A couple of weeks ago, a hacker identified as “Bassterlord” claimed to have administrator access to the network of a tax collection office in India.
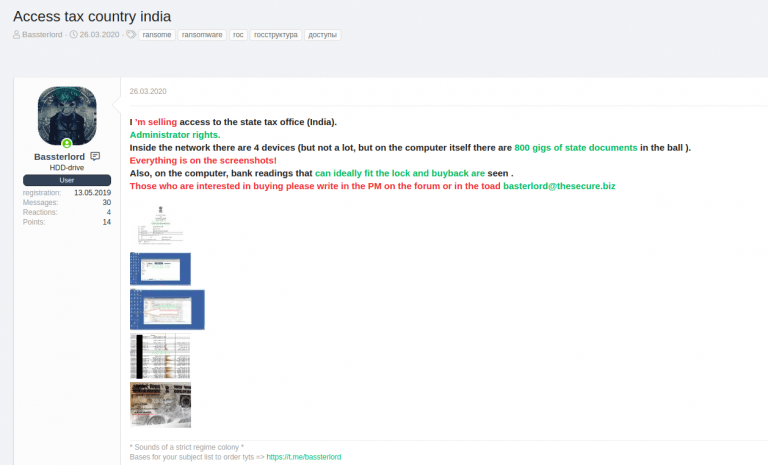
In his post, on a Russian-speaking hacking forum, it can be seen that the hacker mentions that this network is made up of four devices that store 800 GB of government information. Bassterlord adds that he is accepting requests through communication channels such as Telegram, his personal email and the hacking forum itself.
The writing of this post is not good enough, so cybersecurity experts are unclear if the hacker is selling the leaked data or just the compromised system access credentials. However, as proof of the hack, Bassterlord posted five screenshots; after being analyzed, the experts concluded that the incident is real.
Below is an analysis of each of the screenshots posted by the hacker.
1. The seller tries to point out that the state tax office system was hacked.
This screenshot shows that the system has 3 storage units:
According to specialists, it is practically impossible to extract 800 GB of data without attracting attention, so it is most likely that the hacker is only selling access to this network, not the data.
Some of the sensitive file names are:
- Export_Tax
- Tele doc.xls
- Tele-Directory
- Telephone Nos off…
- life_time_cal..
- mobile_introductory
- Book1.xlsx
- RomeshAshokbh…
The upper left corner of the screenshot has Russian text that translates as “Remote Desktop Connection”. The hacker likely gained access to the Remote Desktop tool to exploit a remote code execution flaw, using the default RDP credentials or using brute force.
2. The vendor tries to make this look like proof that they really do have administrator rights on the affected system.
The arrow in this screenshot points to a folder on the desktop named “admin”, indicating that the threat actor could have logged into the target system using the administrator’s login credentials.
3. According to the seller, this is a test of access to confidential documents in the target system. The image below is a Provisional Registration Certificate, for P N Goradia & Co. We can also note that the certificate has been issued by the Gujarat Government. This could mean that the threat actor could have access to a local tax office in India.
The details of P N Goradia & Co on the certificate match the information on indiamart.com:
- P N Goradia & Co.No.
- Address: 302, Taksh Classic in front of the IOC fuel pump, Vasna Road, Vasna Road,
- Vadodara-390007, Gujarat, India
4. The seller assures that this is evidence of access to some confidential documents. The image belongs to Vishmit Enterprise’s Permanent Account Number (PAN) card.
After doing a little more research, cybersecurity experts discovered that this PAN card was active, but did not match the Vishmit Enterprise data recorded in the PAN database. However, if the name is changed to Vismit Enterprise, without the “h”, the PAN key matches the name in the database. This shows that this PAN key is active.
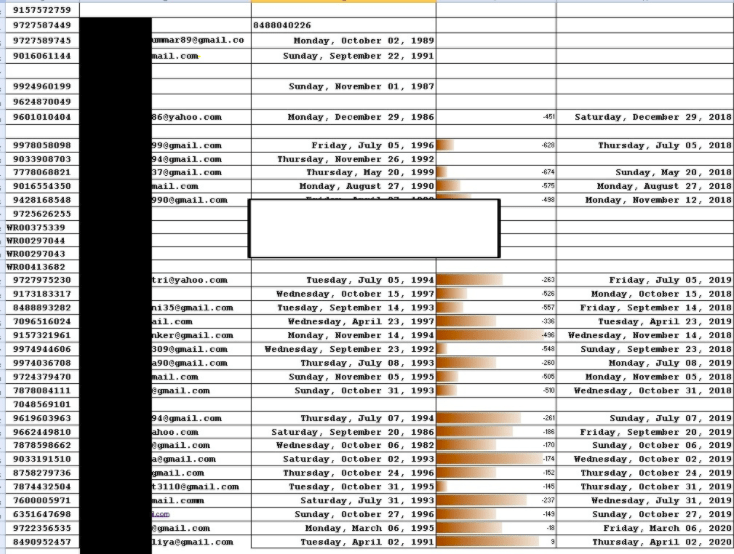
5. The hacker ensures that he has further evidence of his access to confidential documents. The latest screenshot published by Bassterlord contains confidential details such as phone numbers, email addresses, dates, and other details about companies not found on the Internet. The researchers took a sample of these phone numbers and found that they actually belong to some private companies in India, specifically in the State of Gujarat.
According to the forum where this information was published, Bassterlord has 14 reputation points on this platform and, so far, nobody seems to have filed any complaints against him. A striking detail is that, in less than a year, Bassterlord has positioned itself as one of the trusted members of the forum.
The hacker appears to have remotely accessed other systems on previous occasions. For example: on March 23, 2020, the user was selling remote access to some private companies in India. Due to its history, the researchers consider that the hacker is highly likely to sell legitimate accesses.
Based on the analysis, specialists suppose that the hacker actually gained access to the tax office server, exploiting some known vulnerabilities. The hacker mentions that 4 network devices have been compromised and a screenshot shows shared network drives. Therefore, the hacker may have made lateral movements to compromise other systems on the network.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
