Introduction
In this smart world if we are connected to the internet we can find many types of details using a google search engine. Google is used for everything to find out the details about any topics which we don’t know or having any type of confusion in it and now using the same search engine we can find out some sensitive information called google dorking
Google hacking is also known as Dorking. Google hacking is a passive information gathering or footprinting technique that is used to extract information about vulnerabilities data exposure and security misconfiguration in websites which stored on a server
It involves using specialized search query operation to find out the right results based on what you are looking for, By some advanced operators like (inurl, filetype, intitle) using this advanced operators we can find out some information which is openly connected to the internet it may happen in a different way like mostly The first is when the server or other service is configured incorrectly, and administrative logs are available via the Internet. In the event of a password change or failure during authorization, account leakage through these logs is possible. The second scenario is when configuration files containing the same information become available. It is assumed that these files are for internal use only, but often confidential information is available in cleartext. Both of these scenarios allow you to gain control over the entire deal if an attacker manages to find the files of this kind
FIND OPEN FTP SERVERS WITH GOOGLE HACKING
- Now We use the dork to search for FTP servers available after 2018. These servers allow you to find out the files of internal use but unknowingly ended up in public access. intitle:”index of” inurl:ftp after:2018. This URL will list out only FTP servers
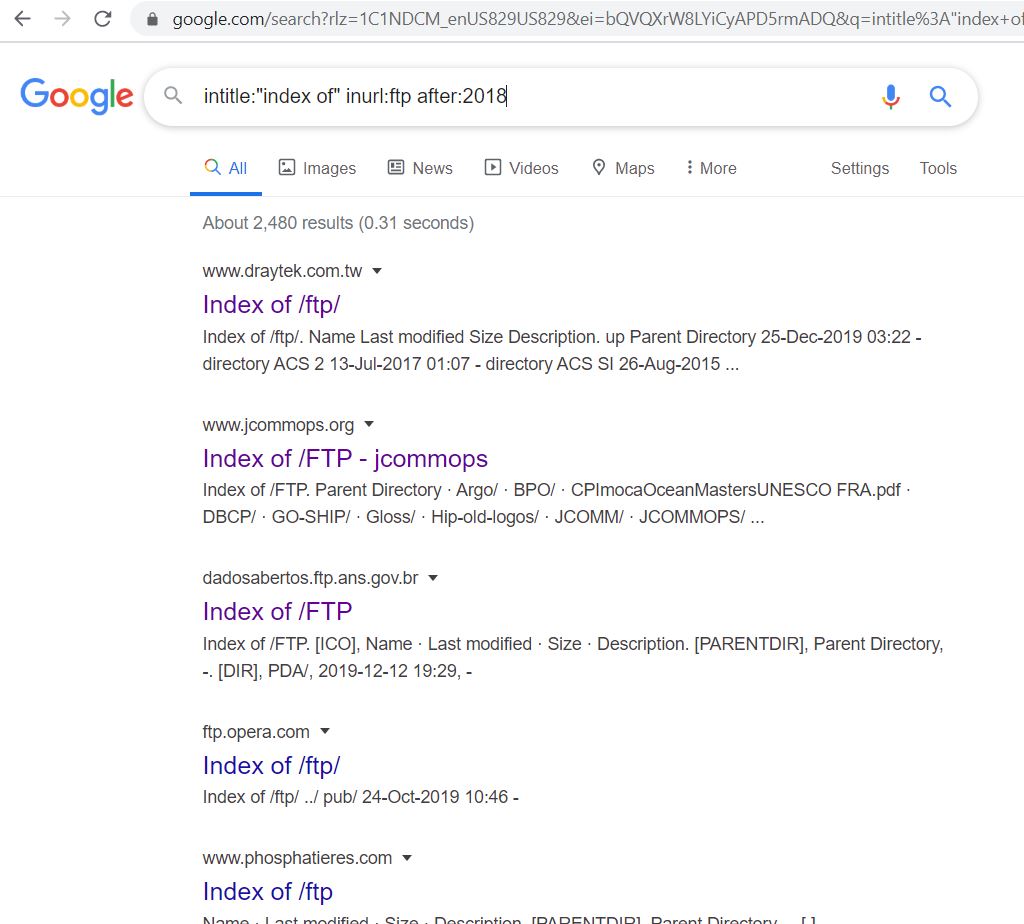
- Now click on any link from that FTP pages, Let’s see any data is available or not
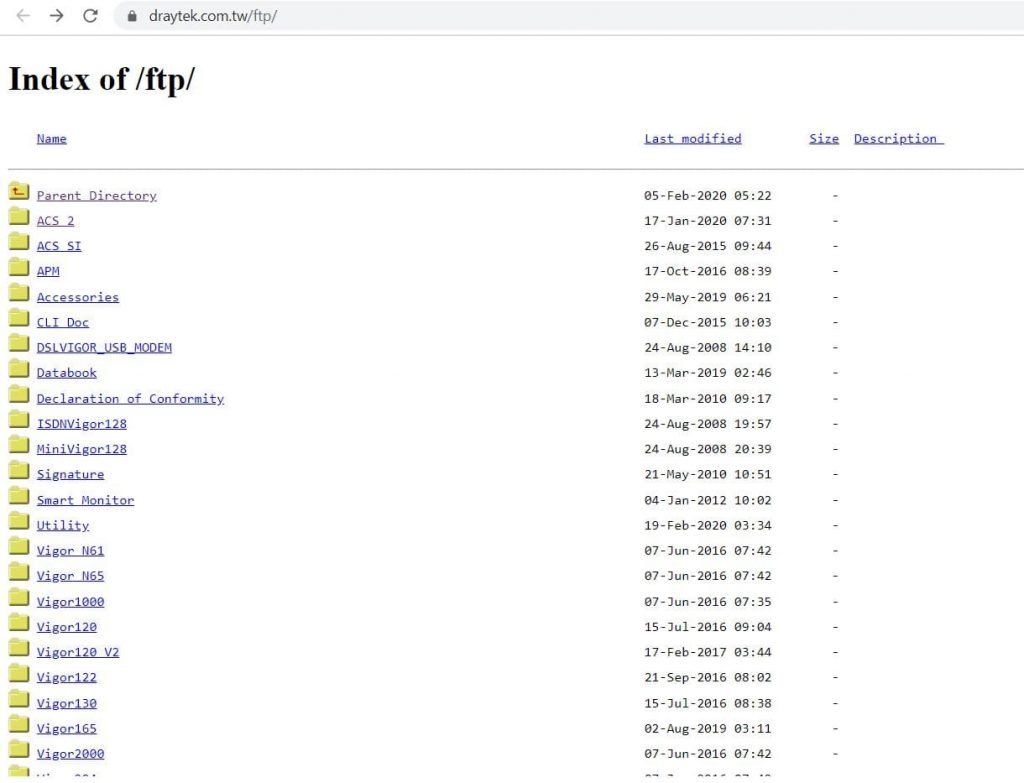
- Yes, we see some data on this.
- Next, let’s open this FTP Files. Let’s check whether we can any confidential information

- Yes. we see some confidential information. If you click on any link in this we can download and see the content in this files
FIND UNSECURE WEBSITES WITH GOOGLE HACKING
