MooBot is a variant of Mirai discovered in September 2019 by the Qihoo 360 Netlab team. Moobot previously focused on devices such as LILIN digital video recorders and Hikvision video surveillance products to expand its botnet.
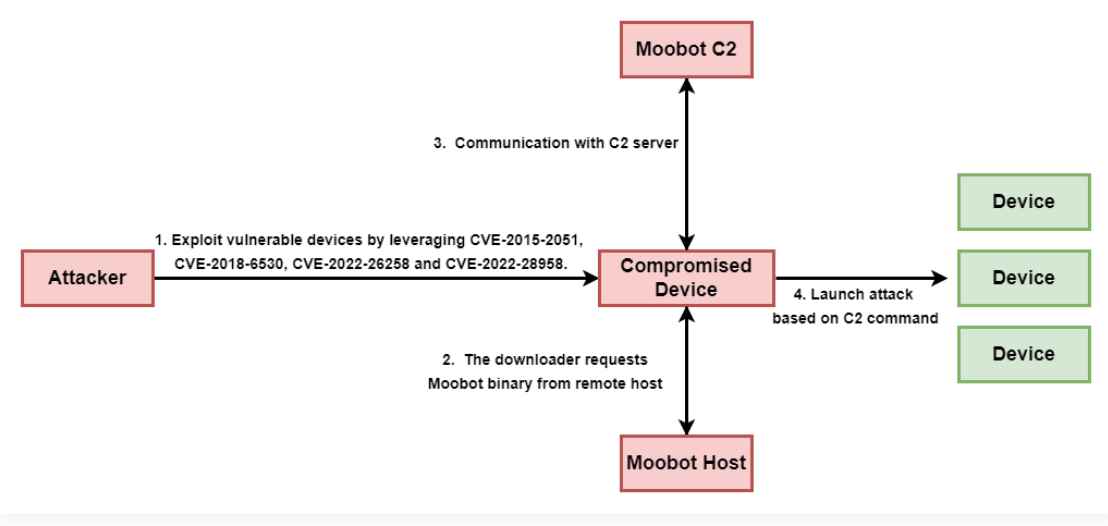
Earlier this past August, Palo Alto Networks Unit 42 observed a series of attacks with attempts to exploit up to four different vulnerabilities in D-Link devices. These were critical vulnerabilities with low exploitation complexity.
Employed
- CVE-2015-2051 ( CVSS score: 10.0): Command execution vulnerability via ‘GetDeviceSettings’ in HNAP interface.
- CVE-2018-6530 ( CVSS score: 9.8) – Remote OS command injection vulnerability via a parameter in the SOAP interface.
- CVE-2022-26258 ( CVSS score: 9.8): Remote command execution vulnerability via parameter in ‘lan.asp’.
- CVE-2022-28958 ( CVSS score: 9.8): Remote code execution vulnerability via parameter in ‘shareport.php’.
These security flaws affect the following D-Link devices:
- DIR-65L
- DIR-645
- DIR816L
- DIR-820L
- DIR-860L
- DIR-868L
- DIR-880L
Attack & IOCs
Successful exploitation of any of the above vulnerabilities could lead to remote command or code execution and allow recovery of the MooBot payload from a remote server. From then on, the device would wait for instructions from the command and control server (C2) to execute, for example, distributed denial of service (DDoS) attacks.
The team of researchers has published a series of IOCs. Even though a couple of the vulnerabilities used were discovered several years ago and all of them have been fixed by D-Link, there are still many vulnerable devices. Users of affected D-Link devices are recommended to apply the security updates and patches available on the manufacturer’s official website to mitigate potential threats.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
