Malware infections have become the main threat to users of internet-connected devices, and one of the most common ways in which threat actors deploy these attacks is through the web browser, which can be used for information theft. However, it is difficult to familiarize users with these risks and their consequences, as this depends on a certain level of technical knowledge.
To solve this problem, researcher Matthew Bryant developed CursedChrome, an extension available on GutHub that is divided into two elements:
- A plugin for the client, which is the extension itself
- A plugin for the attacker, which is a control panel to which the information extracted by the tool is sent
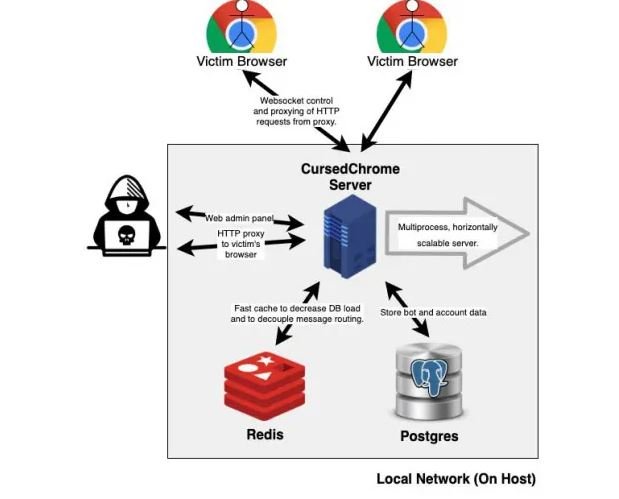
A user can use CursedChrome to demonstrate how a real attack on their browser works to extract login credentials from platforms such as social networks or payment systems like PayPal.
CursedChrome was designed to show how dangerous Chrome extensions developed by unknown sources can be. However, multiple cybersecurity specialists point out that this extension should only be used under fully controlled scenarios, as its out-of-context use can lead to actual loss of information, especially as their code is available to the public. It should be noted that this is a widespread critique of this kind of developments, as is the matter with the Metasploit pentesting tool.
On the other hand, the creator of CursedChrome states that his intention is not to facilitate hacking activities, but that he wants other researchers to be able to easily simulate the scenarios that allow cyberattacks. This tool can be used by “red teamers”, who are groups of cybersecurity researchers who are paid to try to hack enterprise networks; it is the companies themselves that reward them if they find these critical mistakes. With the extension they save time by not having to create code from scratch.
Finally, Bryant argues that his extension employs technology that had already been developed, so it does not actually generate a new attack vector. Besides, for a threat actor to use it, you would first have to get permission from the Chrome Web Store, which is impossible given the nature of the extension, so that users and researchers can use CursedChrome to demonstrate the consequences of a cyberattack safely.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