- If we want to find out insecure HTTP pages, we have to modify the request above by changing “FTP” to “HTTP” intitle:”index of” inurl:http after:2018. This URL will list out only unsecured HTTP pages, In this results, we can find hundreds of HTTP pages and ready to compromise
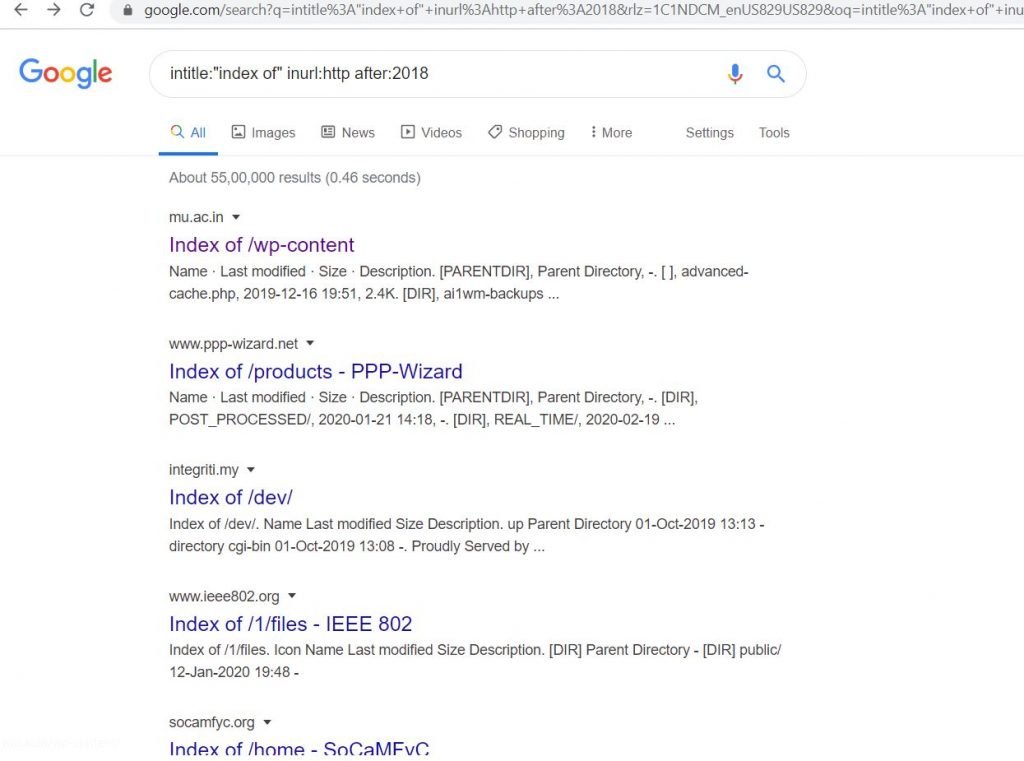
- Now click on any link from that HTTP pages, Let’s see any data is available
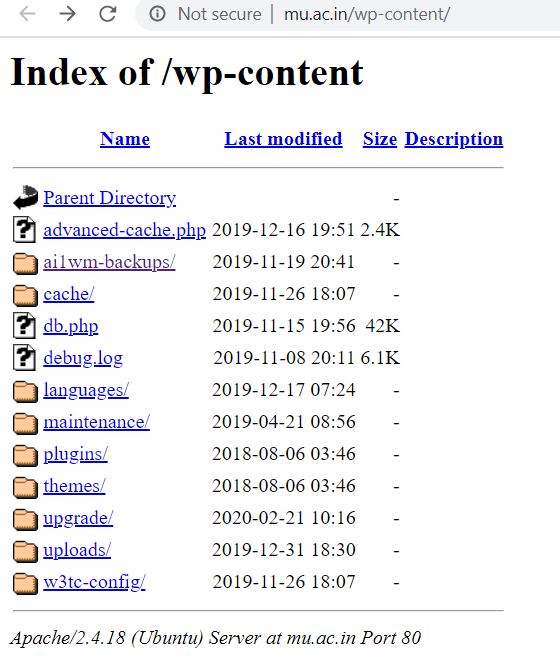
- In the above picture, we see some file containing confidential data in it
Search Logs For Passwords
- Passwords that are available in internet allintext:password filetype:log after:2018. when we use this URL we can see password list in plain text
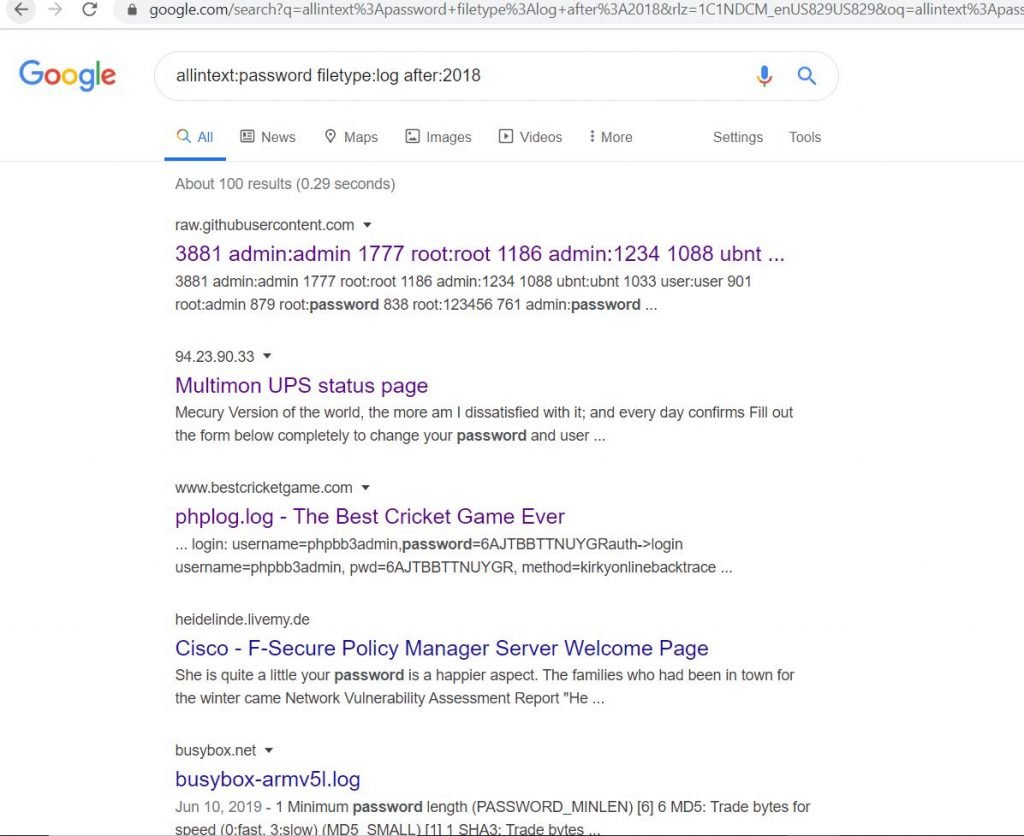
- In the below picture we login details for links we directly download the data and we can search in that file
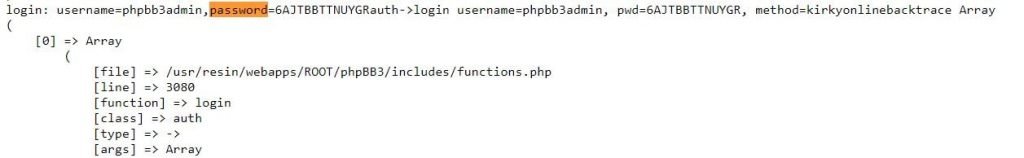
Search For Configuration Files With Passwords
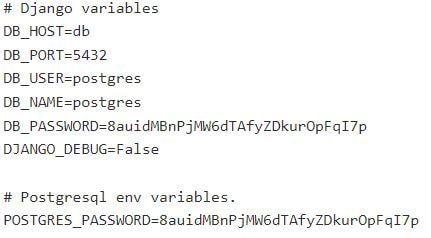
- Configuration files should never be accessible externally. When we use this URL we can find some password and database. filetype:env “DB_PASSWORD” after:2018.
