A worrying number of cybercriminal campaigns occur with no indication of those responsible for these online crimes, especially those with financial motivations. However, in some cases, threat actors leave enough evidence to find their identity, or at least create a trace of the origin of the attack.
Recently PIXM researchers found a slight trace of a campaign for the collection of Facebook credentials, active since the end of 2021. Thanks to the analysis of these “breadcrumbs”, the experts managed to identify a massive and complex cybercriminal operation, in what they described as a state of evolution of phishing websites.
Technical analysis
It all started with the detection of a fake Facebook login page, which grew in its volume of visits until it peaked between April and May 2022. In the following screenshot we can see how this fraudulent platform is identical to the legitimate login on the social media platform:
The PIXM team analyzed the code of this portal, making a couple of interesting findings:
- A reference to the actual server hosting the database server to collect credentials entered by users on a redirection network
- A link to a traffic monitoring application. The tracking metrics of this service can be viewed without the need for authentication, which allowed seeing traffic data from this portal and many other phishing websites
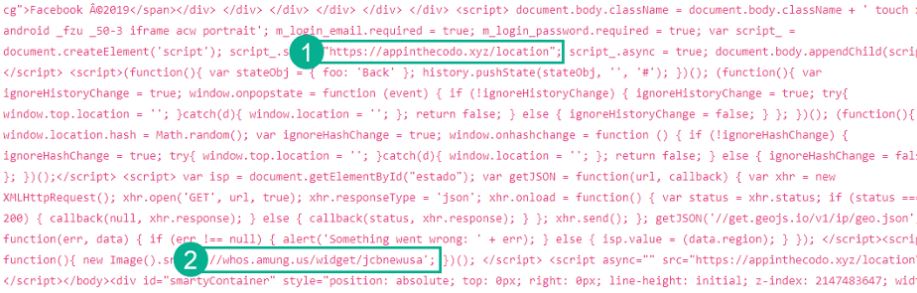
In this structure only one change in the HTML of each page was observed; the name of the server referenced in “http://appinthecodo.xyz/location”, and the username that will follow the traffic control URL, “//whos.amung.us/widget/*username*”.
Although Facebook’s security teams are trained to detect this kind of malicious behavior, the operators of this campaign employed a technique to prevent their URLs from being blocked. To do this, they used fully legitimate application deployment services to be the first link in the redirect string once the user clicked on the link; subsequently, users would be redirected to a phishing website, associated with a URL created using a legitimate service that Facebook could not completely block without disrupting other legitimate services as well.
Hackers abused popular services such as glitch.me, celebrity.co, or amaze.co, employed to deploy and generate full legitimate application URLs. An example of a URL resulting from using this method is “my.famous.co/*User ID*”. When Facebook’s automated security systems came to detect and block a URL like this, another URL with a new ID simply appeared, sometimes several times a day.
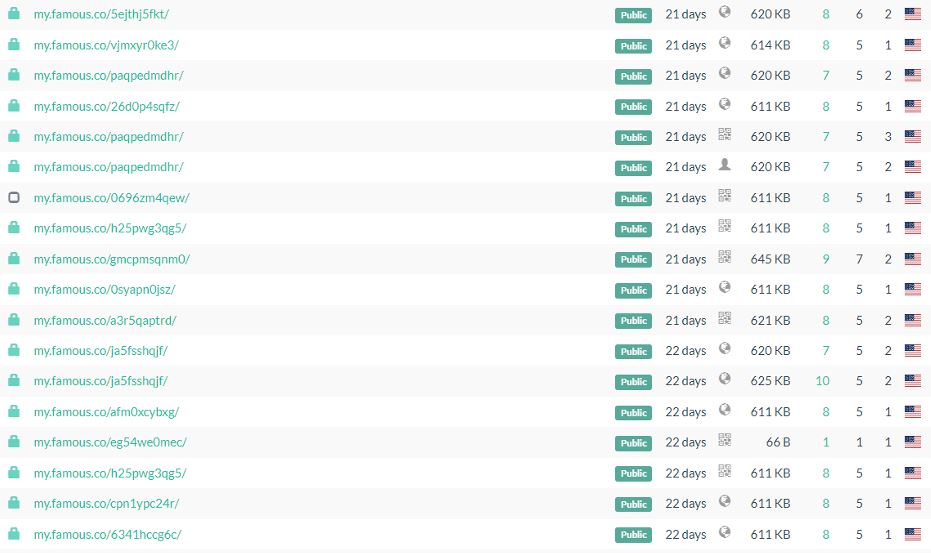
In this way, threat actors were able to continue operating their campaign undetected for months.
