We all know that due to ongoing crisis all over the world , this has led to destruction of the world’s economy due to very less output from the working staff that is now working from home . Lack of resources available online to that compared in the office environment posed many problem for organizations and private firms . Trying to reduce this problem , organization and agencies decided to connect with their employees and arrange meetings with them through a online video conferencing apps available in the market for example Zoom . It is a video conferencing app that lets you have a conference meet for 100 and more members at a time . This app helps the organization a lot but soon the black world started taking illegitimate advantage of this feature . There are many attacks by these attackers like recently discovered and become popular “Zoombombing” which lets an attacker to take over the meetings which are not password protected . There were a lot of issues on the company’s security and privacy mechanism to which Zoom is constantly taking to steps to improve that . But today in this article , we will not discuss security and privacy issues by the company but there is a insider product which is coming in the name of company i.e. Zoom . This insider product is nothing but a trojan which is packed inside by some hackers in “Zoom Installer” for Windows . Discovered by the researchers from Trend Micro , this installer comes with an attachment of Trojan.Win32.MOOZ.THCCABO , which is a trojan for windows platform . The black world cyber criminals are now taking advantage of this trojan to do coin mining from the infected system . Though this Trojan is packed inside the Zoom installer , but the official website for Zoom installer for windows does not contain this malware . This malware contained packet is sell by some fake websites which are run by cyber criminals .