- Now, Let’s click on any link whether we get the password list
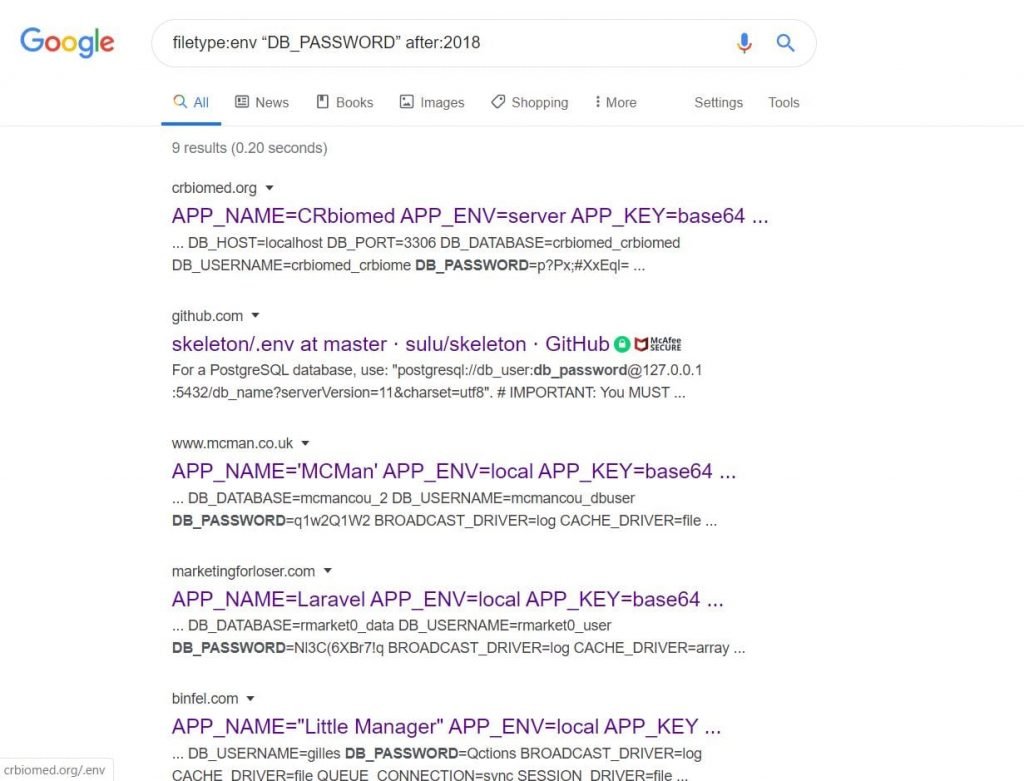
- Yes we found login details
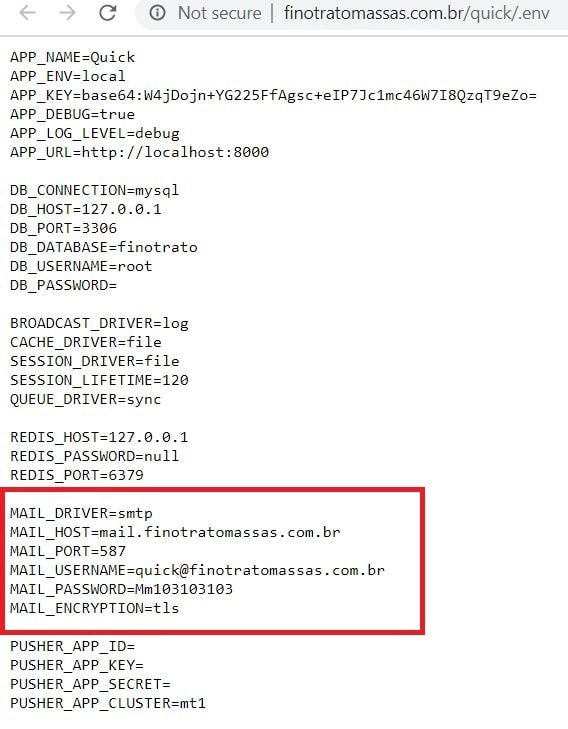
- In some cases, we see invalid URL or Any error, in that case, click below arrow after the link we see the cached option click on it then we can see the data
- In the below picture we see another login credentials
Finding Emails From Google
