The most trusted source for download on the mobile OS platform , Google Play has now been caught for cataloguing some of the applications that contain trojan – a program that perform some malicious actions on your device without you consent . Cybersecurity analysts from Doctor Web virus have come across some of the applications that contains trojan which is programmed to work as an android bot Android.Circle.1 to perform their malicious tasks .
The multifunctional bot , Andorid.Circle.1 , gains the trust of people by hiding under the name of some harmless applications . These harmless applications are under the category of images, programs with horoscopes, applications for online dating, photo editors, games and system utilities on Google Play which has over 18 modifications and over 700,000 downloads as commented by experts from Doctor Web virus . Android.Circle.1 is programmed in android based Kotlin language and is created using Multiple APK mechanism to support it in a variety of devices. Some examples of applications are as follows :


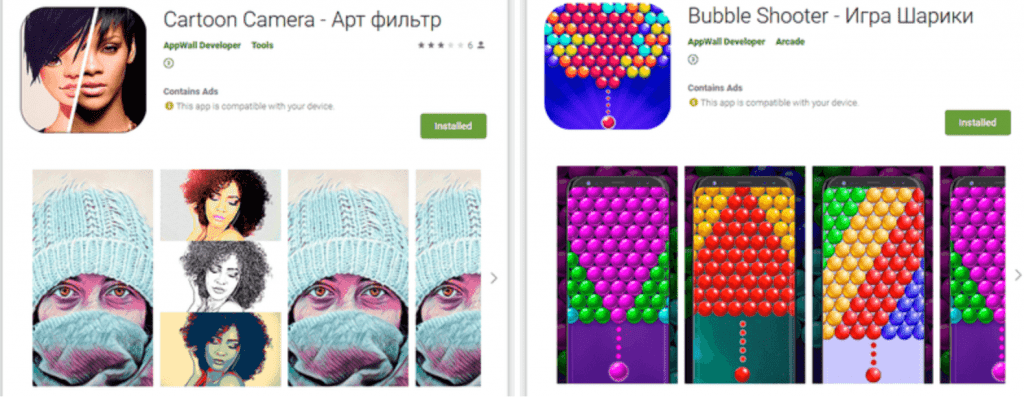
HOW THIS TROJAN OPERATES ?
The trojan embedded in these applications implements a mechanism and divides the main apk into several apk files as some of the malicious function performed by Android.Circle.1 are taken from the library libnative-lib.so which is located in one of such auxiliary divided APKs but the android OS is not able to recognize these multiple APKs and thus perceives the collection as a single application . Thus , Multiple APK mechanism acts a self defense mechanism for this trojan .
On successfully installing, the trojan communicates with the Control and Commanding ( C&C ) server via secure HTTPS with additionally encrypted AES algorithm. The trojan modifies itself and disguise under a standard android application in the list of installed programs and presented with name com.google.security .
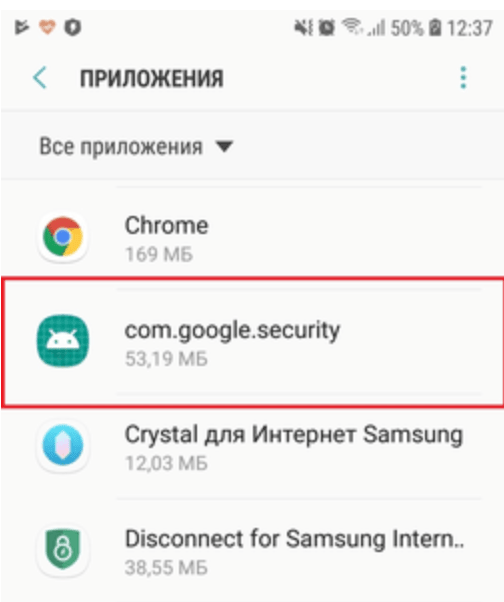
The first task performed by the trojan that it sends the below information to the server :
- packages – list of installed applications;
- device_vendor – device manufacturer;
- sRooted – root access;
- install_referrer – information about the link where the application was installed;
- version_name – a constant with a value of “1.0”;
- app_version – a constant with a value of “31”;
- google_id – user identifier in Google services;
- device_model – device model;
- device_name – device name;
- push_token – Firebase identifier;
- udid – unique identifier;
- os_version – version of the operating system;
- sim_provider – mobile operator.