ANALYSIS OF THE MALWARE
After successfully downloading the Zoom installer from fake sites , the installer file comes with the following sub-folders or files as shown below :
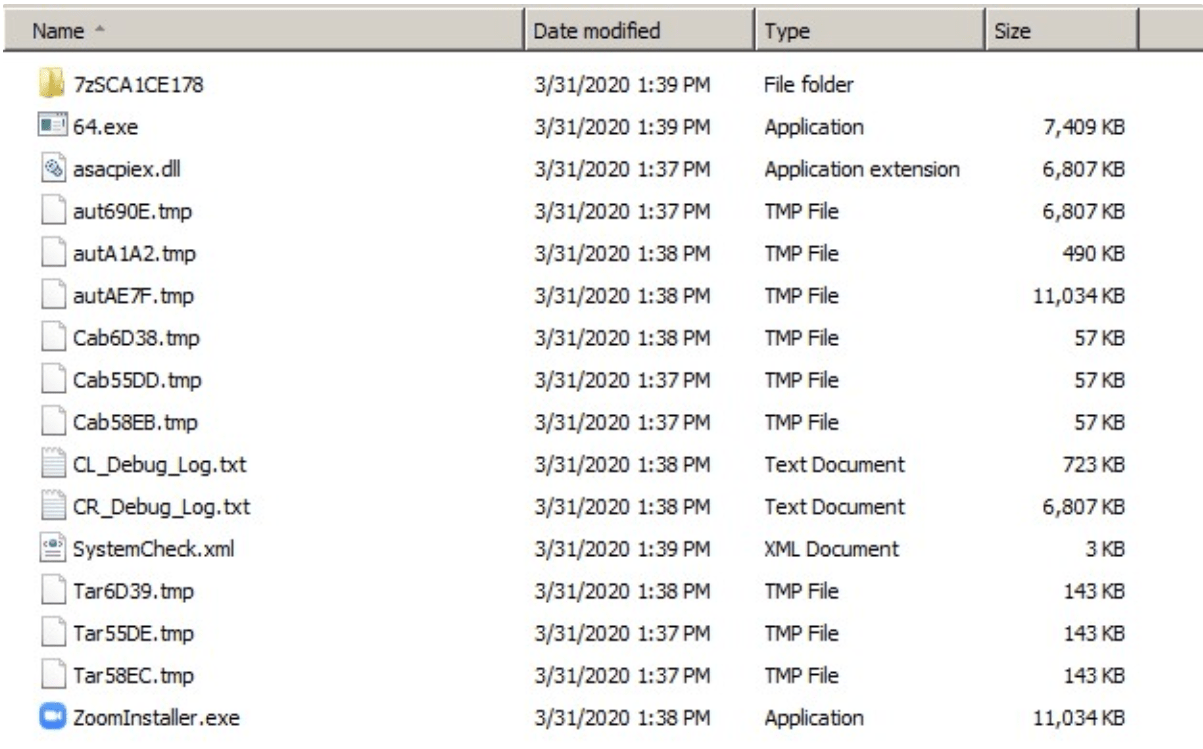
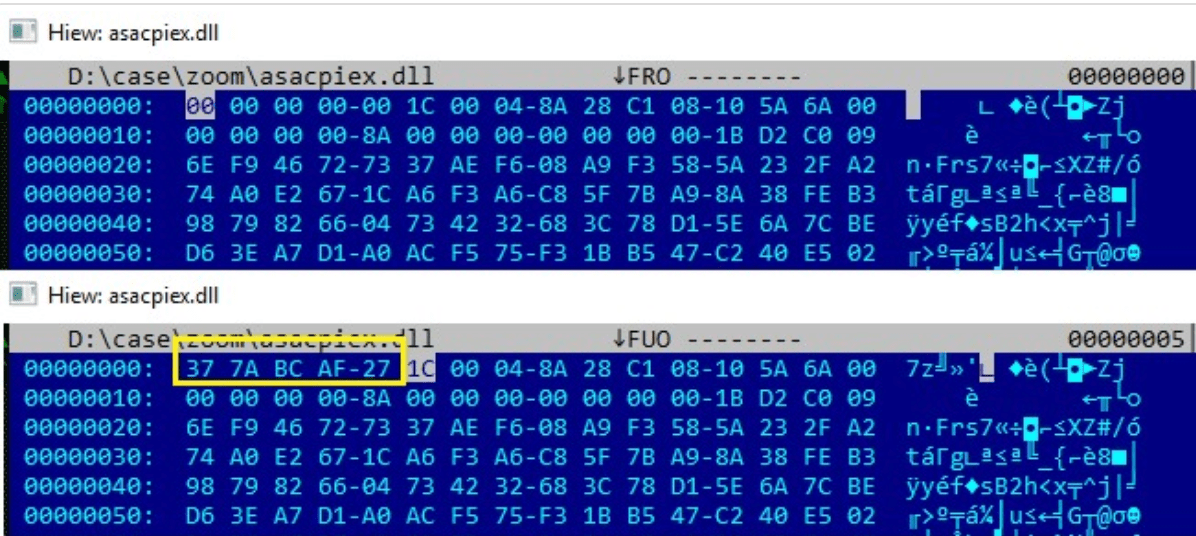
The file named asascpiex.dll in the above list is being signature-tampered to not get identified by any of the antivirus or Windows Defender. To do this , the first five bytes in the .dll file got replaced from 0x37 0x7A 0xBC 0xAF 0x27 to 0x000 which is identified as 7-Zip archiver file by the system and then coped as CR_Debug_log.txt which is then decompressed by the other 7-zip archiver in the same list as CL_Debug_log.txt.
The file CR_Debug_log.txt gathers some information such as Graphics Processing Unit using Windows Management Instrumentation (WMI queries), which is useful information for mining activities. It also collects details on CPU, system, operating system version, video controllers, and processors.
It also checks the antivirus running in the system and some details about the Windows Defender running in the system and send the details to the server hxxps://2no.co/1IRnc using HTTP GET request.
Finally after collecting all the details , CR_ Debug_log.txt then run its algorithms and determine the architecture of the infected system and if the system finds out to be x64 architecture then it drops payload 64.exe coin miner in the infected system by decompressing itself with the help of 7-zip archiver CL_Debug_log.txt . Luckily here , the x86 architecture benefits here as there is no payload for the 32 bit architecture in the installed file .
