Since its debut in 1996 under the stewardship of Daniel Stenberg, the curl tool has undergone significant evolutionary transformations, responding adeptly to the complex and shifting demands of network data transfer and security. As it journeyed through various developmental stages, curl became an integral element in data transfer protocols, indispensable to a multitude of users across different platforms and applications.
On October 5, 2023, Stenberg issued an advanced notification, shedding light on two noteworthy security vulnerabilities discovered within the confines of curl. One among the pair is branded with a “HIGH” severity tag, signifying its potential to inflict substantial damage, making it arguably one of the gravest security lapses identified in recent curl history.
Curl and its library version, libcurl, are instrumental in the realm of network data transfer, with curl serving as a command-line interface tool and libcurl acting as a supportive library, endowing various applications with the proficiency for executing network data transfers.
With adeptness in handling an extensive set of protocols – encompassing HTTP, HTTPS, FTP, FTPS, SFTP, SCP, TFTP, and others – curl has firmly established itself as a ubiquitous entity, extensively employed by individuals and organizations alike. It is a staple in a majority of Linux distributions and maintains compatibility with both macOS and Windows. Additionally, libcurl, with its multifaceted functionality, is deeply entrenched in numerous software applications, providing indispensable services to web browsers, download managers, and file transfer clients, to enumerate a few.
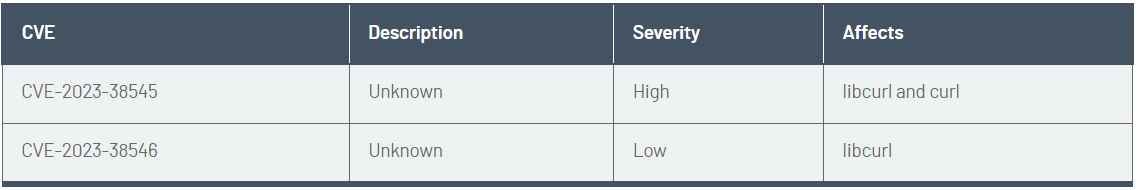
As the release of curl version 8.4.0 is on the horizon, meticulous details about the twin CVEs are slated for disclosure on the 11th of October, 2023. The vulnerability detected within libcurl is particularly disconcerting, given its prospective widespread ramifications. Nonetheless, the precise circumstances that would trigger this vulnerability are still obscured, complicating the endeavor to pinpoint the exact user base at imminent risk accurately.
To elucidate further, CVE-2023-38545 is a security vulnerability of considerable severity that simultaneously afflicts libcurl and the curl tool. While the threat it poses is undeniably substantial, it is imperative to acknowledge that it does not cast a wide net over all users. On the other hand, CVE-2023-38546 is designated as a vulnerability of lower severity, with its impact confined solely to libcurl.
As a proactive countermeasure, users are unequivocally urged to initiate an upgrade to curl version 8.4.0 at the earliest juncture post its official release. This expedited transition is not merely advisable but is an imperative protective maneuver designed to fortify user defenses against the looming threats embodied by these vulnerabilities. This imminent upgrade is essential, not just for leveraging the enhanced features it promises to deliver but more critically for erecting a robust security barricade capable of neutralizing potential breaches stemming from these newly unearthed security vulnerabilities.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
