication. The Microsoft Authenticator App is the current client ID in use.
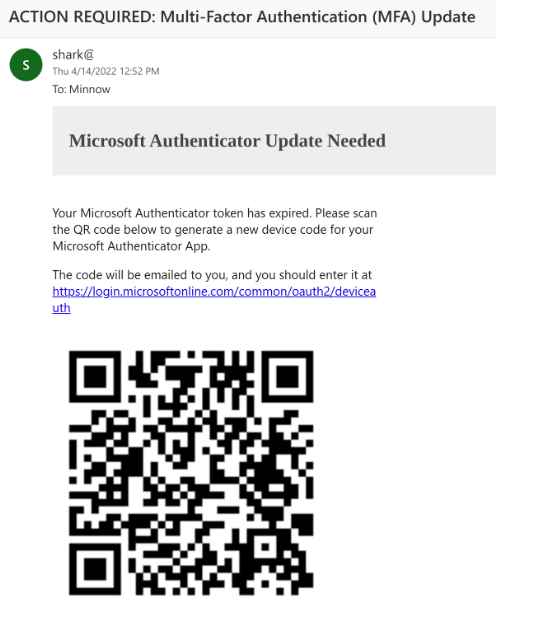
The victim will next use a smart phone to scan the QR code contained in the email body. The victim will be sent via the QR code to the attacker’s server, which is running SquarePhish‘s server module, with a URL parameter set to their email account.

A secondary process is started when the victim accesses the malicious SquarePhish server, starting the OAuth Device Code authentication procedure and emailing the victim a produced Device Code that must be entered into the genuine Microsoft Device Code webpage (this will start the OAuth Device Code flow 15-minute timer).
The victim will then access the SquarePhish URL on their smart phone, click the link in the email, or receive a redirect to the Microsoft Device Code authentication site.
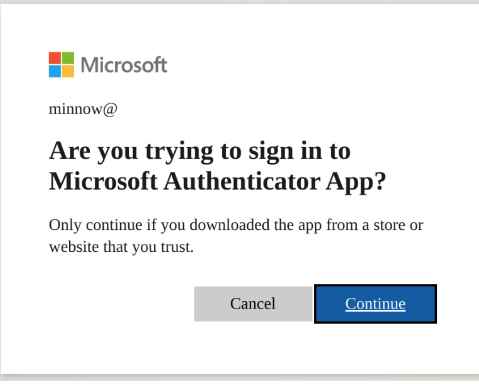
The victim will then be asked for permission after entering the given Device Code. Once the victim has authenticated and given permission, an authentication token is kept locally and will grant the attacker access via the requested application’s specified scope.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