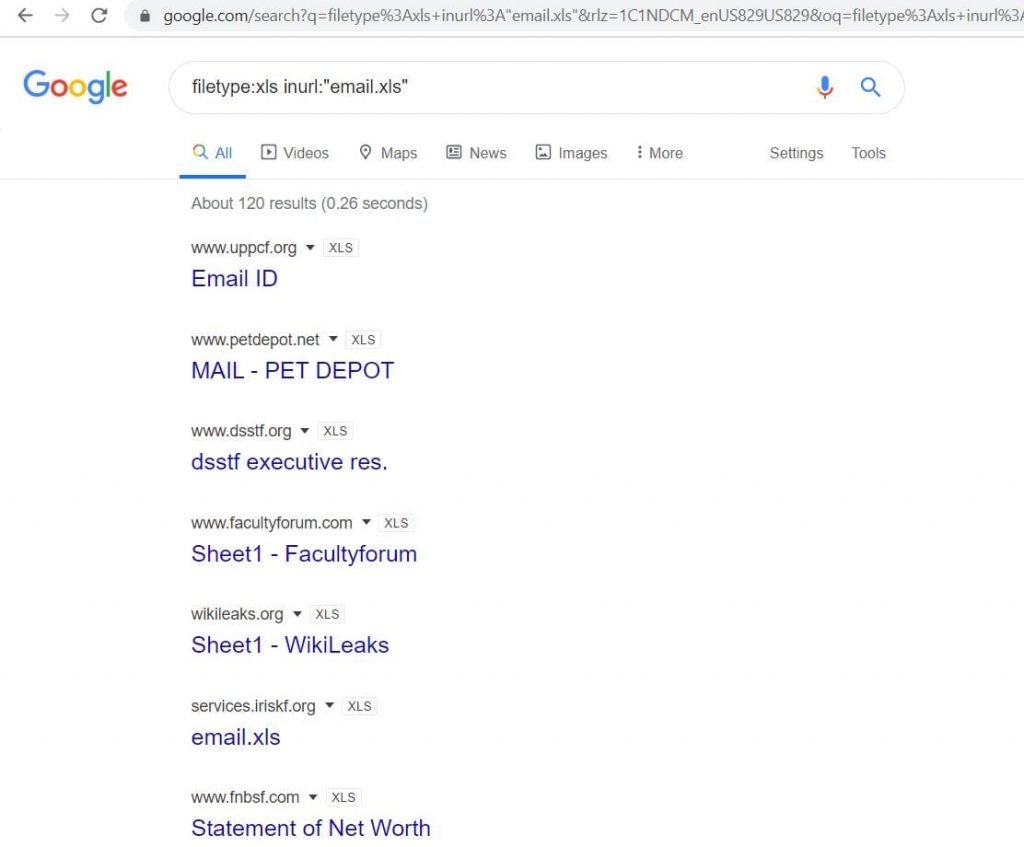
- We will search for e-mail lists in spreadsheets (files with the .XLS extension). In the search query inside the URL, set the file name “email.xls” this will Be Collecting email lists is a great way to find information about various organizations. Use filetype:xls inurl:”email.xls
- Now we see Email pages in the above picture, if we click on those links we can directly download the email list.
