Introduction
Now we can do Digital forensic on any windows machine by using this Dfirtriage Forensic tool. We use this tool on compromised windows machine to verify whether any malware or any payload is running on the machine, or hacker might have installed Rootkit on your Windows machine. This will scan the complete windows machine and generates a report file for the end user. This tool is built on python language.
Environment
- OS: Microsoft Windows [Version 10.0.18363.836]
- %PROCESSOR_ARCHITECTURE% : AMD64
Installation Steps
- Use this link to download the Dfirtriage tool https://github.com/travisfoley/dfirtriage/archive/master.zip and extract the file.
- Next, copy the file path and open the command prompt with administrator privileges. Move to file path using the cd command.
- Now, launch the tool by executing this command DFItriage.exe
- This tool is single command execution tool
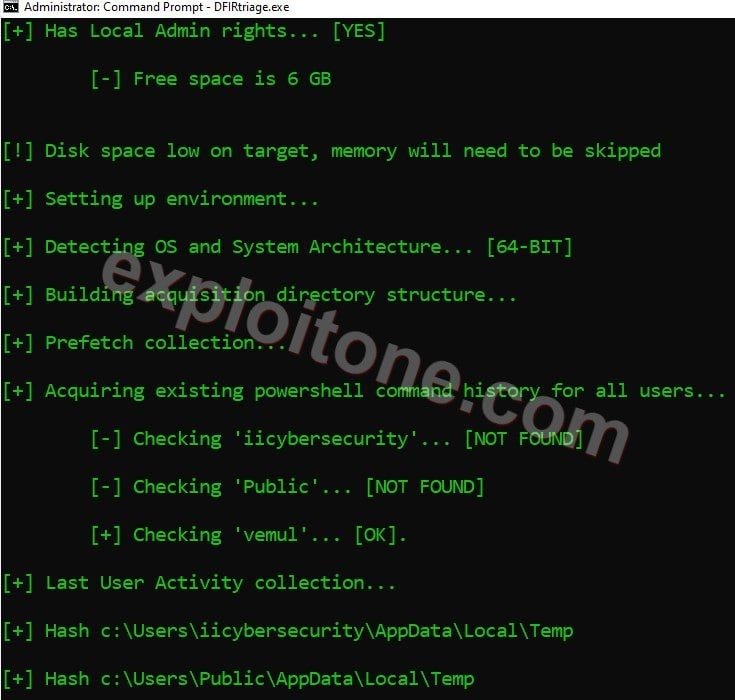
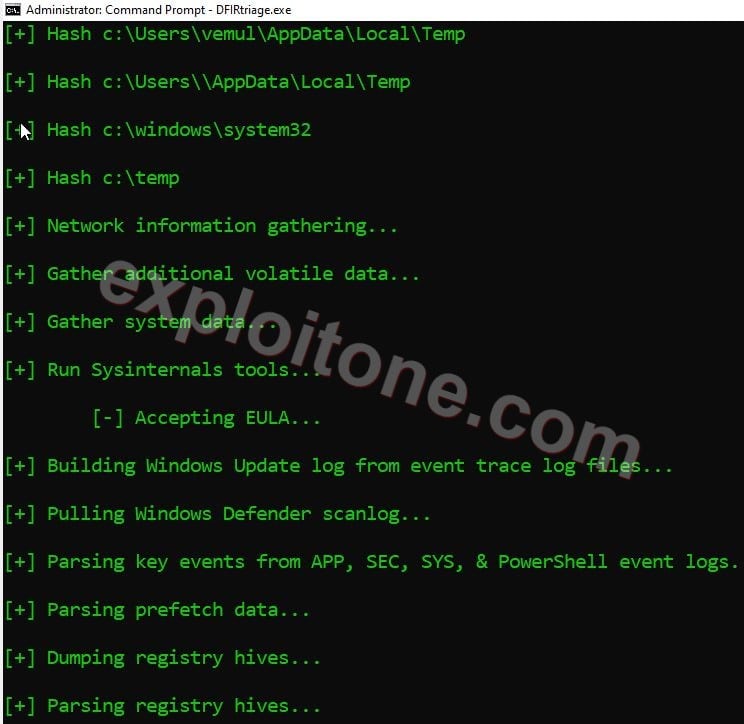
- After firing this command, it starts collecting all the system data like system information, Network information, Powershell command history, NetBIOS information, System32 and converts system files into hash files.
