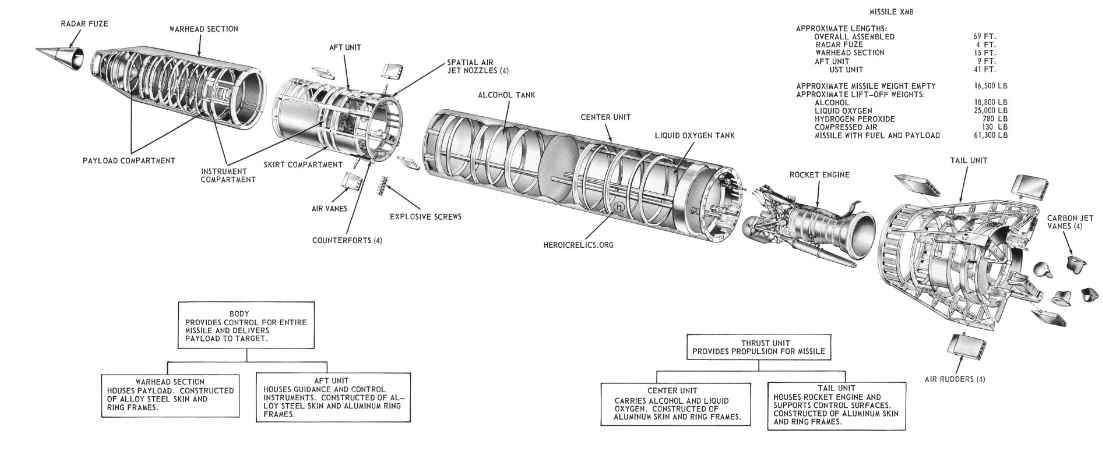
The threat actors associated with North Korea aggressively drew the attention of security specialists, exposing useful campaign insights during the course of the year. Five months ago, a crew of highly skilled North Korean hackers that belongs to the elite category entered covertly and in secret the internal networks of one of the most important Russian missile companies.
Researchers working in the field of information security for SentinelOne Labs have recently uncovered evidence suggesting that North Korean hackers into the private networks of a prominent Russian firm that specializes in missile and military engineering.During the investigation into North Korean threat actors, analysts from SentinelOne Labs found a DPRK-linked implant in a leaked email collection. This discovery led to the discovery of a bigger previously unknown infiltration.
NPO Mashinostroyeniya, a Russian company that manufactures missiles and spacecraft and has classified missile technology that is sanctioned and held by JSC Tactical Missiles Corporation KTRV, is the firm that is being targeted.The data breach resulted in the exposure of emails that are unconnected to each other, suggesting that the breach was either inadvertent or unrelated. Nevertheless, it is a rich source of information about the following things:
Security loopholes in the network design
Additional attackers
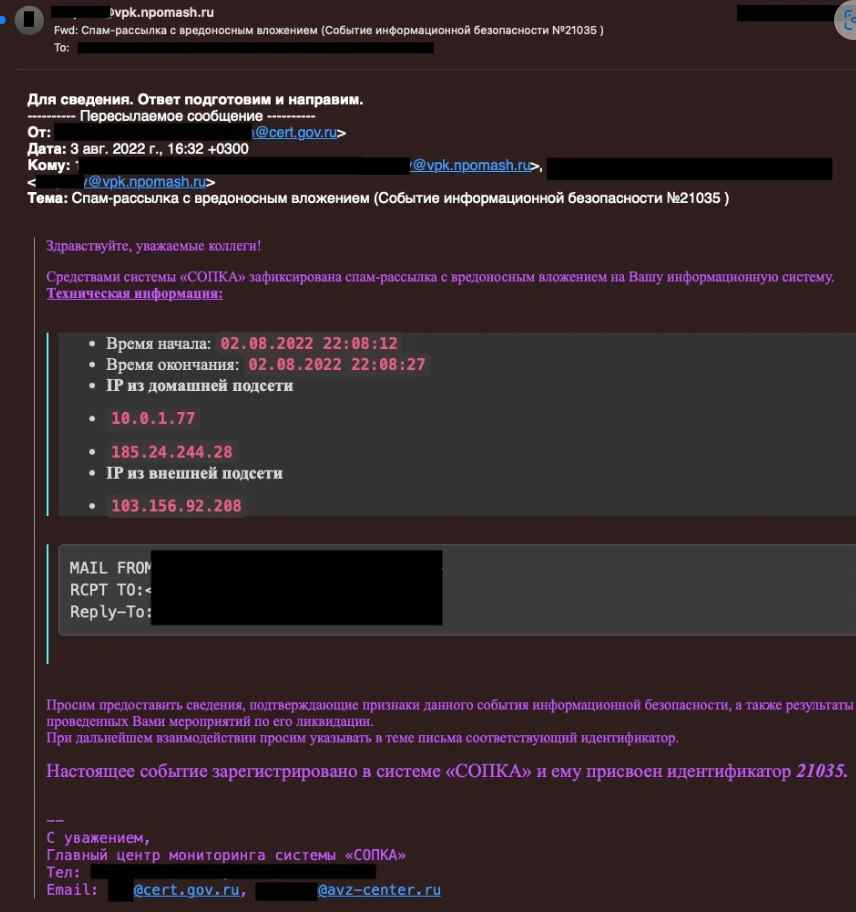
Emails from NPO Mashinostroyeniya disclose talks among IT workers about potentially malicious communications and DLL files. Following the breach, they contacted AV assistance in order to fix detection difficulties.