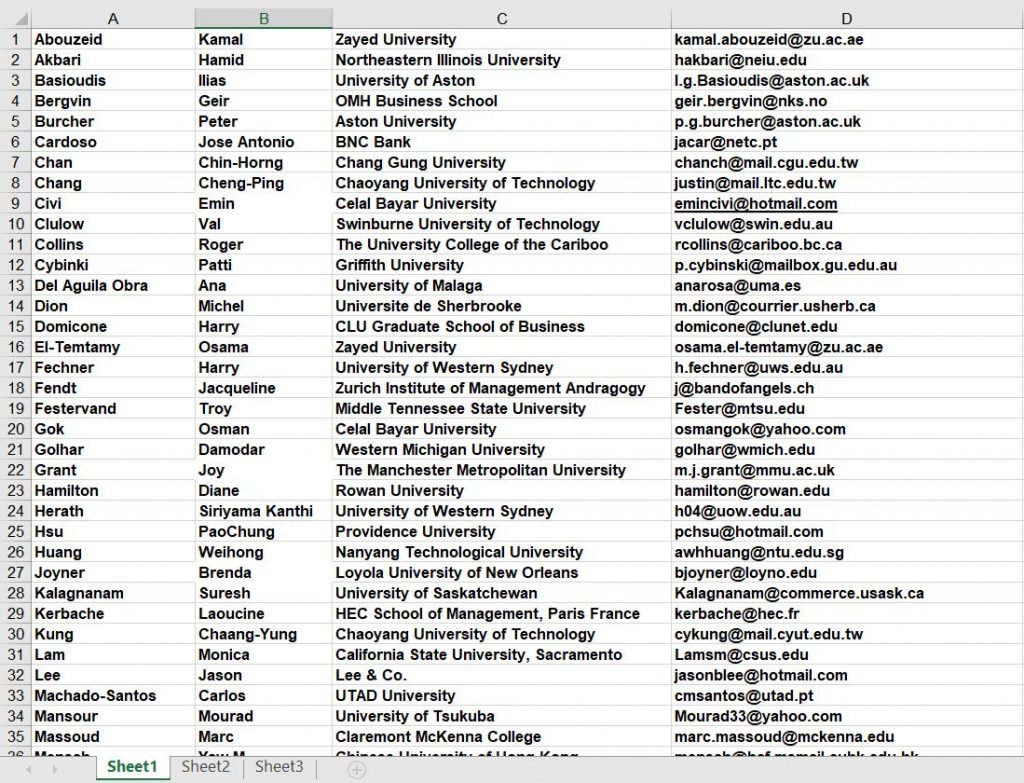
- In the above picture, this is the data I have downloaded we see the data in the spreadsheet.
HACK CAMERAS USING GOOGLE
- We can access the camera via HTTP pages One of the most common queries contains the name “top.htm” to search the URL along with the current time and date. Using the below dork, you will get many pages. Use
inurl:top.htm inurl:currenttimeOR inurl:/view/index.shtml”Camera”.
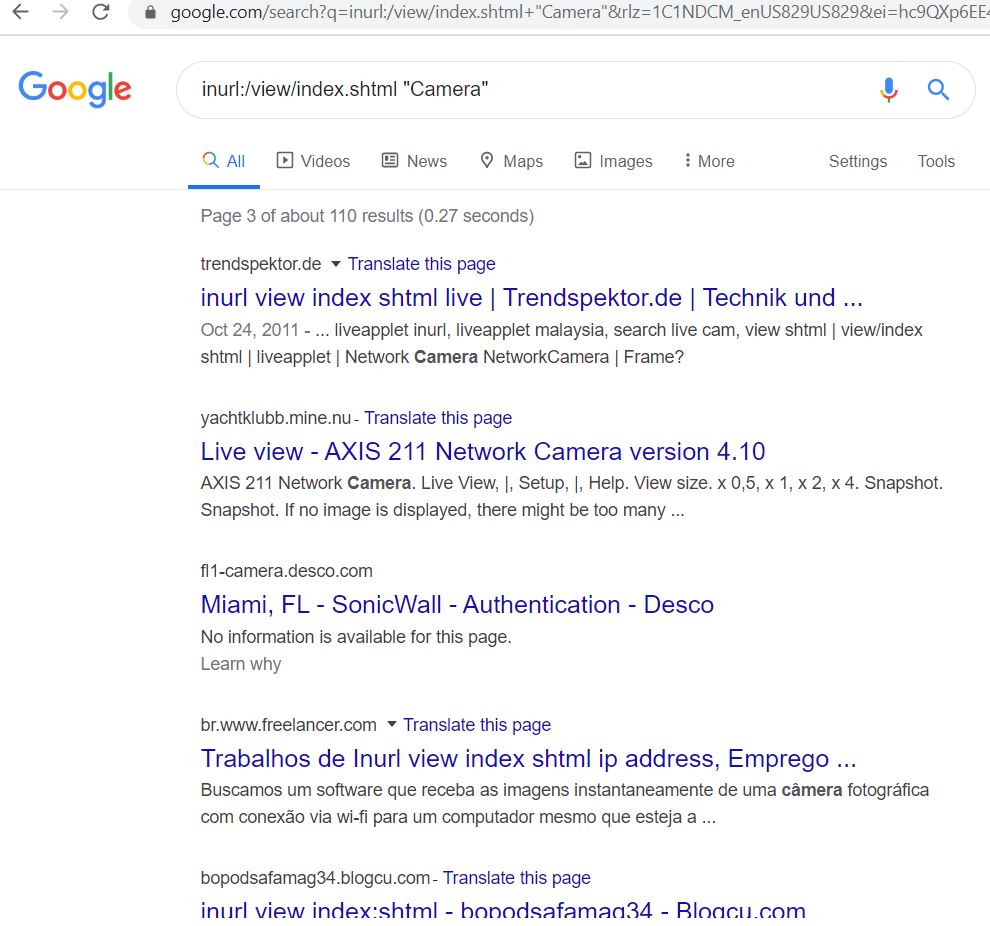
- Now open another link inurl:top.htm inurl:currenttime, let,s see from this page weather we see any live camera or not.
