The infrastructure for a hacking effort that exploited Microsoft OneNote files to distribute malware was shared with a previous campaign that employed a data stealer that was housed on a Discord server. This attack targeted government organizations in the Asia-Pacific and North America areas. Researchers at Menlo Security have identified a previously undisclosed threat actor that, according to the researchers, does not seem to be a large role but that should nonetheless be monitored due to the fact that it targets government organisations.
Email is used by the hackers behind the campaign to trick potential victims into downloading the malware downloader for PureCrypter by encouraging them to click on a link that takes them to a Discord server. The downloader can be purchased online for $59. It is designed to circumvent detection by antivirus software by using obfuscation methods. A malware downloader known as PureCrypter is capable of disseminating a broad variety of ransomware, other forms of malware, and information stealers. In June of 2022, it was discovered for the first time. It is available from its developer, PureCoder, for a monthly fee of $59 or for a one-time payment of $245 for life.
The developer has extended its capabilities to include the PureLogs logger and information stealer, which can steal data from cryptocurrency wallets, web browsers, and email clients for the low price of $99 for a single year of access or $99 for lifetime access.
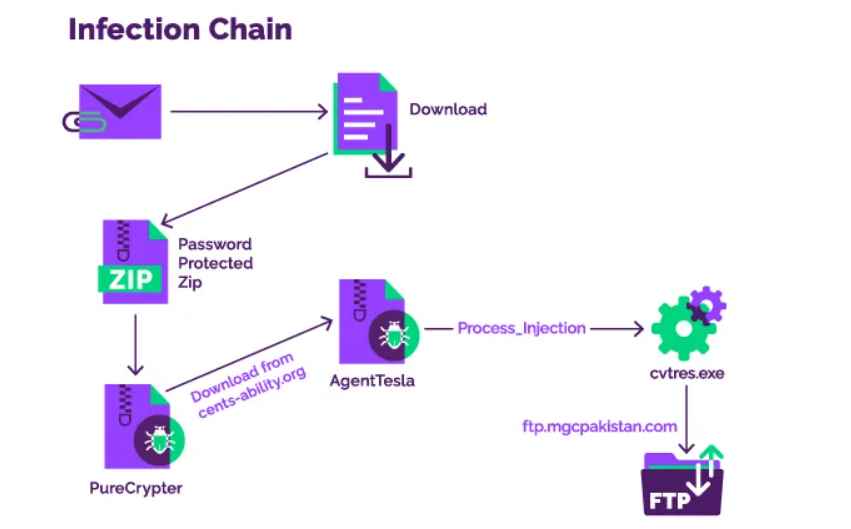
Researchers claim that the perpetrators of this campaign are distributing the PureCrypter downloader, and that the major targets of their attacks are institutions affiliated with the government. In order to deliver a second payload, the threat actor leverages the domain of a non-profit organization that has been hacked as their command and control center.
Researchers have seen that PureCrypter spreads many varieties of malware and information stealers in the course of this operation. They include Redline Stealer, AgentTesla, Philly Ransomware, and Blackmoon.
Researchers said that they got suspicious after seeing that Menlo’s Cloud Security Platform had restricted archive files across several government clients throughout the North American and Asia-Pacific regions. These files were secured by passwords.
A phishing email containing a malicious link to Discord serves as the launchpad for the attacks. This URL will open a password-protected ZIP file that contains the.NET malware downloader PureCrypter. This malware downloader will then download a secondary payload from the command and control infrastructure of the attackers.
Researchers from Menlo Security tried to follow the PureCrypter connection in order to get the secondary payload; however, they were unable to do so since the link led to a hacked web domain that, at the time, seemed to be down.
Additional samples acquired from the campaign revealed that the download was AgentTesla, a data stealar that was first seen in 2014.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