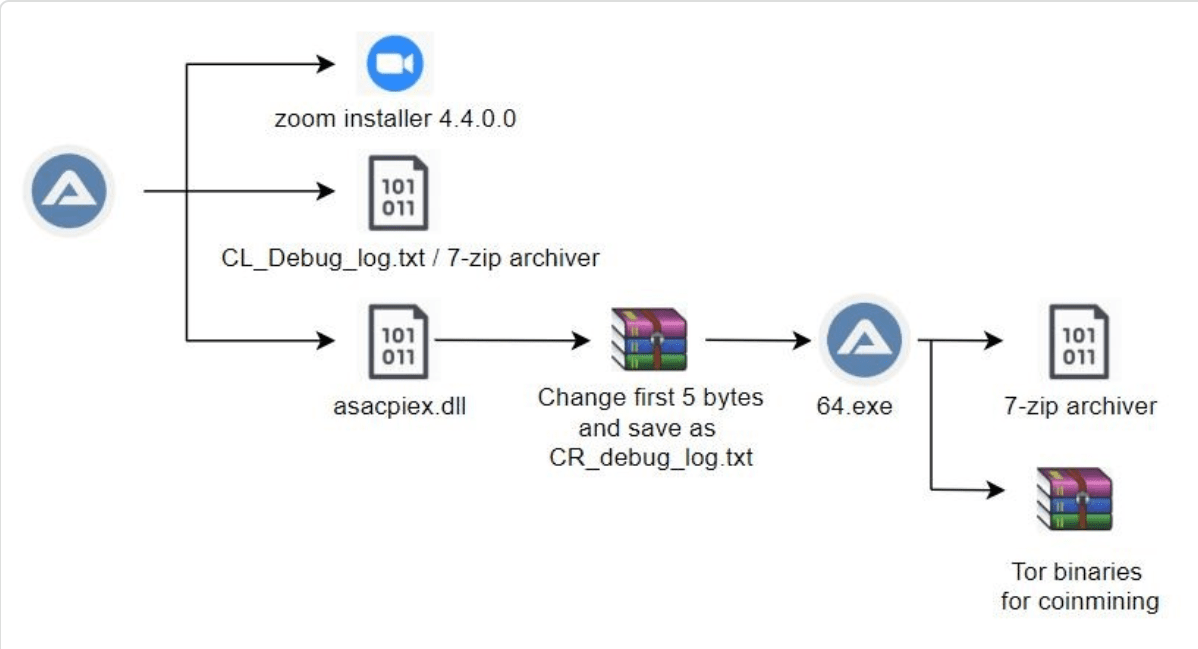
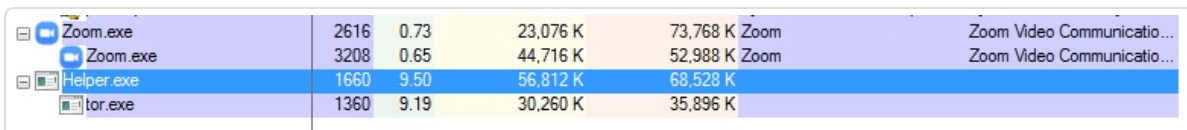
After launching itself , this autolt malware copies itself as helper.exe into the %appdata%\Roaming\Microsoft\Windows\ folder . This 64.exe file is an autolt malware contains 7-Zip archiver and a compressed Tor binaries that are password protected.
