Microsoft has issued a warning that systems that are still utilizing the long-discontinued Boa web server might be at danger of attacks. This comes after a series of intrusion attempts were made into the power grid operations in India, which most likely involved taking use of security holes in the technology.

It’s possible that those who are vulnerable are unaware that their devices run services utilizing the defunct Boa web server, and that firmware upgrades and downstream fixes do not address the known vulnerabilities in the Boa web server.
Researchers from Microsoft’s Security Threat Intelligence unit reviewed a report from the cybersecurity company Recorded Future that was published in April. The report discussed the intrusion attempts that had been made into India’s power grid as far back as the year 2020, as well as more recent intrusions into a national emergency response system and an Indian subsidiary of a global logistics company.
When the Microsoft researchers dug further into the data, they discovered a vulnerable component on the IP addresses that were indicated as symptoms of intrusion. This component was the Boa web server (IOC). In their own investigation, which was published last week, they said that they “discovered indications of a supply chain risk that may impact millions of organizations and devices.”
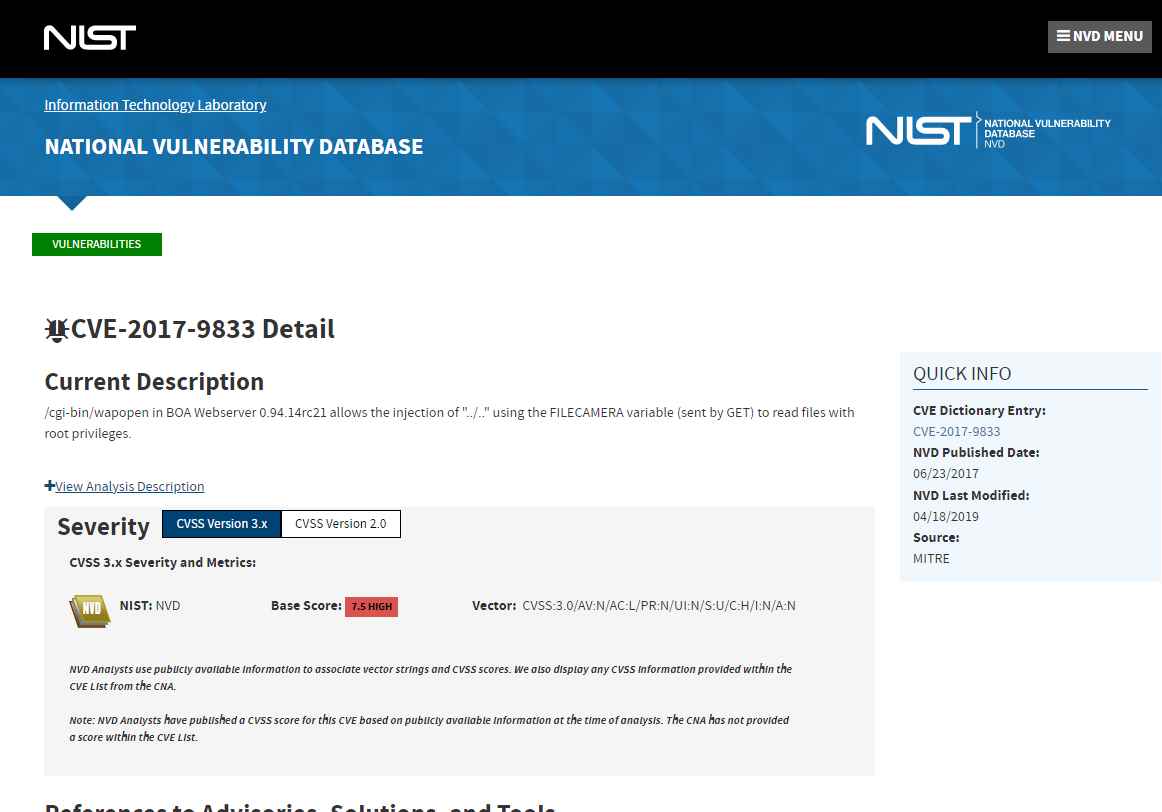
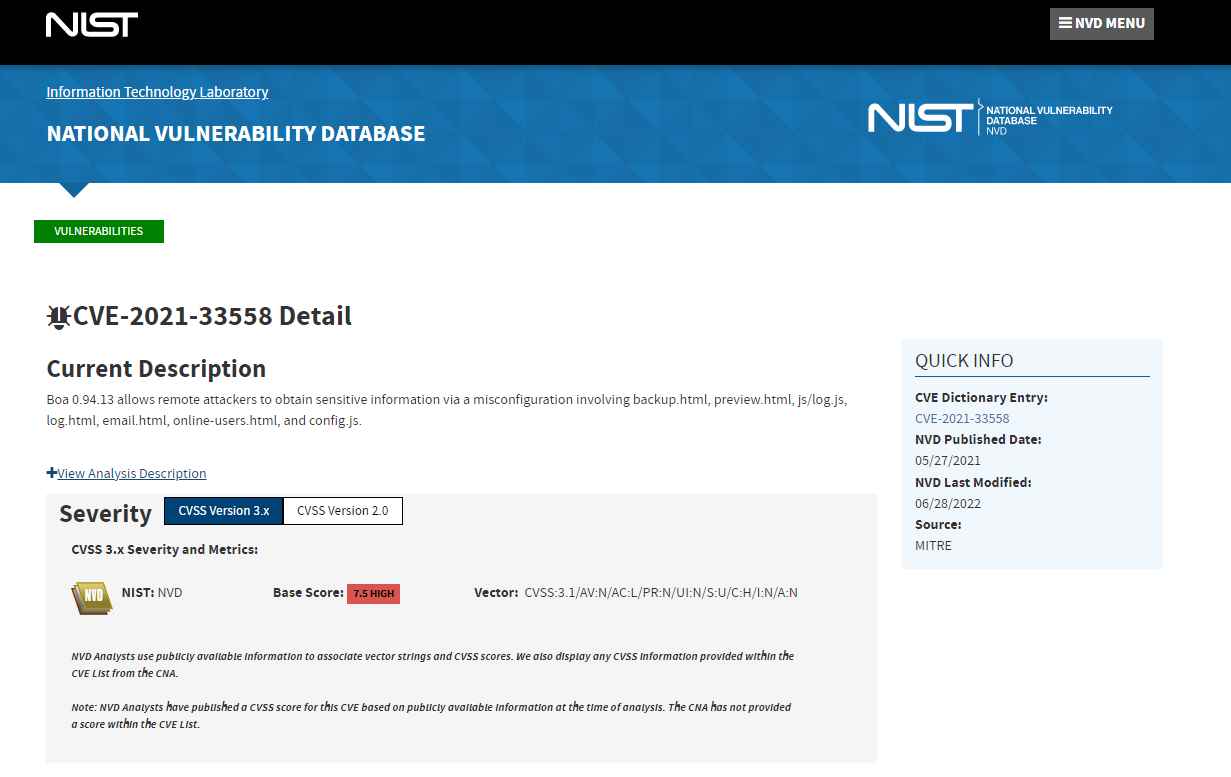
CVE-2017-9833 and CVE-2021-33558 are two of the known vulnerabilities in the Boa web server. These vulnerabilities could allow attackers to remotely run code after gaining access to the device by reading its “passwd” file or stealing user credentials after accessing sensitive URIs in the web server. Both of these vulnerabilities have been patched. Exploitation of these vulnerabilities does not need the presence of a logged-in user.
Boa is an open-source web server that was developed specifically for embedded applications. It enables users to view the configuration panels, administration consoles, and sign-in screens that are present in various devices. They said that even though it was taken off the market in 2005, a variety of IoT gadgets and popular software development kits are still making use of it.
