Mobile security specialists revealed the finding of a severe vulnerability in MX Player, a media player app available on the Google Play Store that has over 500 million downloads. According to the report, exploiting the fault allows remote code to be executed on the target system, leading to a full compromise of the device.
Unlike other media player apps, MX Player’s vulnerability is not exploited by sending malicious or malformed files, but the attack requires abusing the video sharing feature. Researchers successfully exploited the flaw and notified the developers, who corrected this condition with the release of version 1.24.5.
MX Player users can transfer video files between two devices, setting up a receiving computer and an issuer, which is authenticated using a shared password, initiating the connection. Files received in this way are stored in an automatically created directory (/sdcard/MxShare).
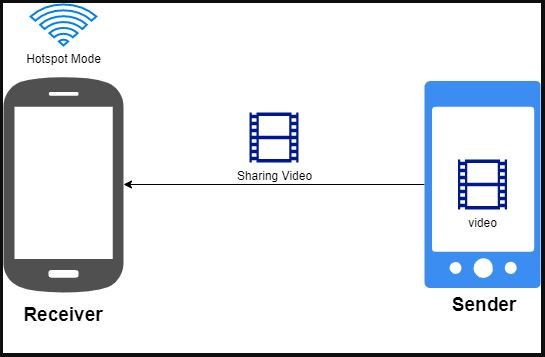
When the receiving device user enables “Hotspot Mode”, the password is encoded on base64 and publicly presented as a recognizable Bluetooth device.
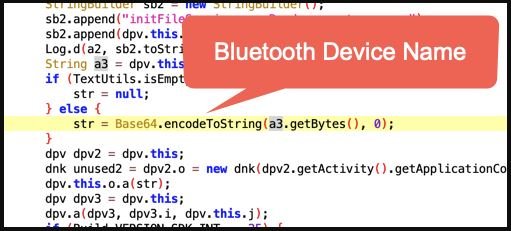
If a threat actor locates the receiving user’s Bluetooth, the password could be compromised, triggering various risk scenarios.
The protocol presents several commands throughout the transfer process. One of these commands tells the application the file name to save the incoming file.
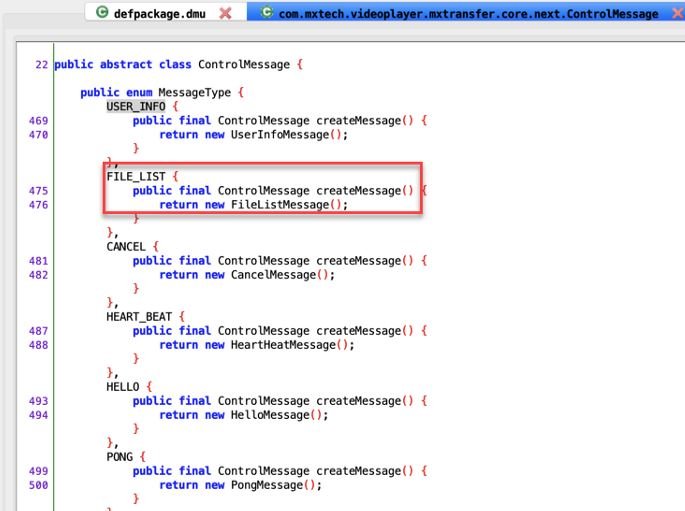
By reverse engineering the application code, you can find the part where this application processes the sharing protocol. Here we see that the command responsible for processing the file name is “FILE_LIST”, when this message is received through the transfer protocol, parameters are taken that tell the application how to save the file.
The expected message would be displayed as:
‘mx-x00-x01-x00-x02-x00-x00-x00-xb5-“hash”:”FA730A013D17D705CAF504B5CA560501″,”id”:0,”name”:”cool_video”,”suffix”:”mp4″,”size”:5976,”type”:0’
The flag “x01” after the header “mx” is the command FILE_LIST, while the following JSON text contains a field named “name”. If the message is received during the transfer of a file in MX Player, the name will be taken and concatenated into an encoded path of “/sdcard/MXShare/”.
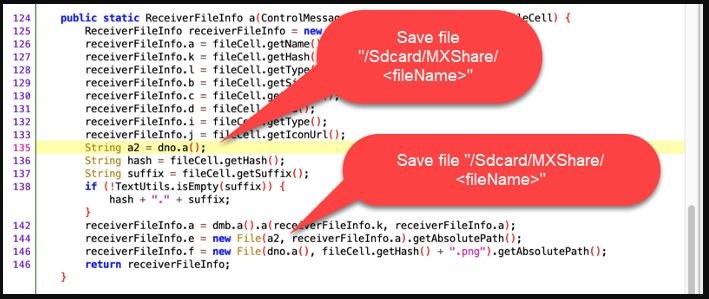
Here you can see the problem, which consists of the ability to perform a path traversal if the name of the pasad file is “../../traversedFile”.
Therefore, when sending a message like the following:
s.sendall(b’mx-x00-x01-x00-x02-x00-x00-x00-xb5-“hash”:”FA730A013D17D705CAF504B5CA560501″,”id”:0,”name”:”.. /cool_video”,”suffix”:”mp4″,”size”:5976,”type”:0-
The video could be stored outside the default location and directly in the root directory of the device’s memory card.
When the user enables receiver mode in an MX Player transfer, a threat actor can connect to the phone remotely in order to interact with the MX transfer protocol to deploy an executable .odex file to /data/data/com.mxtech.videoplayer.ad/files/oat/<arch>/audience_network.odex (as well as .vdex). The MX Transfer protocol can support sending multiple files in a transfer session, so creating a message FILE_LIST as seen below, both files in the paths for execution will be successfully deleted the next time the application runs.
As mentioned above, successful exploiting of the vulnerability would allow remote code execution. MX Player users are strongly encouraged to upgrade to the latest available version of the app.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
