This week, SolarWinds released three warnings that detailed high-severity vulnerabilities that are anticipated to be corrected with an upgrade to the SolarWinds Platform before the month of February is out.
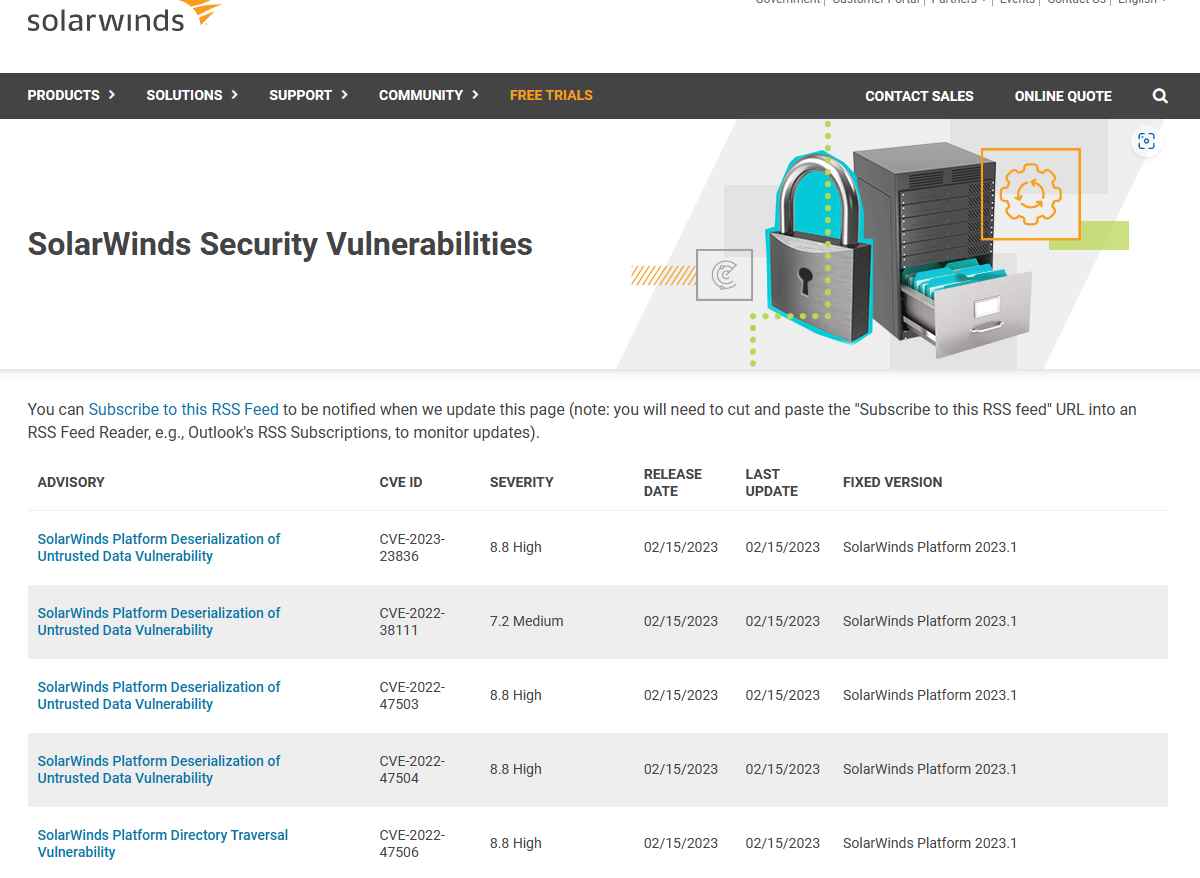
There are a total of seven flaws in the system’s security, five of which are defined as problems with the deserialization of untrusted data and have the potential to be exploited in order to accomplish command execution. A CVSS score of 8.8 was assigned to four of them.
According to SolarWinds, the high-severity vulnerabilities, which are tracked as CVE-2023-23836, CVE-2022-47503, CVE-2022-47504 and CVE-2022-47507, might enable “a remote attacker with Orion admin-level account access to the SolarWinds Web Console to execute arbitrary commands.”
The fifth flaw, which has been assigned the tracking number CVE-2022-38111, is categorized as a medium-severity problem by SolarWinds; nonetheless, the effects of exploiting it successfully are the same as in the other cases. The issue also has a CVSS score of 7.2, which places it in the ‘high severity’ category of vulnerabilities.
The business also disclosed remedies for a high-severity path traversal vulnerability that was found in the SolarWinds Platform. This vulnerability is known as CVE-2022-47506 and is being monitored (CVSS score of 8.8).
In addition, SolarWinds has released information on a high-severity bug that was present in Server & Application Monitor 2022.4 and prevented users from using Kerberos in conjunction with NTLM.
SolarWinds Platform 2023.1, which is scheduled to be released by the end of the month, fixes all known flaws in the software. Consumers should upgrade to this version as soon as it is made available, since it is strongly recommended.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