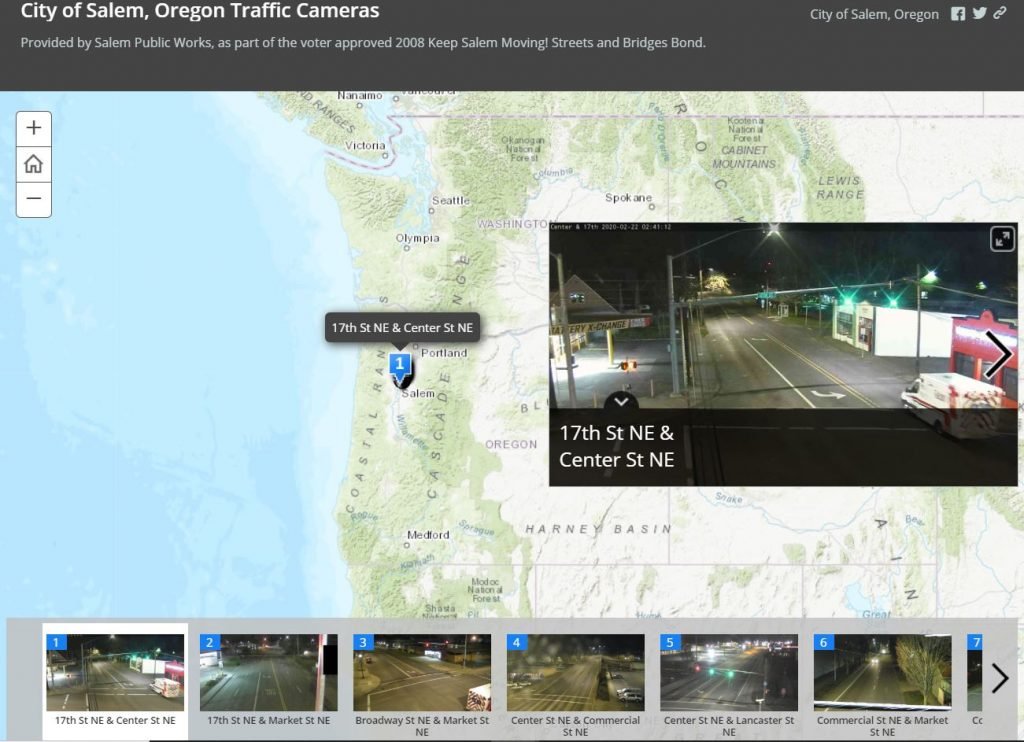
- The above Picture we see live traffic cameras in the USA, Oregon, city of Salem, this camera is available without a password this advantage may use any unusual activity and this how dorks allow you to find authorization pages for cameras that use normal passwords.
- In the above picture, we see live traffic cameras in USA.
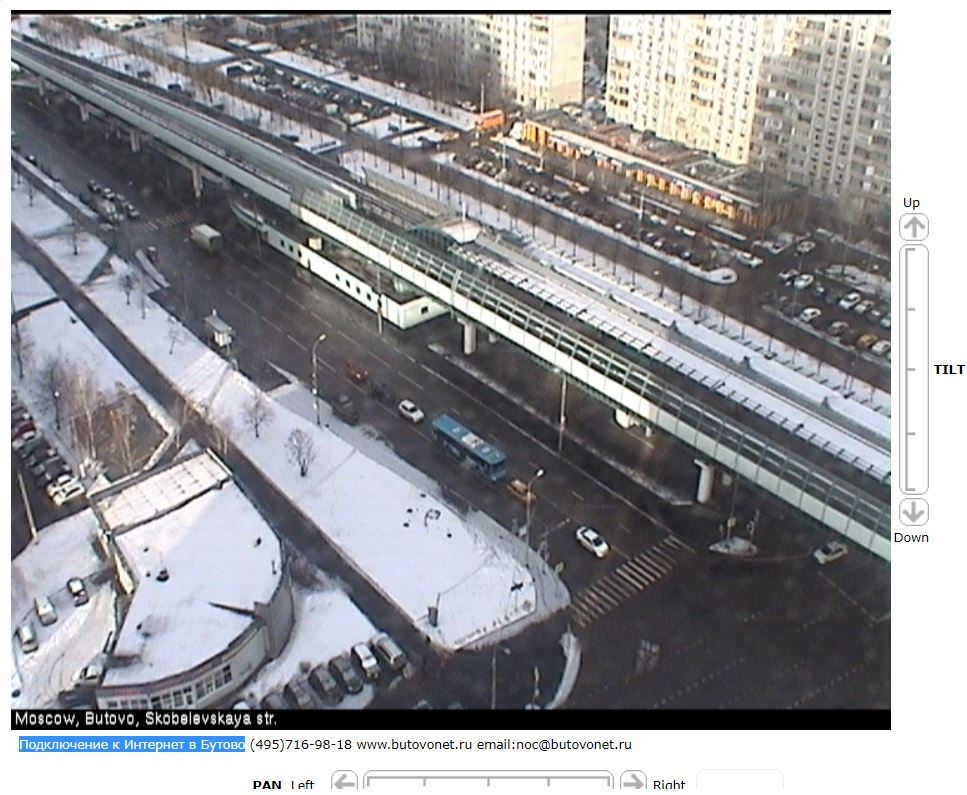
- In the above picture, we see a live traffic camera in Russia.
