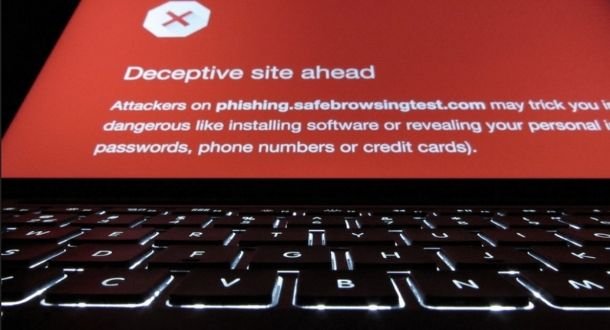
How cyber criminals hide phishing website on the Internet?
2022-04-27
The internet is rife with fraudulent websites posing as legitimate platforms or of interest to some particular group of users, with the threat actors behind these web pages resorting toRead More →