A security researcher has discovered a technique to harness the data deletion capabilities of widely used endpoint detection and response (EDR) and antivirus (AV) software to transform these programs into data wipers. The software in question is from Microsoft, SentinelOne, TrendMicro, Avast, and AVG.
Or Yair, a researcher at SafeBreach, had the notion to take use of the existing security features on a targeted system. This would make the attacks more covert and eliminate the need that a threat actor must be a privileged user in order to carry out harmful operations.
The idea of deletion is generally the first thing that comes to mind whenever you hear the term “wiper.” However, there is an essential distinction that can be drawn between the two. When a particular process in Windows makes a call to the DeleteFile() API function, this function then makes a request to the kernel to remove a particular file. After that, the kernel navigates to the master file table (MFT) and designates an item there as being available for use. This item is nothing more than a link to the content of the file itself. The contents of the files themselves are not really removed from the disk; they remain on the hard drive. This is the key distinction between erasing something and wiping it clean. When something is “wiped,” it signifies that the information contained inside it is being fully removed and cannot be recovered in any way.
A deletion, on the other hand, may be used to accomplish the same thing as a wipe. According to the Microsoft Developer Network (MSDN), “When files are destroyed from a New Technology File System (NTFS) disk, their MFT entries are marked as free and may be reused.” This indicates that a newly generated file is able to utilize the same free MFT entry if it already exists. A user is able to replace the actual content of a deleted file by writing to a file that was assigned an MFT entry that was previously used by the deleted file. This is possible since the MFT entry was previously used by the deleted file. After doing research into the methods that well-known modern wipers use to close the gap that exists between a deletion and a wipe, he discovered that many of these wipers do not remove files but rather replace them. They are able to confirm that they are modifying the actual content of the file in this manner, and as a consequence, they are able to successfully delete it.
This method is used by well-known wipers such as Shamoon, CaddyWiper, DoubleZero, IsaacWiper, KillDisk, and Meteor. Essentially, these wipers open the files they want to delete and then overwrite them in order to guarantee that the actual contents of the file are being replaced. Nevertheless, this method calls for a high level of rights. For instance, in order for the wiper to be able to remove certain files from the folder that is associated with the administrator account, it is necessary for it to have access rights to those files. This is also true for the files that make up the system. As a consequence of this, these wipers will often operate with administrator rights.
Wipers of today also use a method known as drive destruction, which is one of their other techniques. When using this method, the wiper first opens the drive as a device and then begins writing straight to it. As a consequence of this, it is able to replace the boot-sequence structures that are part of the NTFS as well as the contents of the files. IsaacWiper, KillDisk, a variation of the Petya wiper, SQLShred, StoneDrill, WhisperGate, and DriveSlayer are examples of well-known wipers that use this approach. However, in order to utilize this option, you will need to have administrator capabilities. This is because a normal user should not be able to fully corrupt anything that is stored on the hard drive.
At this stage, it would be beneficial to have an understanding of the circumstances under which EDRs decide to destroy or quarantine data. He did find that most EDRs come preconfigured with a setting that allows them to immediately destroy or quarantine files that they determine to be hazardous. Some programs do this whenever a file is opened, at which point they identify it as harmful. This is something that other EDRs perform after the files have been written to and then closed afterward. And despite this, more EDRs do act in any of the two cases. However, most EDRs do include the ability to conduct a scan, and this may either be a specialized scan of a specific path on the file system or a more comprehensive scan of the whole system.
The initial concept that sprang was to add some harmful code to a file that was otherwise safe, and then to wait for the EDR to remove that code. However, there are two issues with using this strategy. The first problem is that the wiper does not have the necessary write rights for the majority of the crucial files that it may seek to delete. The second issue is that this procedure is quite similar to the method of overwriting files in terms of the API calls that are required. As a result, he abandoned the idea.
His second thought was to trick the EDR into thinking it was deleting the route it was originally supposed to remove while simultaneously directing it in the direction of another path to delete. In most cases, these vulnerabilities may be exploited via the use of links. CWE 59, which refers to the category of link vulnerabilities, is quite well-known in the cybersecurity sector. Microsoft even realized that they needed to give a special user right, which they called the “create symbolic links” user right, to enable users to create symbolic links (symlinks) because they are commonly used in a large number of vulnerabilities that allow privilege escalation. They called this user right the “create symbolic links” user right. This user privilege is only automatically granted to administrators; in order for other users to have access to it, an administrator will need to do so manually.