Large-scale attack
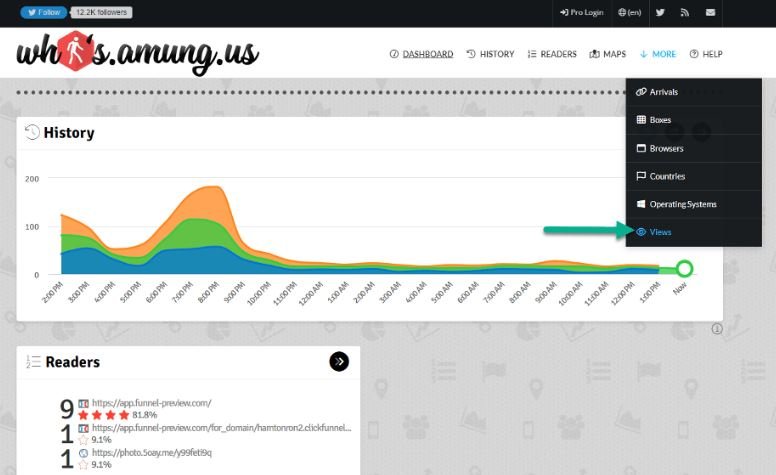
PIXM analyzed whos.amungus.us, the traffic monitoring application used by hackers, to determine the scale of the attack. Experts searched the HTML code for a reference to a whos.amungus.us username, finding that they could access users’ control panel simply by navigating to amung.us/stats/username.
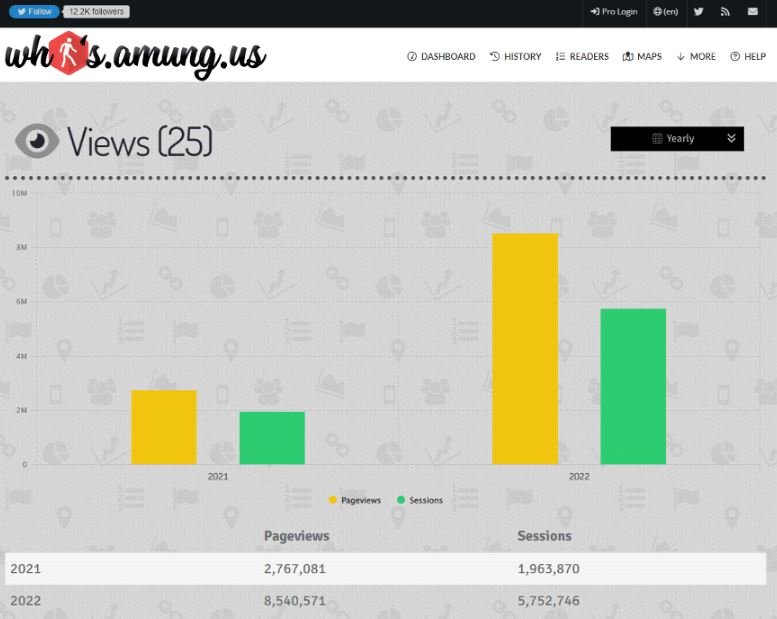
By visiting one of these URLs, the researchers accessed the active sessions in “Readers” on websites that use this tracking code and the actual URLs those sessions are in. Statistics are available on the “Views” page.
According to the analysis, 2.7 million users visited some of the fraudulent pages in 2021, while so far in 2022 8.5 million visits have been detected.
