Researchers at the Israeli cybersecurity firm Check Point have given the new ransomware the name “Rorschach.” They said that their incident response team identified it while looking into an attack that involved a corporation situated in the United States. Researchers in the field of cybersecurity have expressed concern about a new strain of ransomware, which they characterize as a mash-up of the most efficient ransomwares that are already in circulation. The malware would immediately delete the event logs of any devices that it infected and would propagate itself across the system.
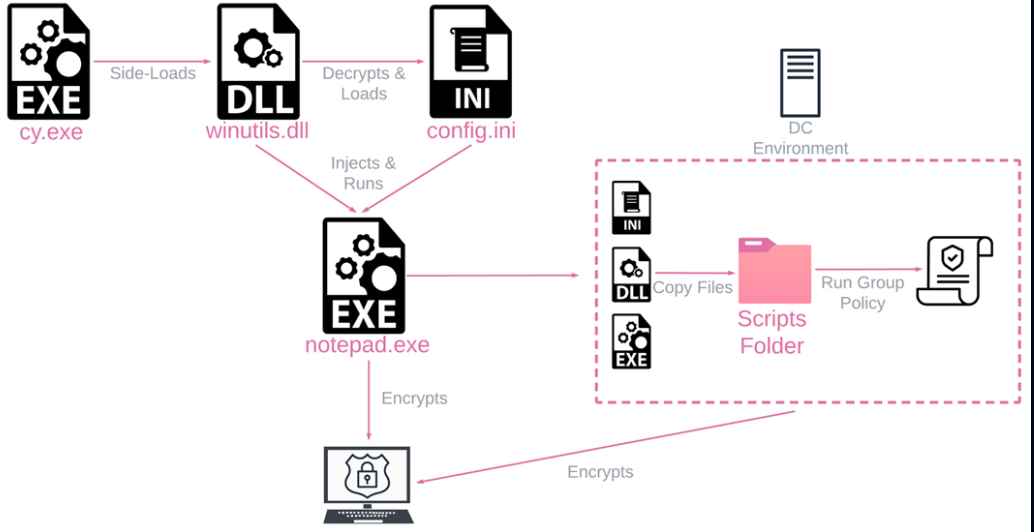
The researchers gave it the name Rorschach because each individual who looked at it saw something a little bit different, much like the well-known psychological test. This inspired them to give it the name.
The average estimated time of encryption is minutes quicker than frequently used ransomware such as LockBit. This was not the only aspect that astonished experts; there were numerous more. One of these qualities was the speed with which it encrypted data. They put LockBit through five independent encryption performance tests in controlled circumstances and said that the ransomware was the “new speed demon in town” after conducting the testing. In addition, the ransomware uses its own one-of-a-kind encryption method, which encrypts just certain parts of a file rather than the full file in order to make it more difficult to decode. This is one of the factors that contributes to its speedier operation compared to other ransomware encryption methods.
According to a research that was released on Tuesday by the business, Rorschach looks to be unique since it does not have any overlaps that might readily identify it to any other ransomware strain, nor does it have the sort of branding that is characteristic of the majority of ransomware organizations.
”
A portion of the ransomware is autonomous, enabling attackers to carry out operations that they would normally have to carry out manually and freeing up some of their time. The ransomware is also highly modifiable, allowing attackers access to a diverse arsenal of tools that they may use to carry out their attacks.
While it had a number of characteristics that were unique to itself, the malware also borrowed elements from a number of previous types of ransomware. The ransom message that was sent to victims was quite similar to those that had been distributed by the Yanluowang and DarkSide organizations. Also, the code behind the ransomware took some cues from the stolen source code of the Babuk and LockBit ransomware strains.
The ransomware has the ability to erase backups and prevent key systems, such as firewalls, from running, which makes recovery far more challenging. The researchers were taken aback when they learned that in addition to encrypting an environment, the ransomware employs certain peculiar strategies in order to circumvent the security measures.
The programmers who created the ransomware also took care to program it to do two system checks that, depending on the language that the victim is using, might cause it to stop functioning properly. The ransomware will not function properly if the language is from a nation that is part of the Commonwealth of Independent States (CIS). It is currently unclear who is behind the Rorschach ransomware, including its operators and creators. They don’t employ branding, which is an unusual practice for ransomware operations.It suggests it’s probably an experienced ransomware gang.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
