Cybersecurity experts mention that pspy is a command-line tool designed to spy on processes without the need for root permissions. By using this tool, researchers are allowed to view commands executed by other users, jobs, and other activities as they run. This is critical for listing Linux systems in CTF. It is also useful to demonstrate to system administrators why passing secrets as arguments on the command line is a bad idea.
The tool collects information from procfs scans. Researchers located in selected parts of the file system activate these scans to detect short-lived processes.
It is worth mentioning that there are tools to list all processes executed on Linux systems, including processes that have already been completed. For example, it is forkstat, used to receive kernel notifications about process-related events, such as fork and exec.
Although these tools require root privileges, that should not give users a misunderstood sense of security. Nothing prevents you from spying on processes running on a Linux system, and it is possible to access large amounts of information in procfs while a process is running. However, there is a drawback, as researchers must catch short-lived processes in very short time lapses. Scan the /proc directory for new PIDs in an infinite loop completes the hack, but consumes huge computing resources.
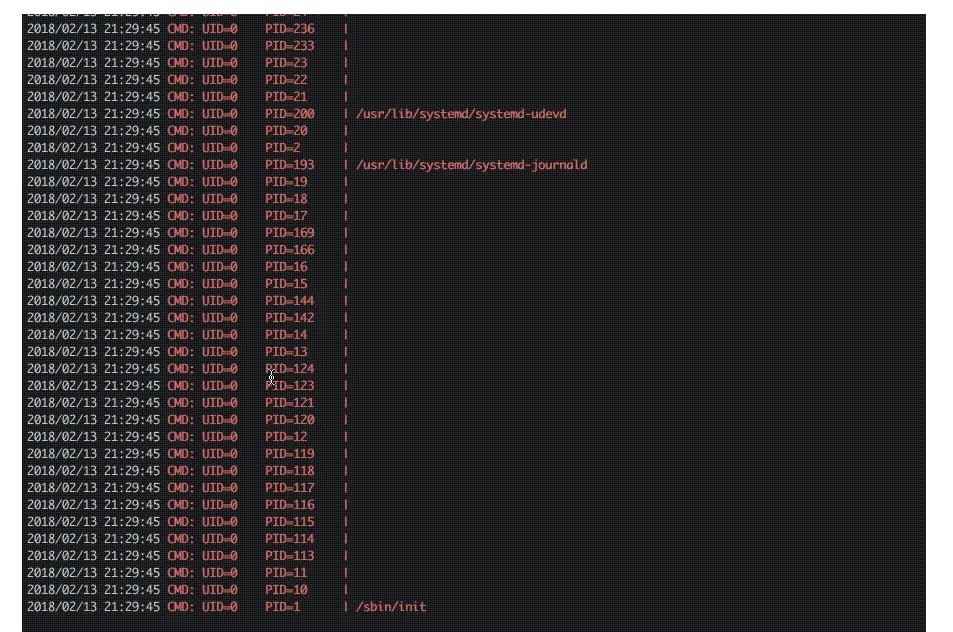
A less obvious method is to use the following: Processes tend to access files such as libraries in /usr, temporary files in /tmp, log files in /var, and more. Using the inotify API, the researcher can receive notifications whenever these files are created, modified, or deleted. High privileges are not required for this API, as it is required for many routine applications, such as text editors. Therefore, even though non-root users cannot monitor processes directly, they can monitor the effects of processes on the file system.
Administrators can use file system events as a trigger to scan/process, hoping to do so fast enough to detect the process. This is possible using pspy; although there is no guarantee that administrators will not lose any process, the chances of success are high enough to try.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
