The internet is rife with fraudulent websites posing as legitimate platforms or of interest to some particular group of users, with the threat actors behind these web pages resorting to all sorts of tricks to hide their malicious activity. In the face of these threats, it is necessary that individuals and organizations have the necessary knowledge to identify a fraudulent online platform, which could prevent dangerous cyberattacks capable of causing severe economic, infrastructure and even public image damage.
This time, the specialists of the cyber security awareness course of the International Institute of Cyber Security (IICS) will show you the methods most used by cybercriminals to hide phishing platforms, in addition to showing some tools for scanning, detection, filtering and blocking of these platforms, which will help create a complete cybersecurity environment in any organization.
Search for potential threats
Many organizations are aware of these threats, so their IT areas have their own processes in place to limit the reach of a phishing website. Although each organization implements them as best suits their requirements, these processes usually share steps such as:
- Download lists of domains registered according to your geographic top-level domain
- Search for domains similar to the official domains of large companies, banks and public institutions
- If a potentially fraudulent website is detected, request domain locking from the registrar and configure a firewall to block this enterprise network platform
A more advanced option is to use automatic scanners, which make it easier to identify possible phishing attempts. Although protecting against these threats sounds simple, everything is complicated in real scenarios, so it is necessary to know in detail the tactics used by hackers to create phishing websites and keep them off the radar. For the following examples, the experts of the cyber security awareness course will take as a reference the official platform of the Russian energy company Gazprom (gazprom.ru).
Similar spelling
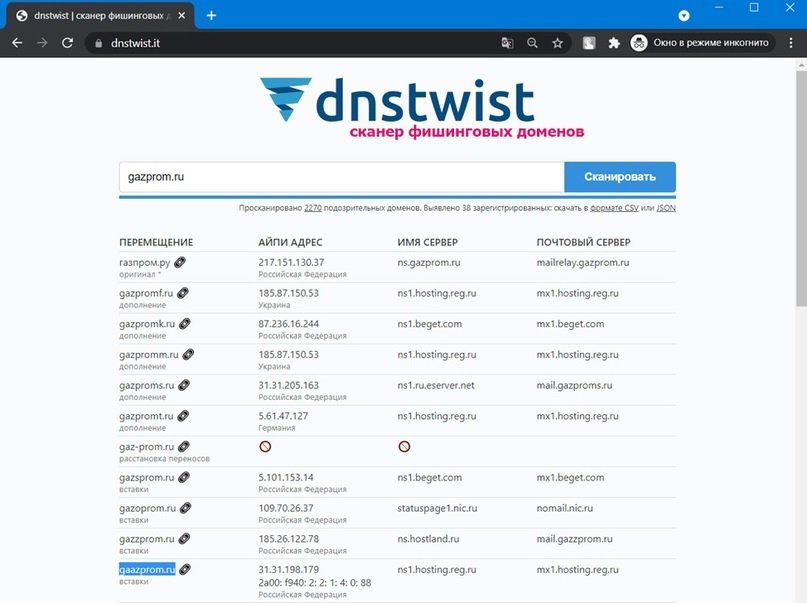
If in the list of registered domains all pages are selected with the word “gaz”, the members of your organization will not find domains like gaazprom.ru, intentionally registered with a wording similar to that of the official platform, evading the most well-known identification tactics.
The Dnstwist utility, available on Kali Linux, can be helpful when searching for malicious websites with a spelling similar to that of the legitimate platform. Dnstwist generates six different primary domain graphs and verifies which ones are registered. For example, 2270 options for gazprom.ru were generated and tested, finding 38 potentially malicious domains.
