Did you know that the WordPress content management system powers over 455 million websites, or over 30% of all websites worldwide? That represents 62% of the top 100 fastest-growing businesses, and just on WordPress alone, they create 70 million new blog articles every month. And what do Facebook and Wikipedia have in common with the most widely used content management system in the world? The solution is PHP. The majority of the modern web is based on PHP, which has become the de facto standard. In response, PHP security has emerged as a new difficulty.
PHP team has released patch for 2 important vulnerabilities. Below are the details
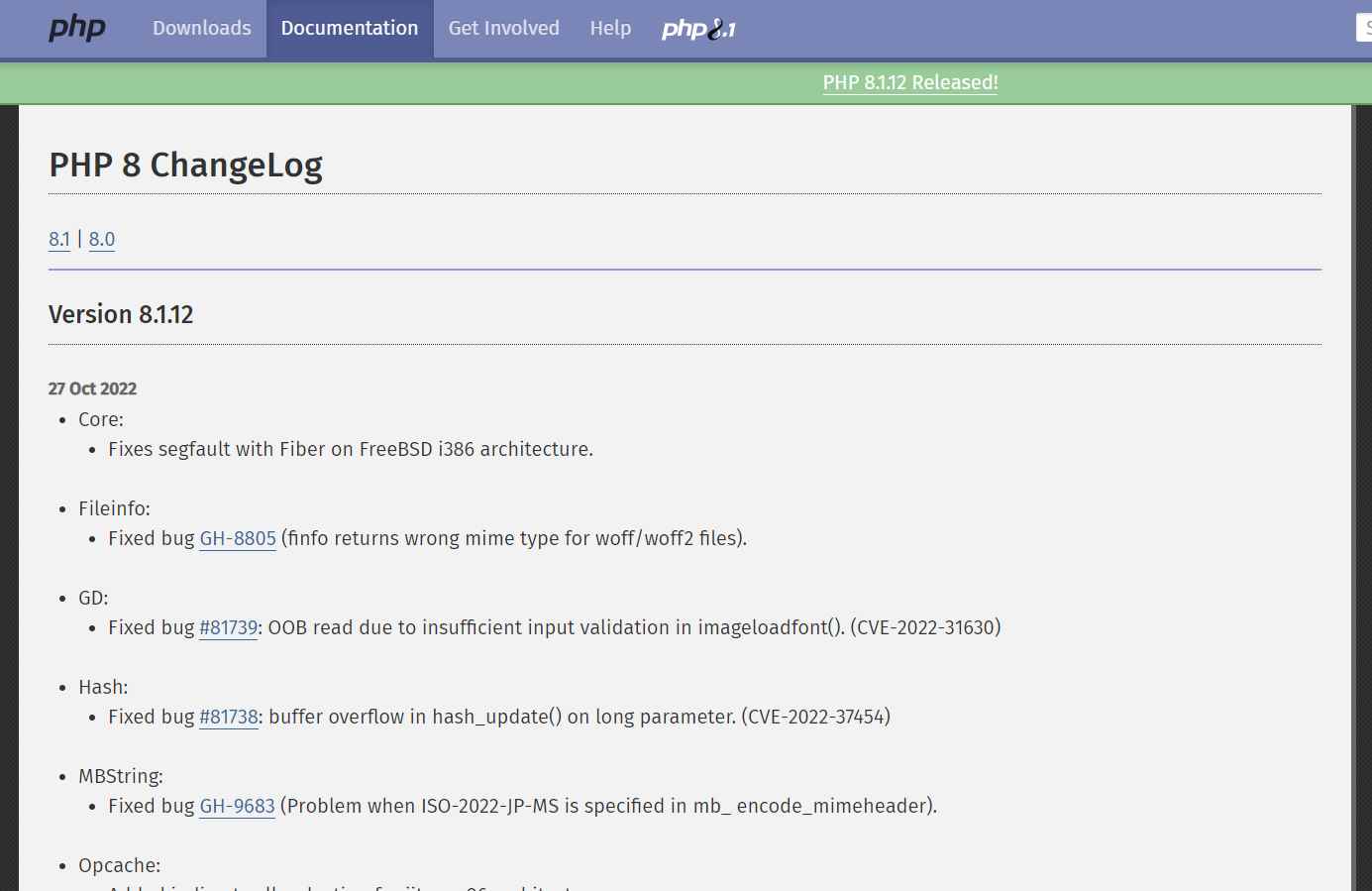
1) Out-of-bounds read CVE-ID: CVE-2022-31630
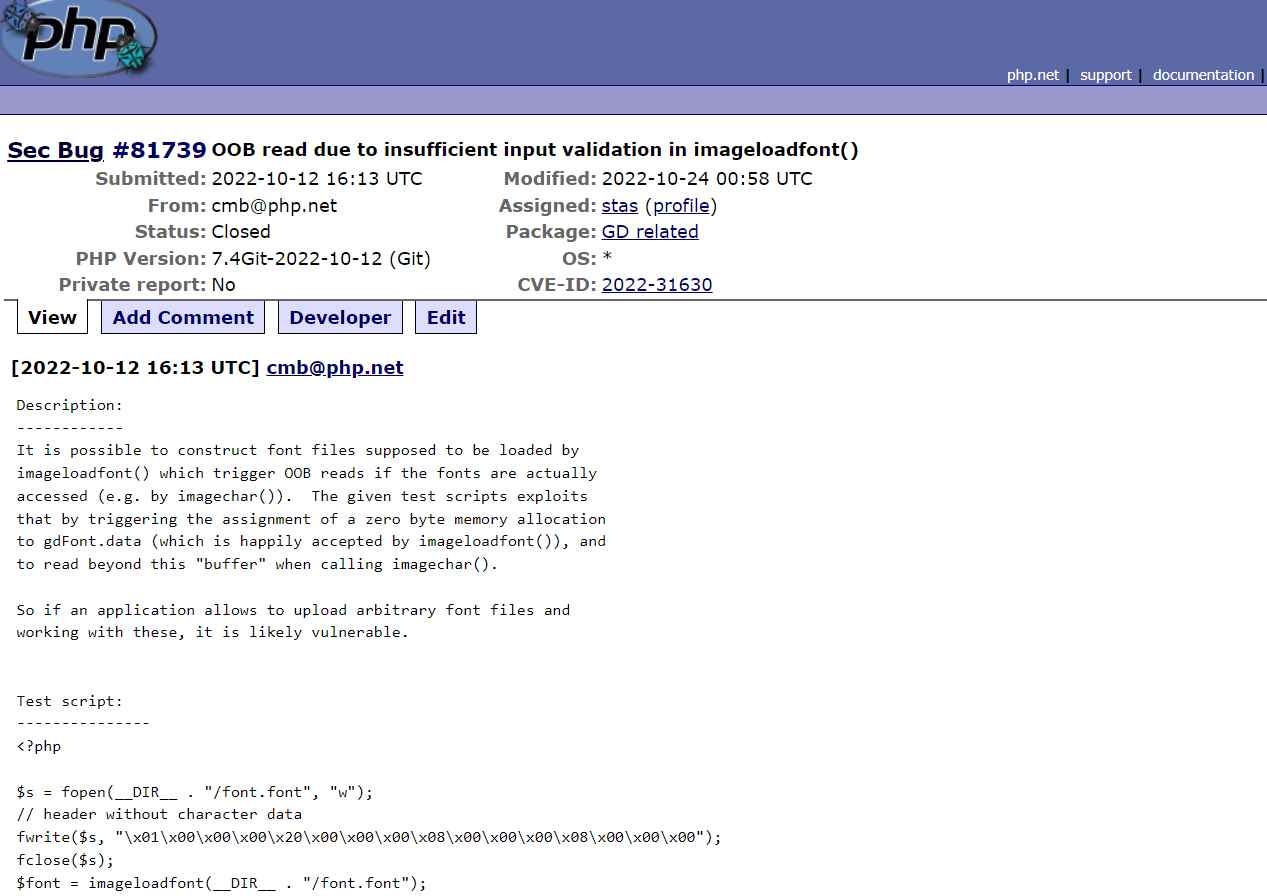
Description
A adversary might obtain potentially sensitive data because of the flaw.
A boundary condition in the imageloadfont() method is the cause of the bug. A malicious hacker has the ability to send the web application specially constructed data, cause an out-of-bounds read error, and access the contents of the system’s memory.
