The use of remote management tools is becoming more common in public and private organizations around the world, especially due to the pandemic. While these tools have a legitimate use, they are sometimes associated with multiple malicious activities, as is the case with the tool shown below.
The cybersecurity course team of the International Institute of Cyber Security (IICS) brings us a tutorial of NjRat, one of the best remote access tools to perform all kinds of activities as if we had physical access to the target system.
Before proceeding, we remind you that this article was prepared for informational purposes only and should not be taken as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
What requirements must our system meet to use this tool?
According to the experts of the cybersecurity course, there are a number of requirements that we must meet for the use of NjRat, including:
- NjRat (remote administration tool)
- IP/dynamic host
- DUC (Noip.com Client)
- Open port
Using the tool
Download njRat v0.8 (the latest version available at the time of writing). You can also work with any previous version if you wish, mention the experts of the cybersecurity course.
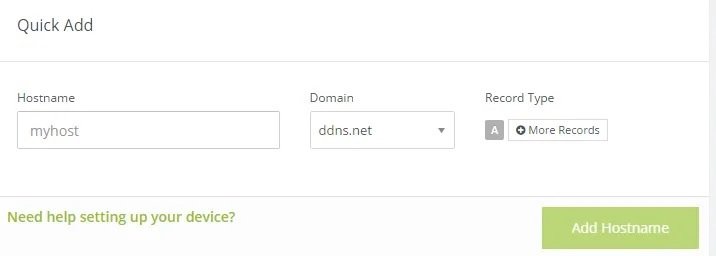
Go to the noip.com site and register as a user. Afterwards, you will be able to see a field as shown below to enter the hostname; enter any name, select any tld from the drop-down menu and click the “Add Host” button:
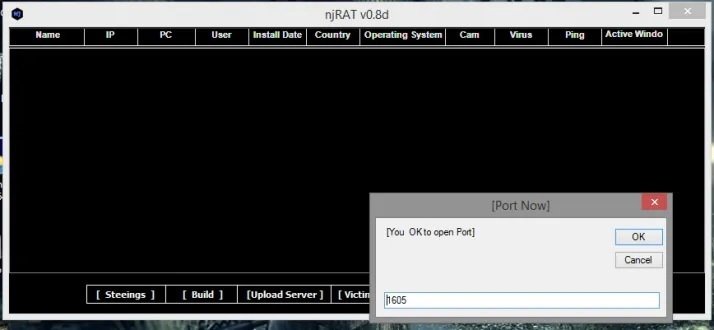
Next, open NjRat and start building the server. When you open the window, a pop-up window will appear as shown in the following screenshot where you will need to enter the port you want to use. Cybersecurity course specialists recommend the default port 1605.
After defining the port, click the Create button and complete the remaining fields as shown below. Be sure to enter your own hostname in the corresponding field.
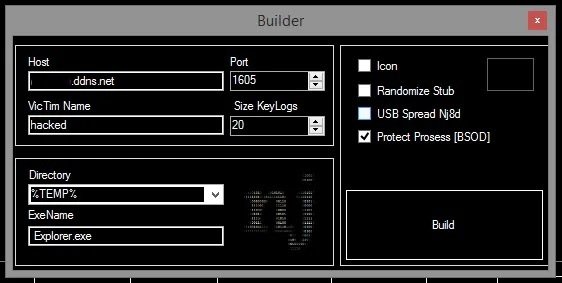
Enter port 1605. In the name of the victim you can enter the name you want. The size of KeyLogs is suitable for 20. Select the directory where you want to place your server and add the exe name. You can also use the icon by marking the icon, mention the experts of the cybersecurity course.
When you click the “Create” button, you will be asked to enter a name, specify any name, and click “Save”. Server creation begins. You will see a success dialog box. The server is now ready to be distributed to other computers. You can send it to someone through online files or by any physical means. Be sure to archive it before copying it to any physical media.
Now you need to open the ports, for which the experts of the cybersecurity course recommend using the method of your preference.
Download the DUC and enter your username and password in noip.com.
The configuration of the tool is already ready, so when someone opens the server created on a machine, the NjRat window will appear, giving the user remote access to the target system.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