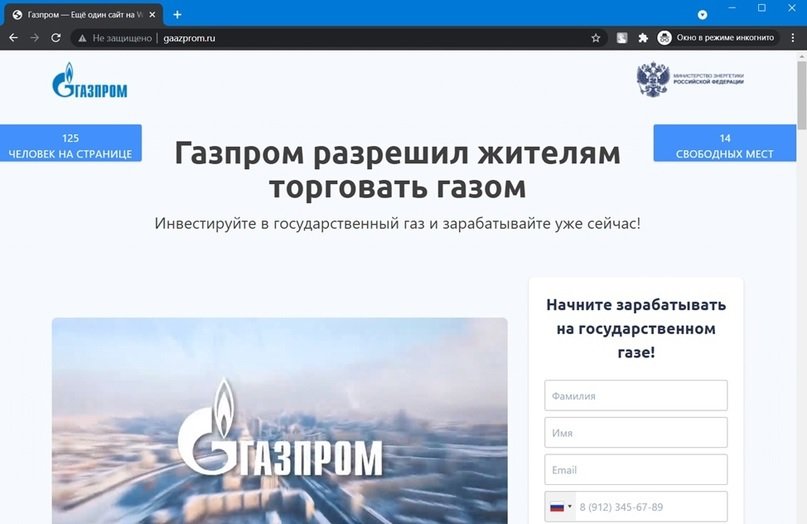
The following screenshot shows the home page of the fraudulent platform gaazprom.ru:
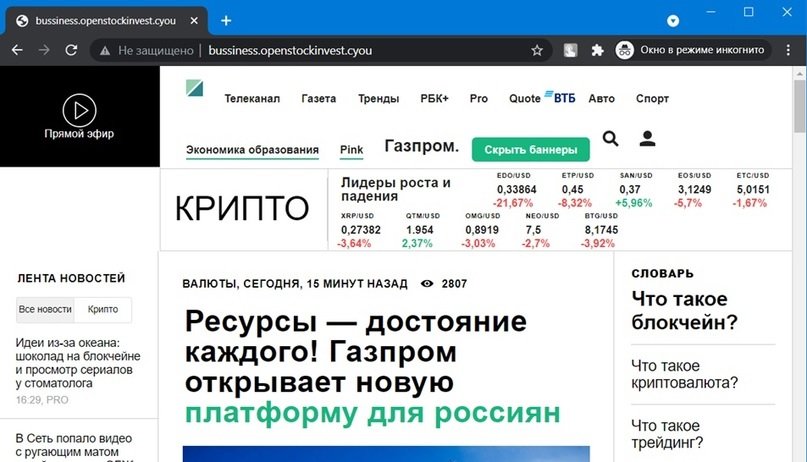
Subdomains
Everything is simple here. If we scan the site openstockinvest.cyou, we will not see anything suspicious. On the other hand, if we go to the hххp://bussiness.openstockinvest.cyou subdomain, a fraudulent page will suddenly appear.
Comfort zone
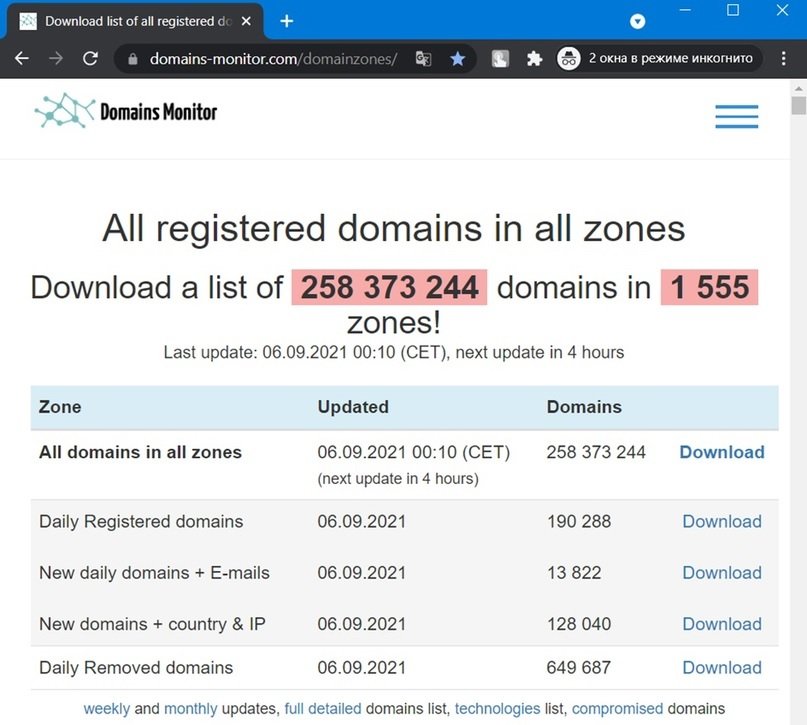
The experts of the cyber security awareness course mention that, sometimes, the search for fraudulent sites is limited to verifying only the geographical top-level domains, so another 1,555 zones would be left out. What’s more, Dnstwist doesn’t search every possible zone, so we can’t rely solely on this tool.
Tools like Domains-monitor.com allow you to download a list of 250 million registered domains to address all possible geographic areas on the Internet. The service costs $7 USD for 24-hour access.
