Almost every country in the world is paying for Coronavirus by self-quarantining itself. The whole world’s economy is at a great loss in this period of time. All the officials are at home with doing their works either it may be official or homework and so if everything is operating from home then entertainment should also too be.
So here we have some bad news for those who entertain themselves from home. If you have some talent or you are a star who wants to show off their skills, the first name might come in your mind is Tiktok. But why Tiktok? This question has a simple answer that the fan following you get here is great as according to Google Play statistics it has now crossed one billion plus downloads all over the world (which is even greater than PUBG downloads). But we have a question for you, what if some other actors misuse your accounts to get famous, to get you fans? We think you are not aware of that side.
Some researchers have a doubt on company’s privacy policies and so they did some research to find out flaws in that. So they come out with some results which is a major drawback of using this app that is use of HTTP protocol to transfer the data from its servers to the end user. If you are tech savvy, you might be aware of what we are trying to say but if you aren’t, here is the detailed information about the flaw.
LET’S EXAMINE THIS IN DETAIL
So what happens when you download videos or anything from Tiktok? The Tiktok is programmed in such a way that in its backend programming there are some servers which instructs the app to download the given content.
This para for networking geeks – If we talk about in networking terms , the Application layer is responsible for presenting the data in a user friendly format to the user. Every layer in the TCP/IP model has its own protocol, so Application layer too have. Here, the two protocols HTTP and HTTPS are the protocols at the Application layer and it decides how the data is transmitted over the network to the required end user i.e. either encrypted or unencrypted and thus basic difference in both is of encryption. HTTPS means HTTP using Transport Layer Security (HTTP over TLS) and so if we really talk about the three rules of transmitting the data C.I.A (Confidentiality . Integrity and Authentication).
So, coming back to the main topic , after successful TCP handshake when a user asks one of the Tiktok servers from Content Delivery Network (A network of geographically based servers to allow the end user to download the requested the content) ,”hey server , I want to download xyz video , Could you please allow me to do that” , Tiktok server will say “yes you can“. So how will it look when some third person or might be your friend can see this conversation between you and to the end server, it can be embarrassing or sometimes ditching. Tiktok servers are using HTTP protocol, which is unsecured way to data transmission. The below screenshots are the analysis of the Tiktok app through Wireshark Tool (which is network analysis tool) :
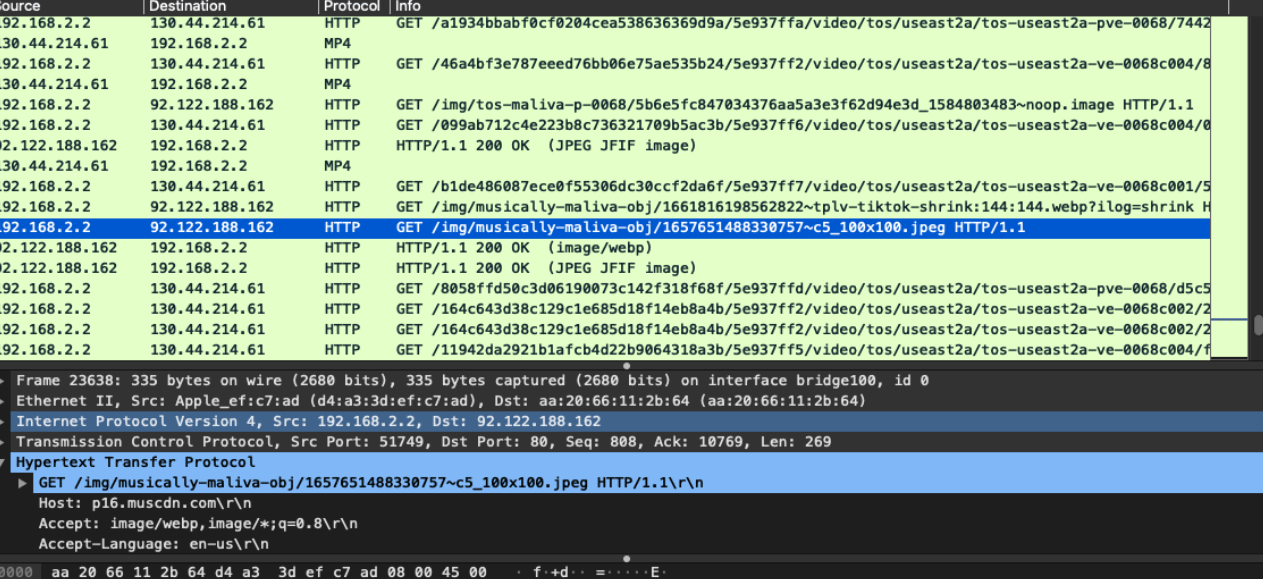
source
As you can see, the client is connecting to the end server using HTTP protocol. Analysis show that videos are downloaded from the following domain names:
Profile photos and still images are downloaded from
Anyone who can see your network and trying to do Man-In-The-Middle attack, because of this protocol, it is easy for the attacker to easily read and alter the content on your network. Thus, through this technique , an attacker can send the fake content to the user and spread the malicious content on the network.
Thus, if a Tiktok user request for some video, and attacker can manipulate the content on its network and the end user receives some malicious content. Here is a demonstration of how an attacker misuse the HTTP protocol to spread its message.
CONCLUSION
- As we all already discussed that Man-In-The Middle is only possible if someone is connected to your network, so please don’t try connect yourself to an open or Public Network as most attackers targets these networks and can easily take the advantage of the flaw in the TikTok.
- If you are using VPN, use reputed VPNs only as sometimes untrusted VPN are launched with a purpose of doing MITM.
- Always connect to a secure network.

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