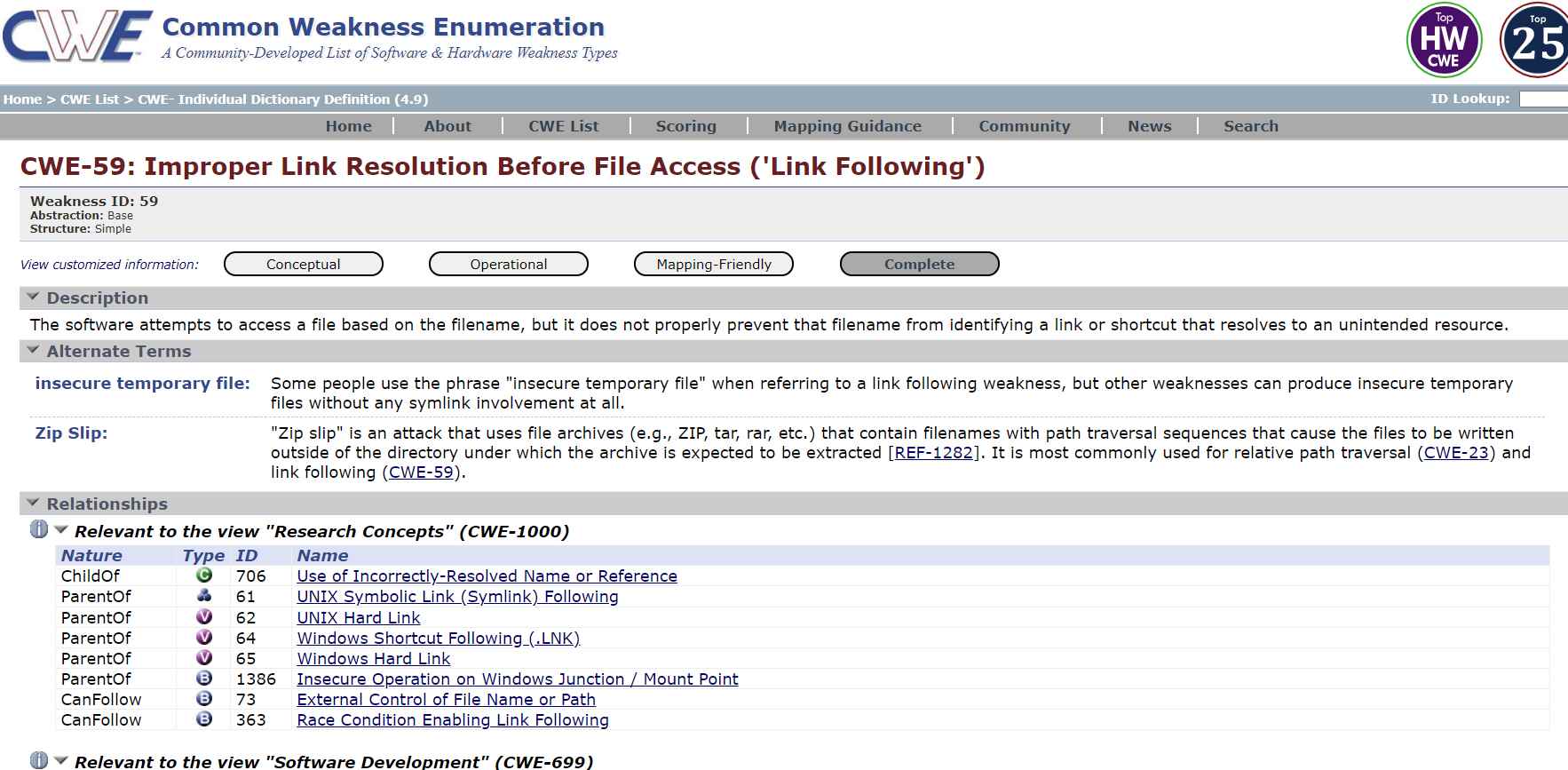
Another kind of connection that may be made on an NTFS file system is called a junction point. It wasn’t long before he started considering the distinction between junction points and symlinks. If we examine a local directory symlink and a junction point, we will see that, from a high-level vantage point, there is no difference between the two. On the other hand, in contrast to a symbolic link, a junction point may be formed by a user without elevated privileges. He rapidly came to the conclusion that it was possible for me to make advantage of a junction point connection, however he still needed to locate the appropriate opportunity window.
Let’s have a look at this scenario in order to get an understanding of how to direct an EDR at a certain location within this window of opportunity. Let’s imagine We wish to remove a.sys file, which is a driver and is located in the directory C:\Windows\System32\drivers. But we are just a regular user without any special permissions. As a user with no privileges, it is obvious that we are unable to remove the file. However, we have the ability to build a unique path that is quite similar to the path that he want to remove, with the primary distinction being that the majority of the path is housed inside a directory that we have power over while being a user with a lesser access level. In this particular instance, it would be C:\temp\Windows\System32\drivers, and this is the directory where we produced the.sys file.