Parasites
Just as it happens in nature, a virtual parasite uses other people’s resources to live as long as possible without attracting attention. In parasitic attacks, hackers take control of a harmless website and upload malicious content without users of the original platform being able to notice the hidden activity.
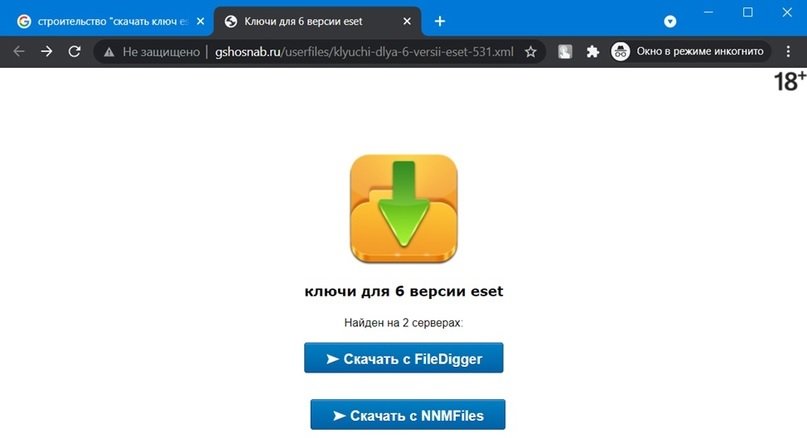
Neighbors
This term refers to the placement of fraudulent websites in “foreign” resources. For example, hххps://gatrade.turbo.site: in this case, the web page was created in the Yandex site builder.

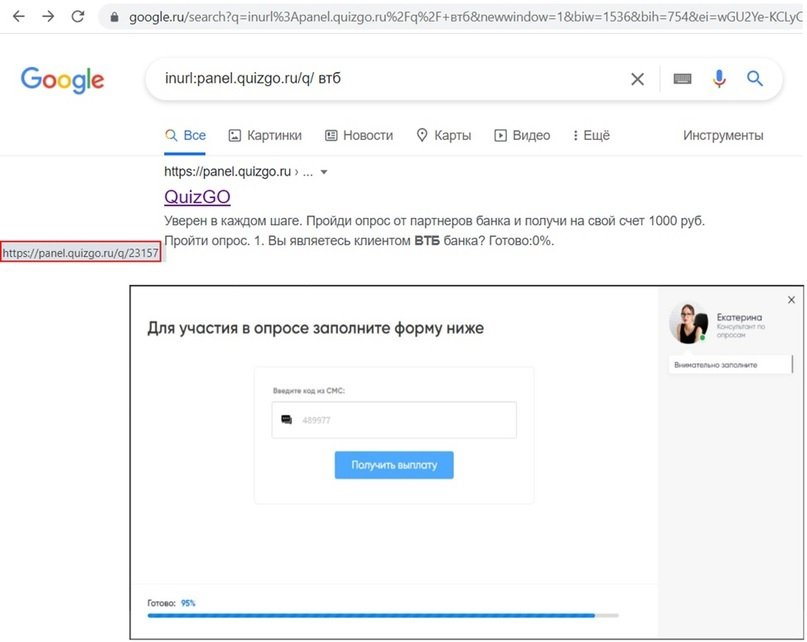
This category also includes sites created on quiz platforms such as Google Forms. Whether created for legitimate or malicious purposes, these questionnaires barely leave a minimal trace on Google, mention the experts of the cyber security awareness course.
