Mordechai Guri, a well-known researcher from Israel’s Ben-Gurion University of the Negev, created the GAIROSCOPE attack method, which uses smartphone gyroscopes and ultrasonic tones to steal data from air-gapped devices.
The threat actor must have planted malware on the air-gapped system in advance, as well as on a smartphone that must be close to the air-gapped system for the attack to succeed.
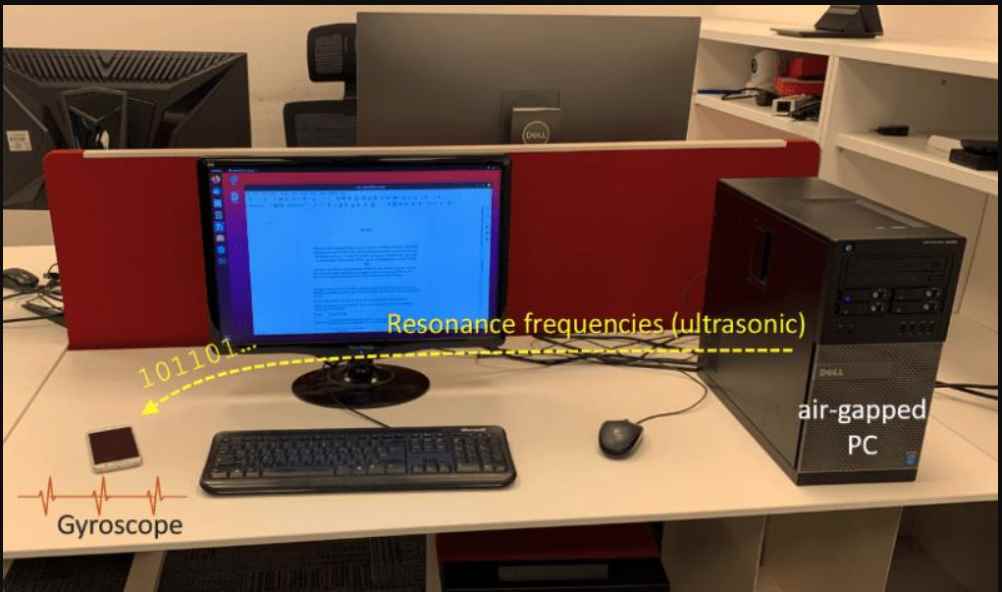
In order to cause small mechanical oscillations within the smartphone’s gyroscope, the malware placed in the air-gapped system emits ultrasonic tones in the resonance frequencies of the MEMS gyroscope.
The study emphasized that, in contrast to other parts like the microphone, the gyroscope in smartphones is thought to be a “secure” sensor and may be used lawfully from mobile apps and javascript without additional authorization.
The researchers also noted that unlike other sensitive sensors, Android and iOS may not provide users with any visual cues, notification icons, or warning messages when an application is exploiting the gyroscope.
“Our tests demonstrate that hackers may use the Speakers-to-Gyroscope covert route to transfer private data from computers that are air-gapped to cellphones that are a short distance away” reads the study’s findings.
Frequency-shift keying is used to encrypt sensitive data collected by the malware on the air-gapped system. In frequency-shift keying (FSK), the carrier wave’s frequency is changed to reflect the data.
The infection then transmits the noises at the inaudible frequencies using the computer speakers.
On the other end, the gyroscope of the smartphone is used to pick up the noises, and malware operating on the smartphone continually samples and analyses the gyroscope’s output. The virus demodulates and decodes the data when it discovers an effort at data exfiltration that was launched using a certain bit sequence. The attacker can then use the phone’s internet connection to send the exfiltrated data to them.
“In the exfiltration phase, the malware encodes the data and broadcast it to the environment, using covert acoustic sound waves in the resonance frequency generated from the computer’s loudspeakers. A nearby infected smartphone ‘listens’ through the gyroscope, detects the transmission, demodulates and decodes the data, and transfers it to the attacker via the Internet (e.g., over Wi-Fi).”. “The air-gapped workstation broadcasts data modulated on top of ultrasonic waves in the resonance frequencies that oscillates the nearby MEMS gyroscope. The application in the smartphone samples the gyroscope, demodulates the signal, and transmits the decoded data to the attacker through Wi-Fi.”
The researcher’s experiment showed that the GAIROSCOPE technique permits data transfer at a maximum rate of 8 bits/sec across a range of up to 8 meters.
In addition, the researcher offers defenses against the GAIROSCOPE attack, including speaker removal and blocking, ultrasonic filtering, signal jamming, signal monitoring, putting sensors under security, and putting keping systems in restricted zones with various radiuses, according to the zone classification.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