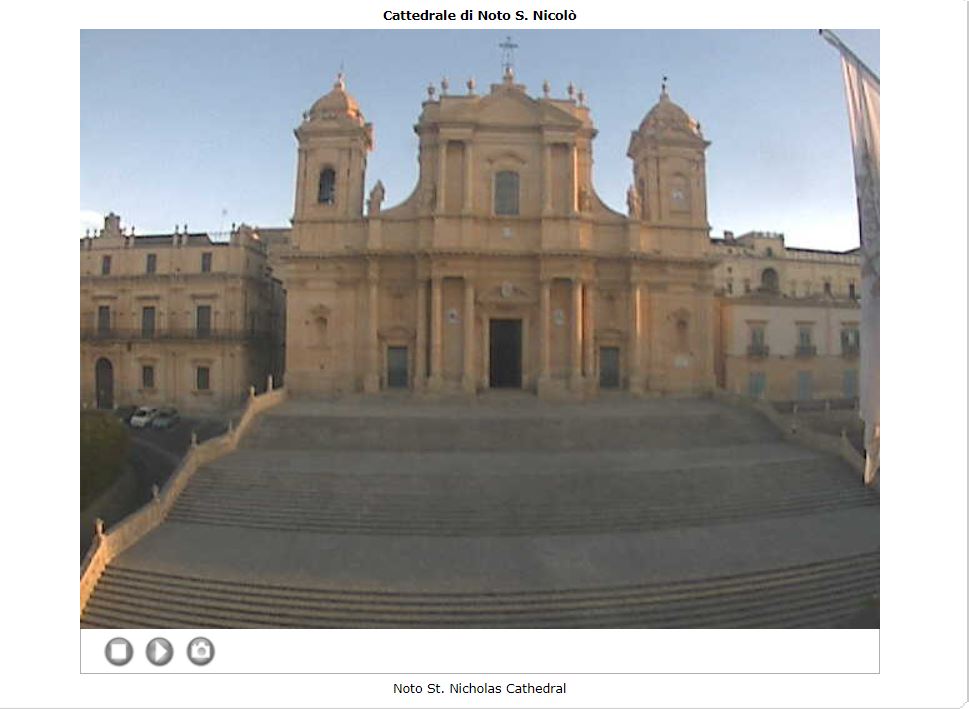
- In the above picture, we see a live camera in Italy.
Conclusion
- Since Google has everything that is connected to the Internet and has a web interface, we can easily find incorrectly configured devices and services. However, it is better not to connect to these devices and there may be problems with application works.
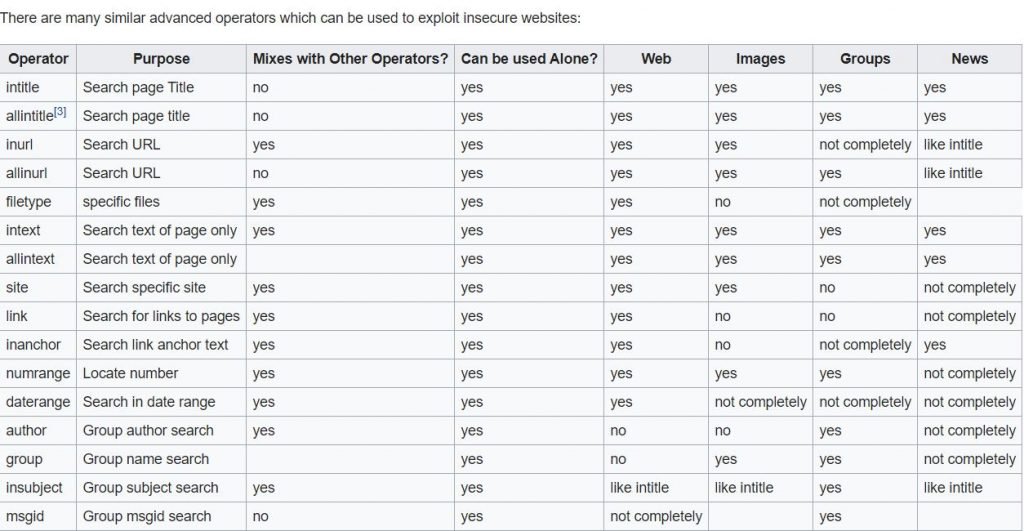
Advanced operators
- This is the advanced operators that we can use to exploit insecure websites.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