After the malware copies itself into target folder , it then schedule task with -SystemCheck argument to pretend as if it is just a utiltity to check all the windows process are running accurately or not but it also checks some processes that can help in coin mining also . Here is a list of windows process that it checks :
- aida64.exe
- AnVir.exe
- anvir64.exe
- GPU-Z.exe
- HWiNFO32.exe
- HWiNFO64.exe
- i7RealTempGT.exe
- OpenHardwareMonitor.exe
- pchunter64.exe
- perfmon.exe
- ProcessHacker.exe
- ProcessLasso.exe
- procexp.exe
- procexp64.exe
- RealTemp.exe
- RealTempGT.exe
- speedfan.exe
- SystemExplorer.exe
- taskmgr.exe
- VirusTotalUpload2.exe
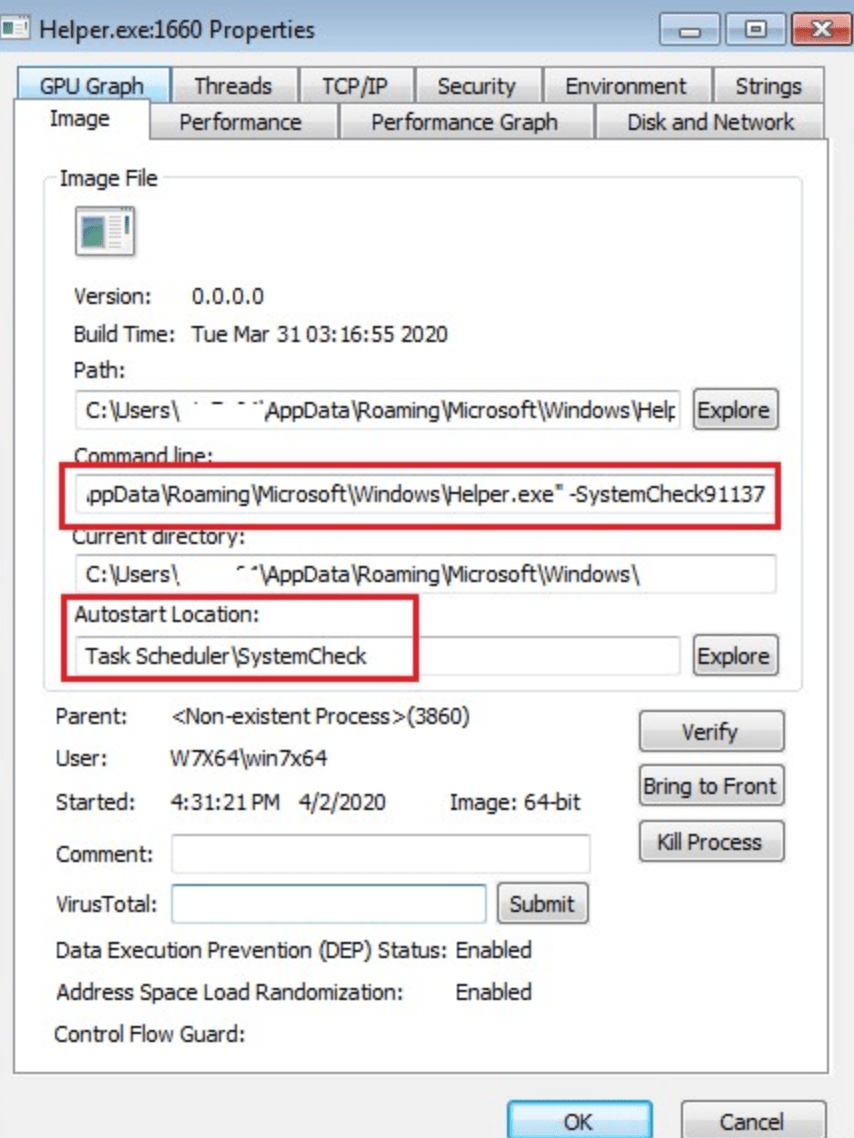
Once after the helper.exe started running , it hides itself under the SystemCheck91137 argument and it then decompress tor binaries with the help of 7-zip archiver inside 64.exe and then finally starts its desired purpose i.e coinming .
CONCLUSION
This coronavirus outbreak has forced many people and organization to work from home but the underground attacker are not leaving even a single chance to exploit these organization with their skills and resources . There were several phishing attacks which were discovered recently on small as well as big organizations . Recently a tool was also discovered by the team SecKC named zWarDial which is an automated tool for finding out the non-password protected Zoom meeting using the old phone-based war dialing programs that called random or sequential numbers in a given telephone number prefix to search for computer modems and has a success rate of 14 percent .