After sending this information , the trojan expects some commands in the form of messages from the Firebase Cloud Messaging Service . The server replies some BeanShell scripts commands and these instructions are saved in prefs.xml configuration file . These BeanShell Scripts are executed with the help of libnative-lib.so open source library built into the trojan which a Java code interpreter and allows to execute Java-based code . Some of the tasks performed by the bot is as follows :
- remove the Trojan application icon from the software list in the main screen menu;
- remove the Trojan application icon and load the link specified in the command in a web browser;
- perform a click (click) on a loaded site;
- show banner ad.
Thus from the above tasks , displaying ads and forcing user to fall in the trap of attack , are the main intention of the attacker . Through ads , the attacker will be able to download the some malicious websites for phishing attacks though it is illegal to execute any third party code according terms and conditions of Google Play . The trojan displays ads as :
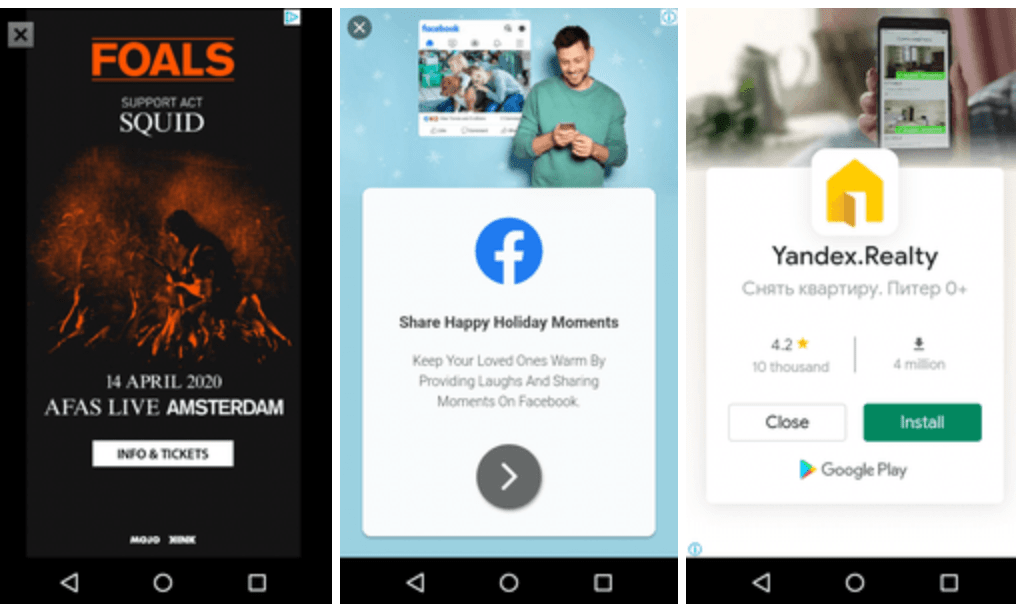
Despite these basic function , the bot can also load and execute any code based on the instruction that it received from the server but it is restricted by device configuration . There are some of the indicators or some applcations of this trojan network :
- com.app.bestwallblack
- com.aboutlife.futureviewer
- com.horoscopelife.zodiac2020
- com.wallypi.pepers
- com.daily.astrologyhoro
- com.findyou.lifehistory
- com.lovs.datter
- com.hdwallpaper.beautywalls
- com.batterybooster.speedup
- com.relationship.horolove
- com.wallypi.peperspro
- com.imagerepair.cartooneffectpro
- com.hdwallpaper.beautywallspro
- com.daily.astrologyhoropro
- com.imagerepair.cartooneffect
- com.bubbleup.gamepop
- com.mydatter.loves
- com.wallpapershop.livepaper
CONCLUSION
Though all the detected modifications of the Android.Circle.1 have been removed form the Google Play , there are chances that attackers can place new versions to it .
- Scan the application with the help of antivirus before installing it .
- Do not click on the third party links in the installed apps or enter any sensitive information on that link .
- Do not click on the ads displayed in the app .

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