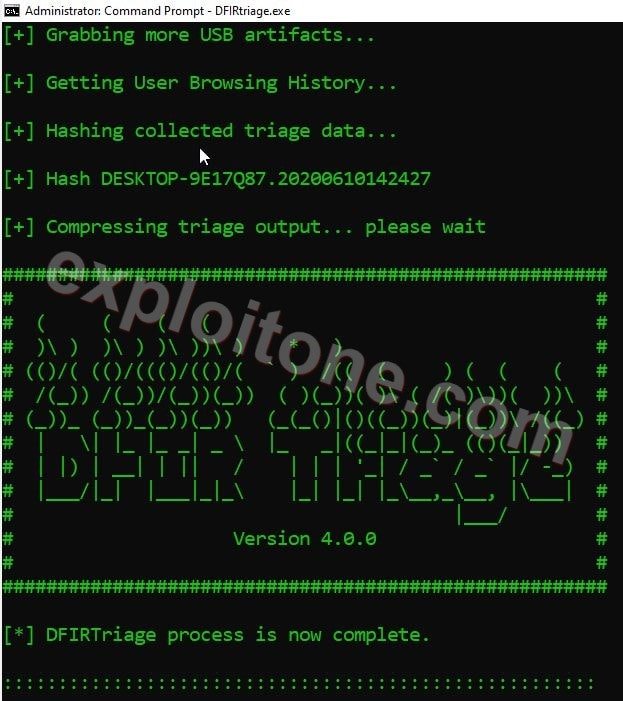
- After complete scanning it will generate a report in zip format. When we extract the report file, we can find four different files Forensic Images, LiveResponseData.Zip, Triage file collection hashlist.cvs and Triage into.txt.
- Now, Extract the LiveResponseData file to view the data files.
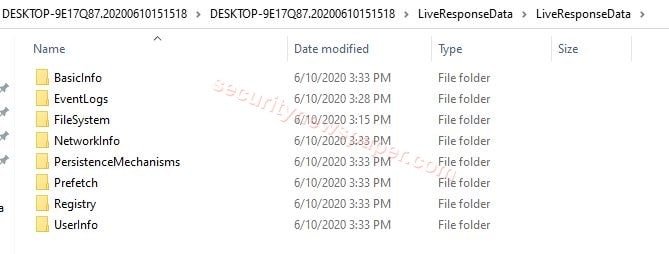
- Here, we can see the complete reports of our system logs.
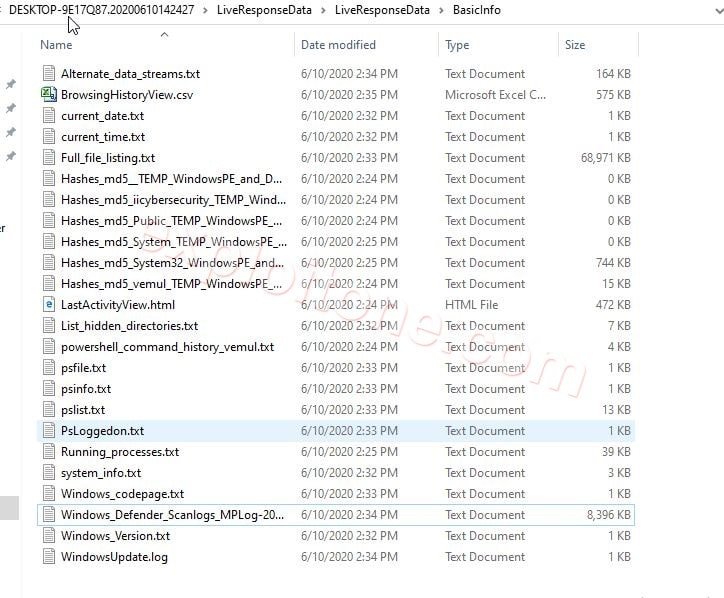
- Basic Info: In the Basic info we can find the information about our system information like Windows Defender Antivirus details (RTP Real-Time Transport protocol details) RTP is used for communication purpose, MPFilters (Microsoft Malware protection by Microsoft details) Mpfilter is used in protecting the Microsoft from knowing malware, internet Browsing History, system file which is converted into the hash, Hidden files in our machine, Powershell commands History and other basic information.
- EventLogs: EventLogs are the records of our windows machine, security, and application notification. All these files will be stored in an event log file. All windows system administrators use this for resolving the system problems.