Mitigation
Install PHP updates from website.
Vulnerable PHP versions
PHP: 8.0.0 – 8.0.24, 8.1.0 – 8.1.11
2) Integer overflow CVE-ID: CVE-2022-37454
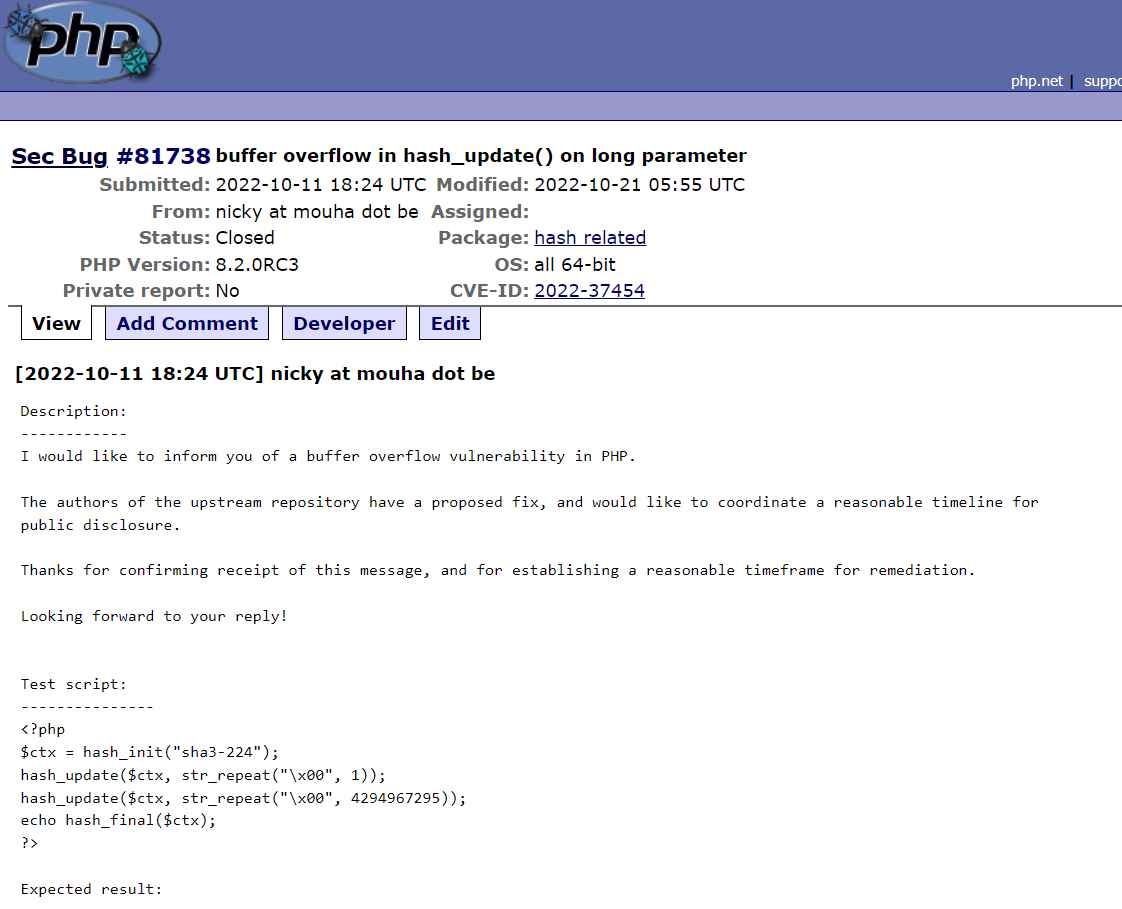
Description
A malicious hacker can run any code they like on the target machine due to the flaw.
The Keccak XKCP SHA-3 reference implementation contains an integer overrun that gives rise to the flaw. An adversary from a remote may send the program specially constructed data, cause an integer overflow, run arbitrary code on the target machine, or disable expected cryptographic characteristics. The hash update() PHP function is where the flaw is discovered.
A susceptible system might be totally compromised if this flaw is exploited successfully.
Mitigation
Install PHP updates from website.
Vulnerable PHP versions
PHP: 8.0.0 – 8.0.24, 8.1.0 – 8.1.11
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