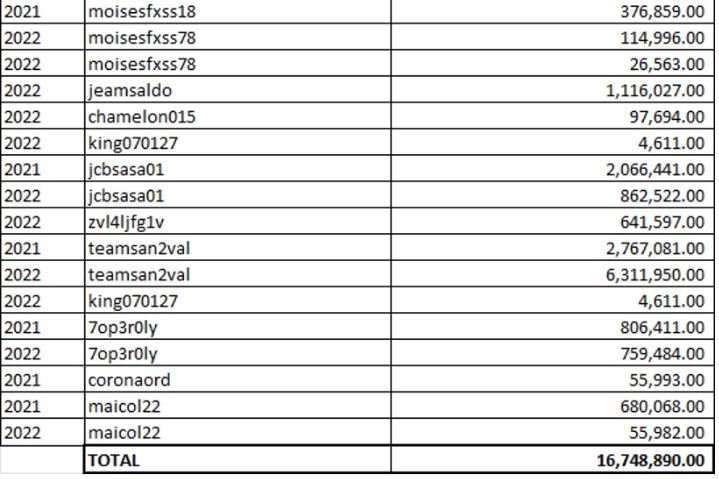
Some 400 unique usernames, all connected to different Facebook phishing homepages, have been associated with the same campaign. Using a sample of 17 random usernames, the researchers concluded that these platforms have received an average of 985,288 visits.
A few months ago, an investigator managed to contact an alleged member of this operation, who says he earns about $150 for every thousand visits to these platforms, equivalent to almost $60 million. Although the alleged hacker’s calculation might be exaggerated, it is undeniable that the actors behind this campaign are generating considerable illicit income.
The gains in this scheme come from a combination of tracking tools and redirects to invasive or malicious advertising platforms.
Who is behind this campaign?
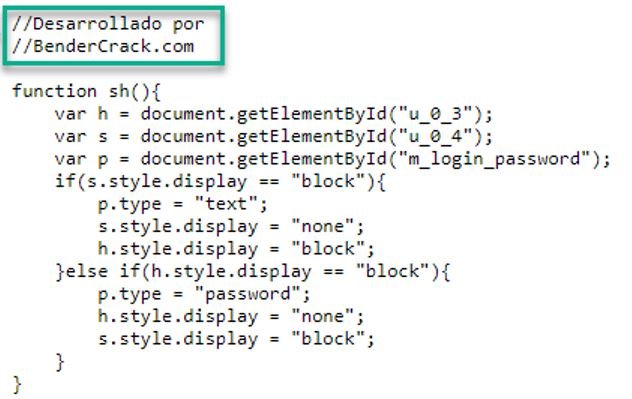
Virtually every page in the redirect infrastructure shares the same “Desarrollado por Bendercrack.com” code snippet (Spanish for “developed by Bendercrack.com”), shown in the following screenshot:
When visiting this platform, the researchers found the following message:
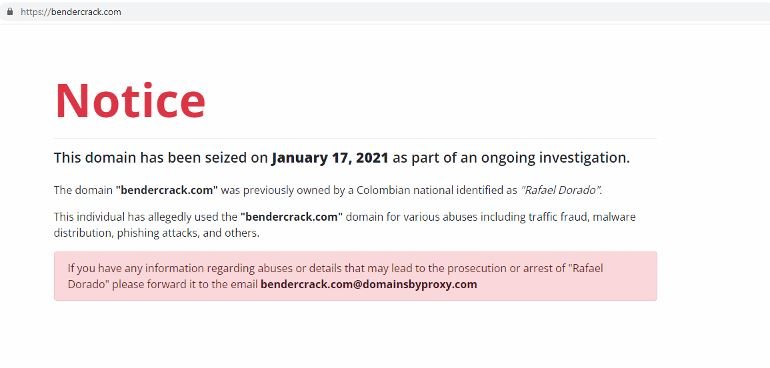
Archived copies of this platform even show a phone number as the owner’s contact information.
Performing a reverse search of this phone number, some websites related to an email address (rafaeldorado001@gmail.com) were discovered. Thanks to this, it was discovered that behind the campaign were several legitimate web development businesses in Colombia, also discovering that the main operator of the attack is known by the aliases “developerdorado” and “hackerasueldo”.
Although virtually complete identity records were found about this individual, that information was properly shared with local law enforcement and Interpol representatives.
Using legitimate services to bypass URL blocking mechanisms is becoming a very common cybercriminal practice, as it is highly evasive and relatively easy to implement. Most security services in web domains are based on the analysis of suspicious properties, so they are not functional for the detection of a campaign like this.
Faced with such security risks, online platforms would have to adopt new approaches to detecting similar practices, preventing redirection networks, and the use of legitimate services for malicious purposes.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