His next plan of action was to make an attempt to seize the handle of the malicious file that he was generating in order to trigger a system restart. This conclusion was reached on the basis of the fact that once we open a file in Windows or create a file in Windows, the operating system prompts us to choose the file-sharing mode in order to ascertain whether or not other processes are able to edit or delete the file. Therefore, when he generated the malicious Mimikatz file, he did not provide any permission for it to occur. Instead, he left the handle to it open and waited to see what results it produced. Both the EDRs and the AVs started giving me warnings that a restart was necessary in order to completely eliminate the danger.
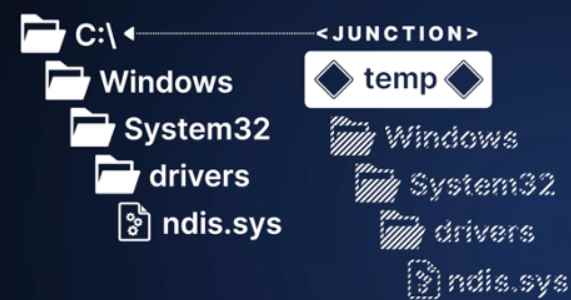
Once again, he saw two distinct patterns of conduct. The first issue was that some EDRs and AVs exploited the standard Windows API to delay deleting files until the next time the computer was restarted. This was the approach that SentinelOne, for example, used in handling the matter. The second way is one that he has seen used by several EDRs and AVs. What they do is simply keep a list of the routes that need to be erased someplace, and then after a reboot, they delete that list. However, if we take a look at the standard Windows API, we can see that the process of delaying a deletion until after the next time the computer is restarted is carried out by using the MoveFileEx function while passing in the flag MOVEFILE DELAY UNTIL REBOOT.
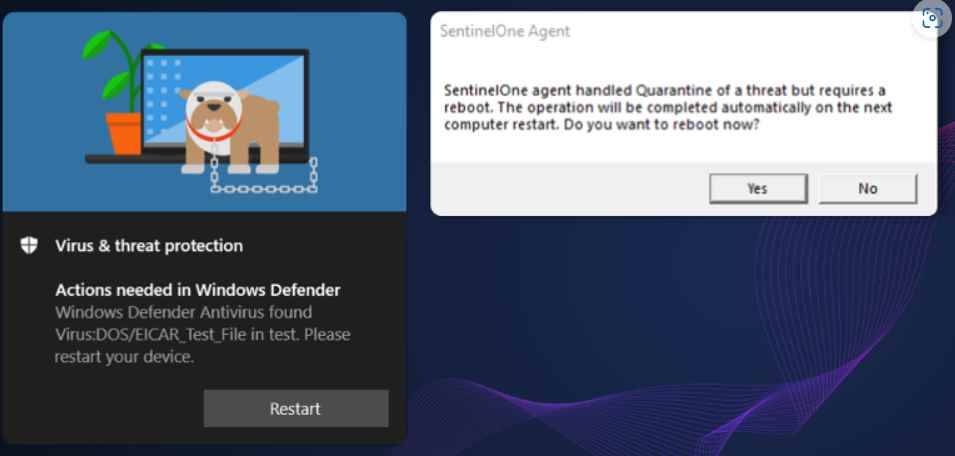
An Outline of the Steps to Be Taken in Order to Activate the Privileged Delete Vulnerability
If we consider all of this in the light of the prior illustration, the finished product might appear somewhat like this:
- Make a unique path that includes the malicious file that is located at C:tempWindowsSystem32driversndis.sys.
- Keep your hand on its handle to coerce the EDR or AV into delaying the deletion until the next time the system is restarted.
- Delete the directory located at C:temp.
- Create a junction C:\temp → C:\
- Reboot
Between July and August of 2022, Yair communicated the vulnerabilities to all susceptible suppliers, and as of right now, all of those companies have issued patches.
CVE-2022-37971 (Microsoft), CVE-2022-45797 (Trend Micro), and CVE-2022-4173 are the vulnerability IDs that have been issued by the vendors for this particular problem (Avast and AVG).
These are the versions with the fixes:
Version 1.1.19700.2 or later for the Microsoft Malware Protection Engine
Hotfix 23573 and Patch b11136, or a later version, are required for TrendMicro Apex One.
Avast & AVG Antivirus: 22.10 or later
Users of the aforementioned products are strongly encouraged to install the latest security updates as quickly as is practically practicable in order to reduce the significant danger of having their data deleted by malicious software that imitates the wiper capability.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