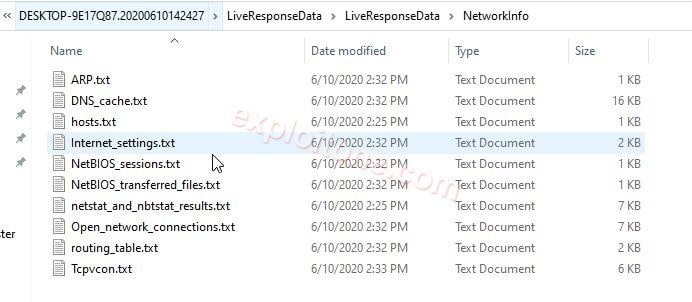
- NetworkInfo: In this folder, we have complete internet connection details like:
- ARP: Address resolution protocol. The main aim of arp is to convert internet addresses to physical addresses. In the arp report we have internet and physical addresses are stored
- DNS cache: the main aim of DNS cache to capture the previous DNS Lookup and this refers to temporary storage. In the DNS cache, we have the previous cache data.
- NetBIOS sessions: Network-based input/output system we use this program to communicate between two different computers in a LAN (Local Area Network). In NetBIOS sessions, we can check any connection details.
- NetBIOS Transferred: In Network-based input/output system transferred we can view the previous transactions.
- Netstat: Netstat is a single command line. The main aim of this command to display the network connections for TCP.
- Nbstat: Nbstat is used to verify the problems for NetBIOS over TCP/IP
- Routing table: The main aim of the routing table is to forward the data packet from source to destination. In this routing table report, we can see all the source and destination IPv4 address.
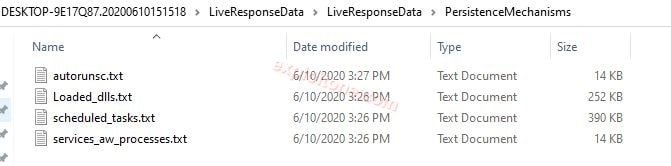
- PersistenceMechanisms: The data which is stored in windows hard disk that called PersistenceMechanisms
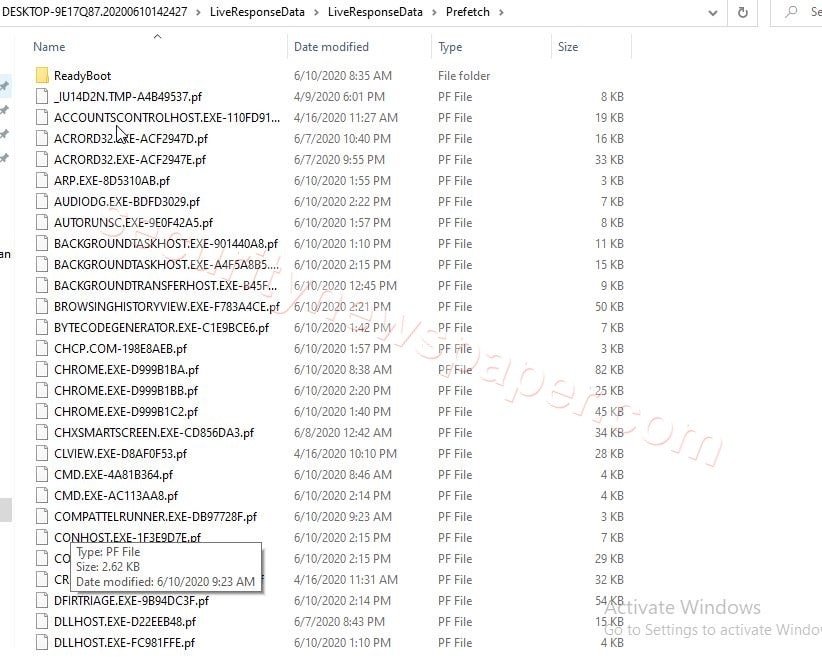
- Prefetch: In prefetch, the log file contains all the application which we have executed in our windows machines.
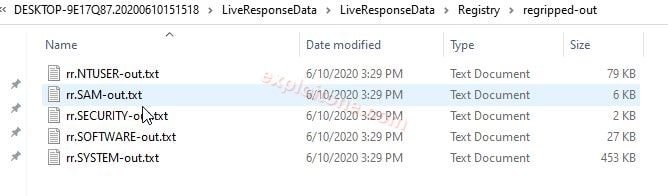
- Registry: The Windows registry is the place where all the system data both hardware and software stored in it just like a database.
- RegRipper: The gripper in as forensics tool, we use this to extract the data very quickly from the registry.
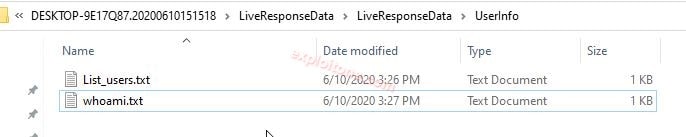
- UserInfo: in this we can view the number of users in our machine.
- Perform the scan more then one time for better results.
Conclusion
We saw how we can do forensic of any windows machine and retrieve the data to protect system from future attacks.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