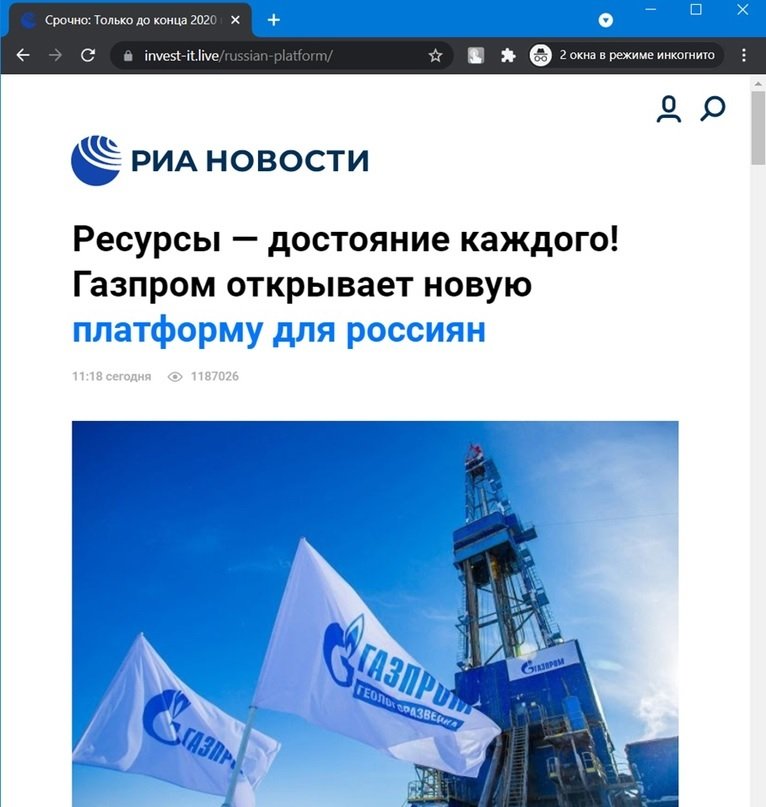
Inside
This is another way to prevent fraudulent websites from being identified by security scanners; if we click on the link hxxps://invest-it.live, we will be redirected to Google. In these cases, the fraudulent page is located “inside” the legitimate site, at hххps://invest-it.live/russian- platform.
Cloaking
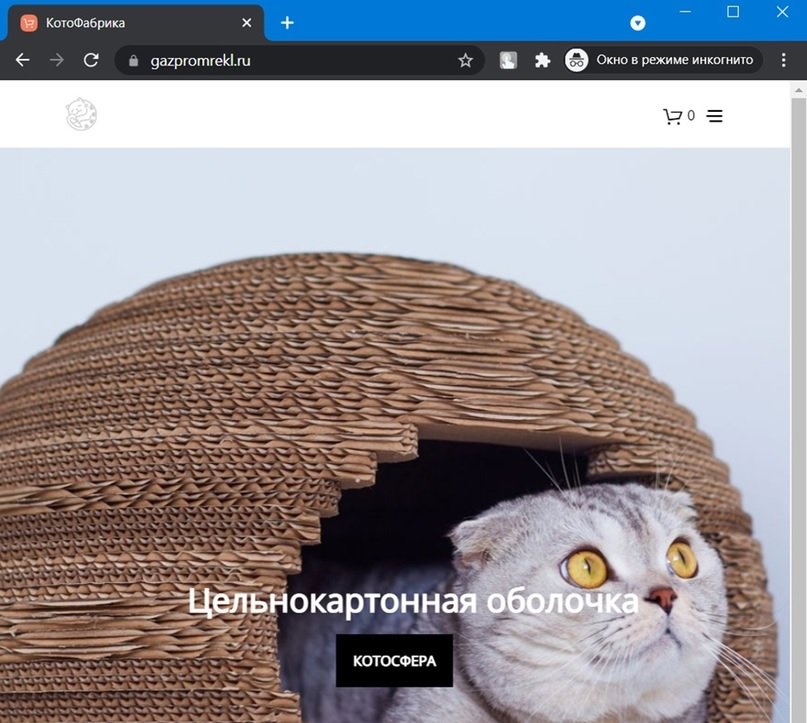
This term refers to the replacement of the content of the site, depending on the technical characteristics of the visitor. For example, if you log in from a Ukrainian IP at hххp://gazpromrekl.ru, we will see a fraudulent site, mention the experts of the cyber security awareness course.
If we search from any other IP address, we will be shown a store that sells cat houses.
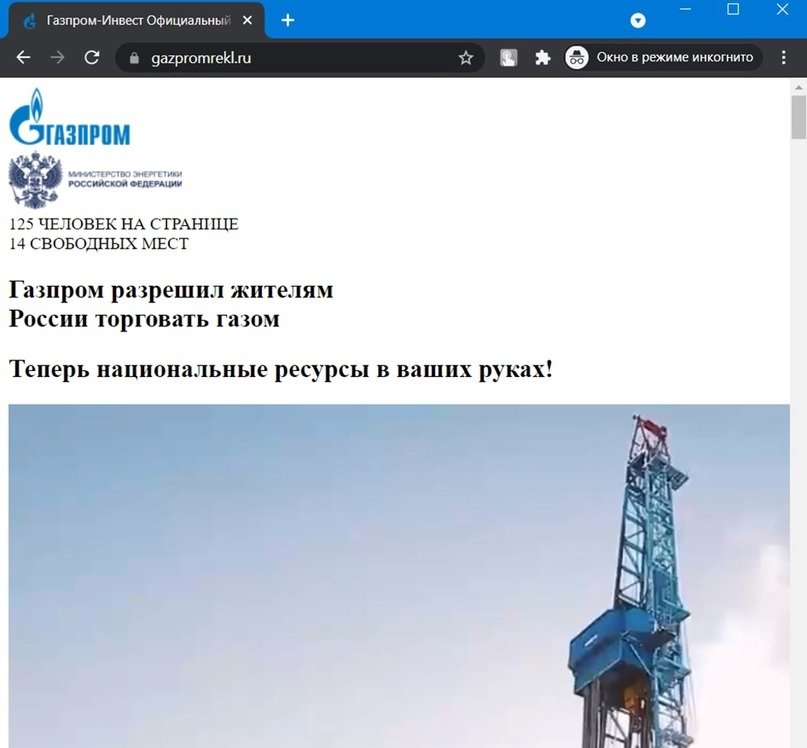
The link gazpromrekl.ru sometimes has errors, and when you log in from a Russian IP, it shows the site of some web studio. Cloaking is also used on social media to bypass moderation mechanisms.