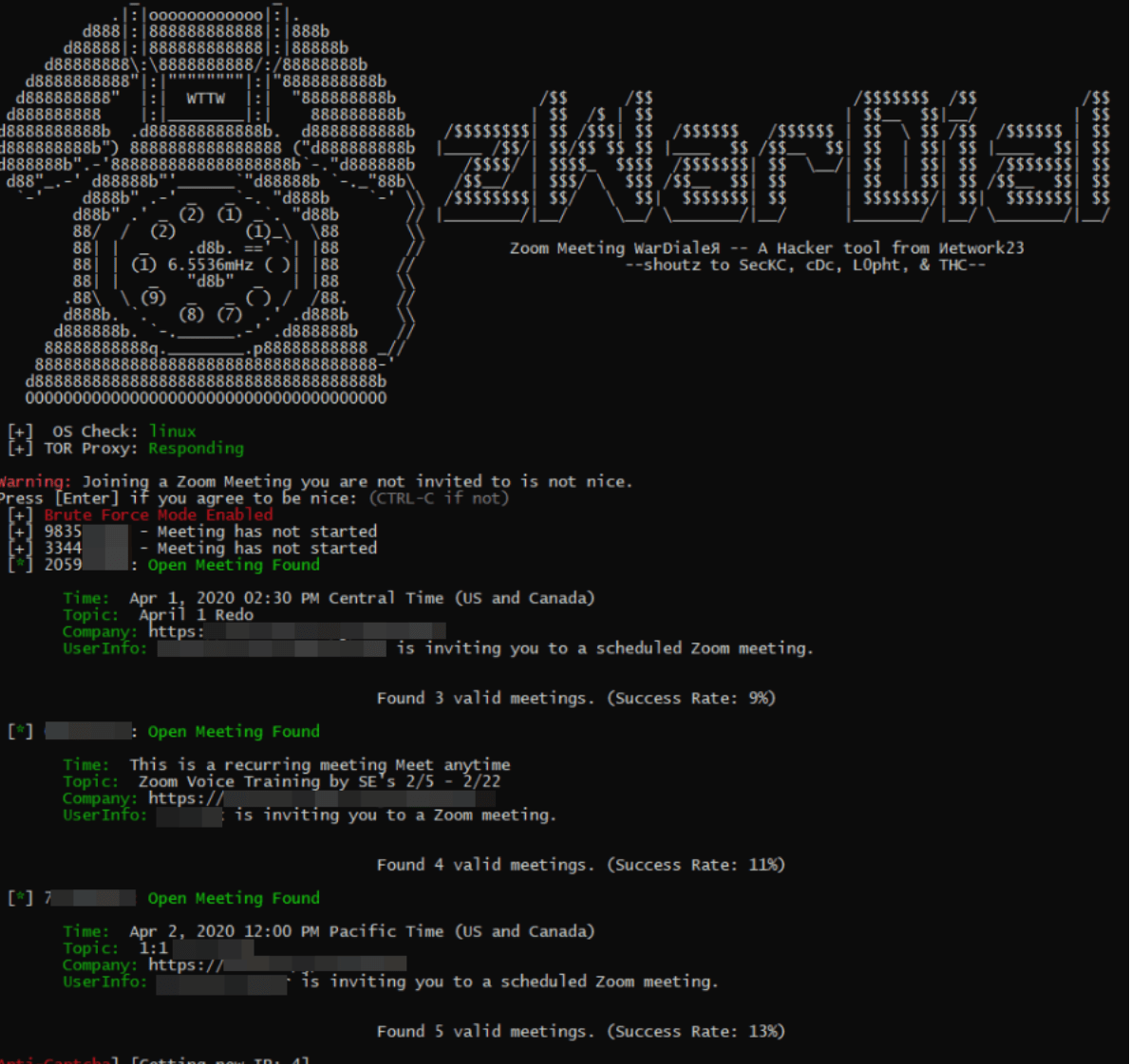
But luckily , the developers of this tool has not announced the source code for the tool publicly and so it cannot be used by normal script kiddies to do some unlawful thing . So as you can working from home is more a threat to organization rather than a help . Therefore , they can prevent attacks by :
- Downloading any software related products only from the officla site of the company .
- Keep your meeting password protected always .
- Do not share your Meeting ID and Password on Social Media.
- Make sure you are connected to a secure network .

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