Email communications between employees of NPO Mash (Source: SentinelOne Labs)
The OpenCarrot Windows OS backdoor, which has been connected to the Lazarus gang and identified by specialists, allows for complete system penetration as well as network-wide assaults with proxying C2 communication.
In this instance, the examined OpenCarrot was used as a DLL file. OpenCarrot is intended for persistence and incorporates more than 25 Lazarus group backdoor commands that have a variety of features.
Because North Korean threat actors lack OPSEC, it is possible for researchers to acquire novel insights on operations that have not been published and monitor the progress of campaigns via infrastructure linkages.
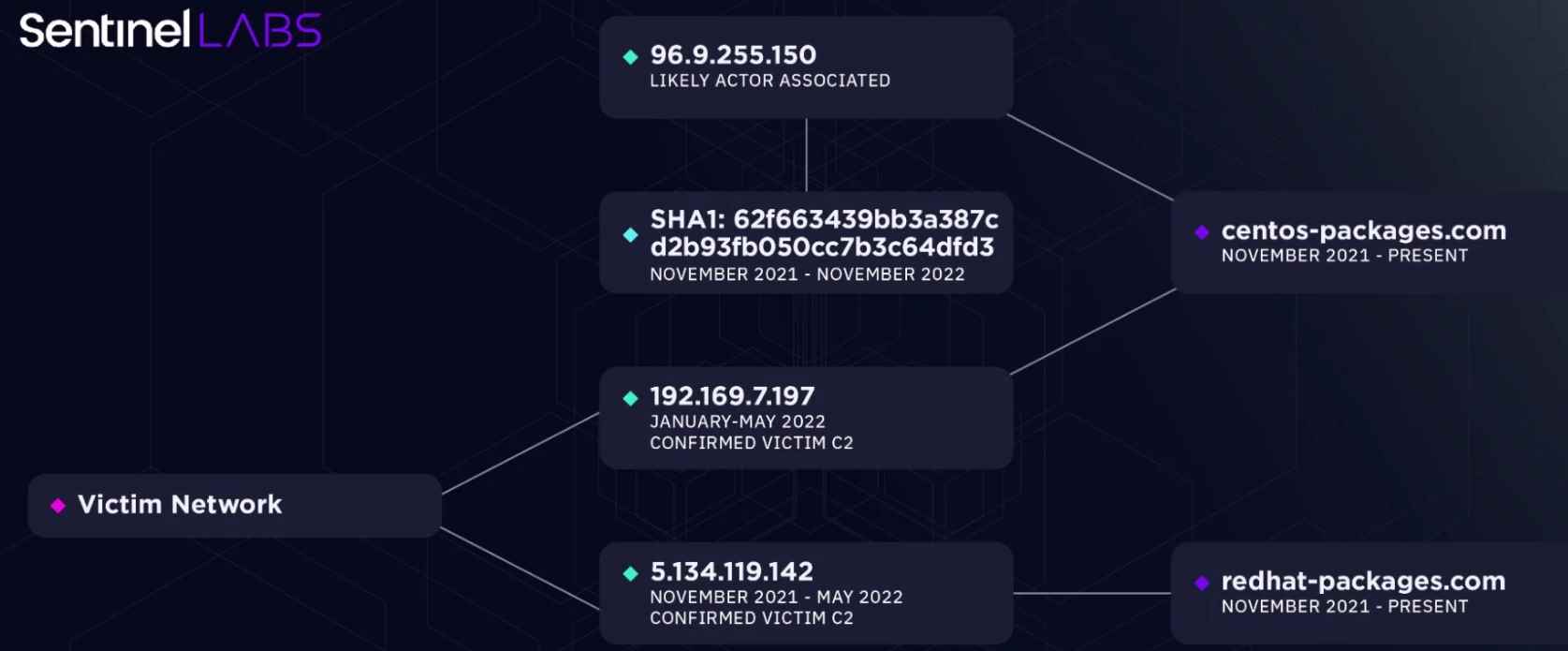
The experts saw domain theme parallels between JumpCloud and NPO Mash, which led them to conclude that the breach was carried out by North Korean threat actors.
Despite the fact that it is not conclusive, it piques one’s interest about threat actor infrastructure building and management methods, in addition to additional linkages.Security experts are confident in their attribution of the breach to threat actors affiliated with North Korea. This demonstrates North Korea’s clandestine missile development ambition via the direct hacking of a Russian Defense-Industrial Base (DIB) organization.
The convergence of North Korean cyber threat actors constitutes a danger of enormous proportions that calls for extensive surveillance on a worldwide scale. These actors continuously engage in a wide variety of campaigns that are driven by a variety of different variables, and they do so while operating in sync as a coherent cluster. In light of these results, it is very necessary to address and work toward mitigating this danger while maintaining the highest vigilance and responding strategically.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
