Although Microsoft received the CVE-2020-0688 flaw report a while ago, a recent report has revealed that more than 247,000 Microsoft Exchange servers continue to operate without the required patches.
This is a remote code execution vulnerability that affects all versions of Exchange currently used. An attacker could compromise the Exchange Control Panel (ECP) component to remotely control a vulnerable server using valid email credentials.
The company announced the release of a patch to fix this flaw in February 2020, as it was considered an exploitable vulnerability. On the other hand, security firm Rapid7 added an MS Exchange RCE module to the Metasploit penetration testing framework developed last March thanks to the emergence of various proofs of concept.
Weeks later, the Agency for Cybersecurity and Infrastructure Security (CISA) asked potentially affected organizations to install the patches to mitigate the risk of exploitation as soon as possible, as multiple attempts at active exploitation had already been detected.
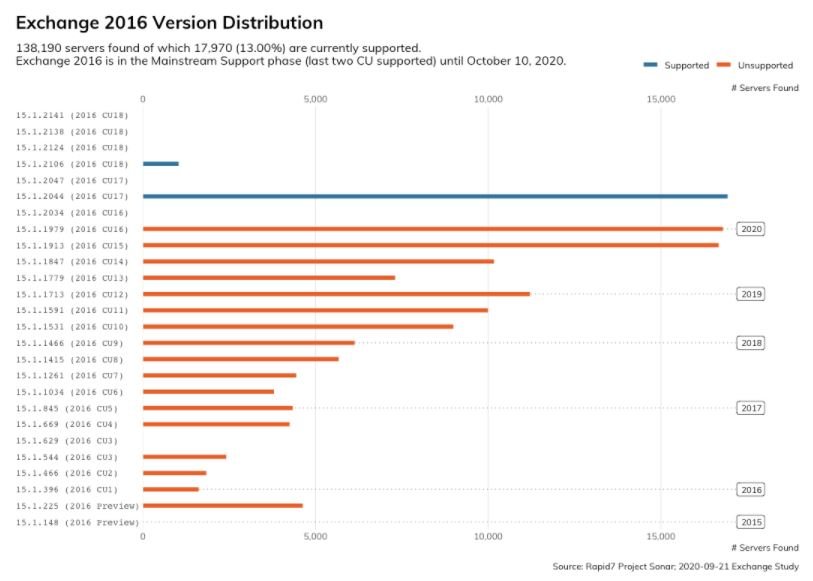
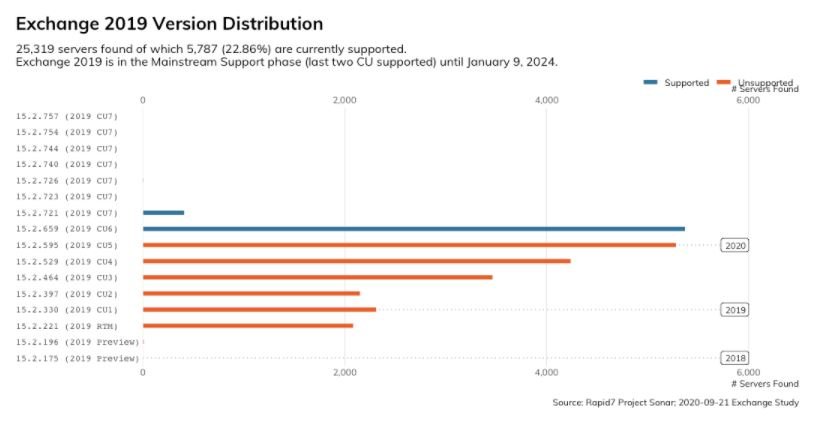
In an update to this vulnerability, Rapid7 performed an analysis of vulnerable deployments, finding that 61% of Exchange servers (about 247,800 deployments) remain out of date or, in other words, remain exposed to threat actors.
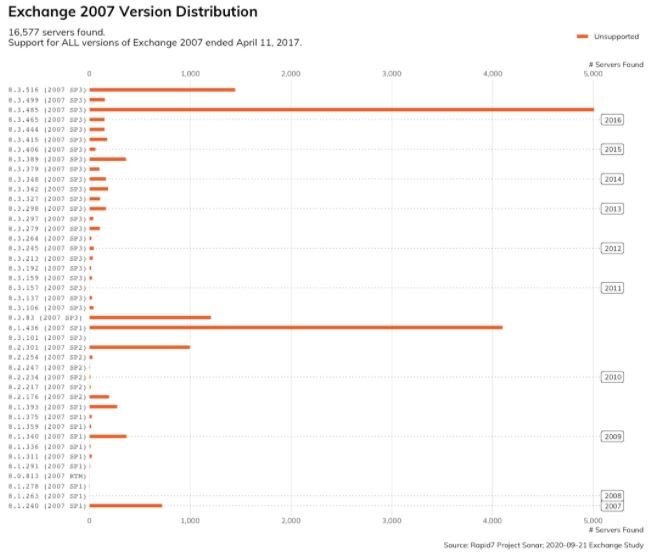
More than that, specialists found that tens of thousands of deployments have been without updates for more than five years. Rapid7 also discovered 16,000 Exchange 2007 servers accessible from the public Internet. This is an unsupported version of Exchange that did not receive patches to protect against CVE-2020-0688 exploitation.
Microsoft mentioned that there are no mitigation methods for this vulnerability, so the company strongly recommends that users install the security patches. Direct download links to security updates that you need to install to patch vulnerable versions of Microsoft Exchange Server are located on the company’s official platforms.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