It’s possible that you won’t even be aware of what’s going on. According to what the researchers said, “without engineers controlling the Boa web server, its known vulnerabilities might enable attackers to stealthily obtain access to networks by collecting information from files.” “Additionally, people who are impacted may be unaware that their devices run services utilizing the discontinued Boa web server, and that firmware upgrades and downstream fixes do not address its known vulnerabilities.”
In this particular instance, Microsoft examined the Internet Protocol (IP) addresses that Recorded Future had provided in the list of indicators of compromise (IOCs) and traced several of them back to Internet of Things devices like routers that had unpatched vulnerabilities. All of the published IP addresses were compromised as a result of multiple attackers employing a variety of different strategies. These strategies included attempting to use default credentials for brute-force attacks, downloading a variant of the Mirai IoT botnet malware, and attempting to run shell commands.
One of the reasons might be because Boa is used in SDKs, which do not always have their vulnerabilities fixed even when the firmware of the IoT device is updated. Additionally, it is difficult to determine if the device components can be updated or whether they have already been updated. Firms who manufacture gateway devices like routers, access points, and repeaters utilize RealTek’s SDKs as an example since these SDKs feature Boa and are used in SoCs by these companies.
Attackers have, throughout the course of the previous several years, focused their attention on devices that run RealTek’s software development kits (SDKs).
Being able to gather data from networks that are part of essential infrastructure without being discovered may lead to attacks that are extremely disruptive, which can cost millions of dollars and affect millions of individuals and enterprises.
“The popularity of the Boa web server shows the potential exposure risk of an unsecured supply chain,” the researchers said. “Updating IoT firmware doesn’t always patch SDKs or [SoC] components, and there’s limited visibility into which components can be updated.”
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
