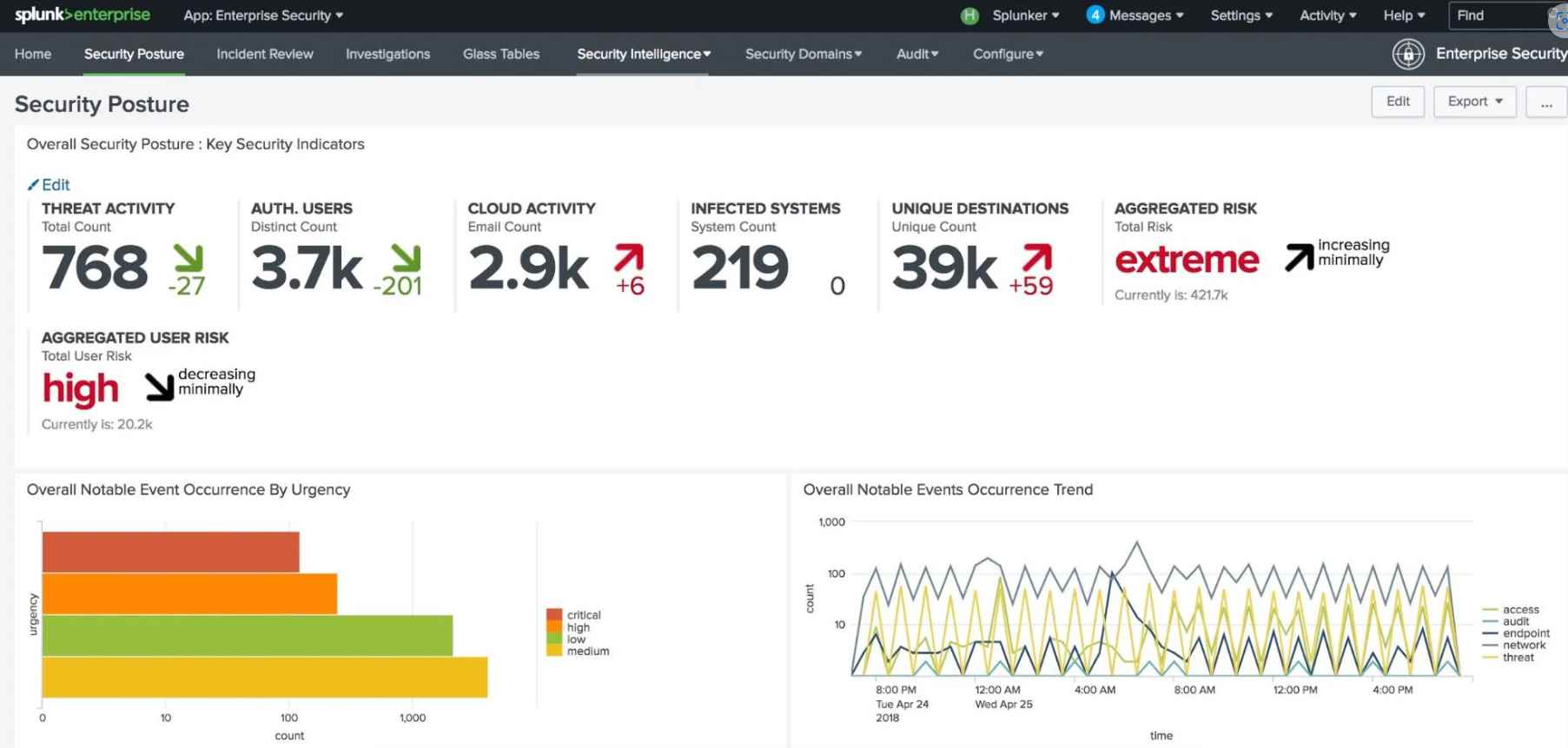
Splunk is one of the Security Incident and Event Management (SIEM) tools that is used the most all over the globe. Splunk has the capability to gather logs of all the events that have been configured, which may then be utilized in the future to analyze security problems.
According to recent reports, Splunk was susceptible to a privilege escalation vulnerability that was found and reported. This vulnerability was detected and reported.

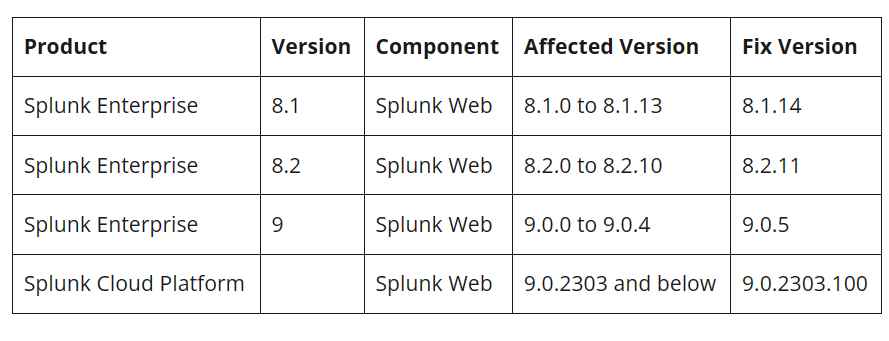
This security hole was fixed up as quickly as possible by the firm across all versions of Splunk.
‘edit_user’ is the CVE-2023-32707 vulnerability. Escalation of Capabilities and Privileges
By submitting a web request to Splunk that has been carefully prepared, even a user with limited privileges who is able to perform the ‘edit_user’ capability action may elevate their status to that of an admin user.This occurred due to the fact that the ‘edit_user’ configuration option in the authorize.conf file does not link with the ‘grantableRole’ setting in the file, which is a parameter that may avoid this privilege escalation vulnerability.
Workarounds and mitigations include making sure that no other users except administrators are able to update their own profiles (the ‘edit_user’ capability).Do not offer a ‘edit_user’ role that other roles may inherit from in order to facilitate inheritance.Users that have little or no rights should not have the ‘edit_user’ capability assigned to them.
It is strongly suggested that all users of Splunk update their installations of Splunk to the most recent available version.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