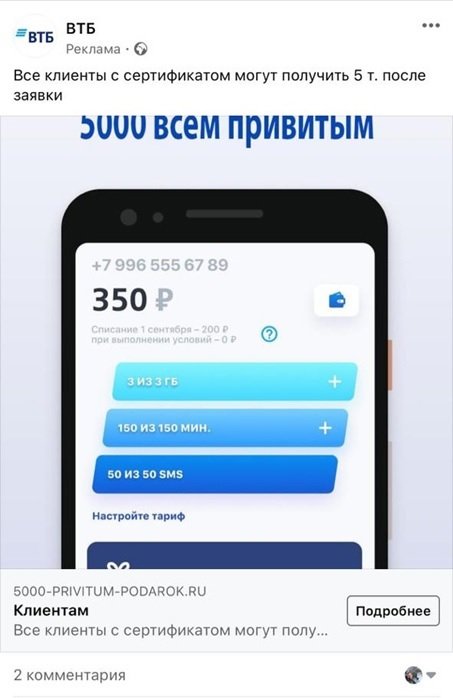
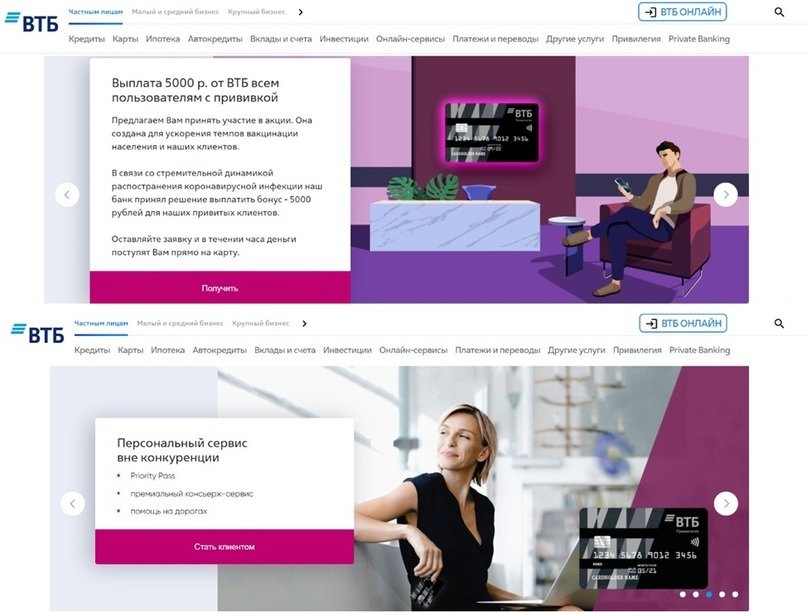
When a moderator moves from your European IP to 5000-privitum-podarok.ru, you are shown a site, and if you move from the IP of one of the CIS countries, the content is completely different.
The methods described in this article are just some of the resources used by cybercriminals around the world, in addition to the fact that in the dark web there are platforms that offer all kinds of tools and services for the creation, design and maintenance of fraudulent websites, which incredibly facilitates the deployment of this kind of hacking campaigns.
Faced with this scenario, resources such as technical blocking and employee training become fundamental, because given the current conditions everyone should use the Internet with the certainty that in that gigantic network there will always be a cybercriminal waiting for us to fall into their trap.
To learn more about information security risks, malware, vulnerabilities, information technologies, and more details on the cyber security awareness course, feel free to enter the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
