According to security firm Rapid7, many flaws have been discovered in two medical devices made by billion-dollar healthcare corporation Baxter International.
The Sigma WiFi battery and Sigma Spectrum Infusion Pump from Baxter are also impacted by the problems. According to Rapid7, infusion pumps are often utilized to provide medicine to patients in hospitals around the United States and other nations.

Deral Heiland, a principal Internet of Things researcher at Rapid7, first identified the problems and reported them to Baxter. He then collaborated with the business to find solutions.
The secure deactivation of Wireless Battery Modules is the focus of the four bugs (WBMs). Before a device is given to a new user, network credentials or other sensitive information are frequently present on medical equipment.
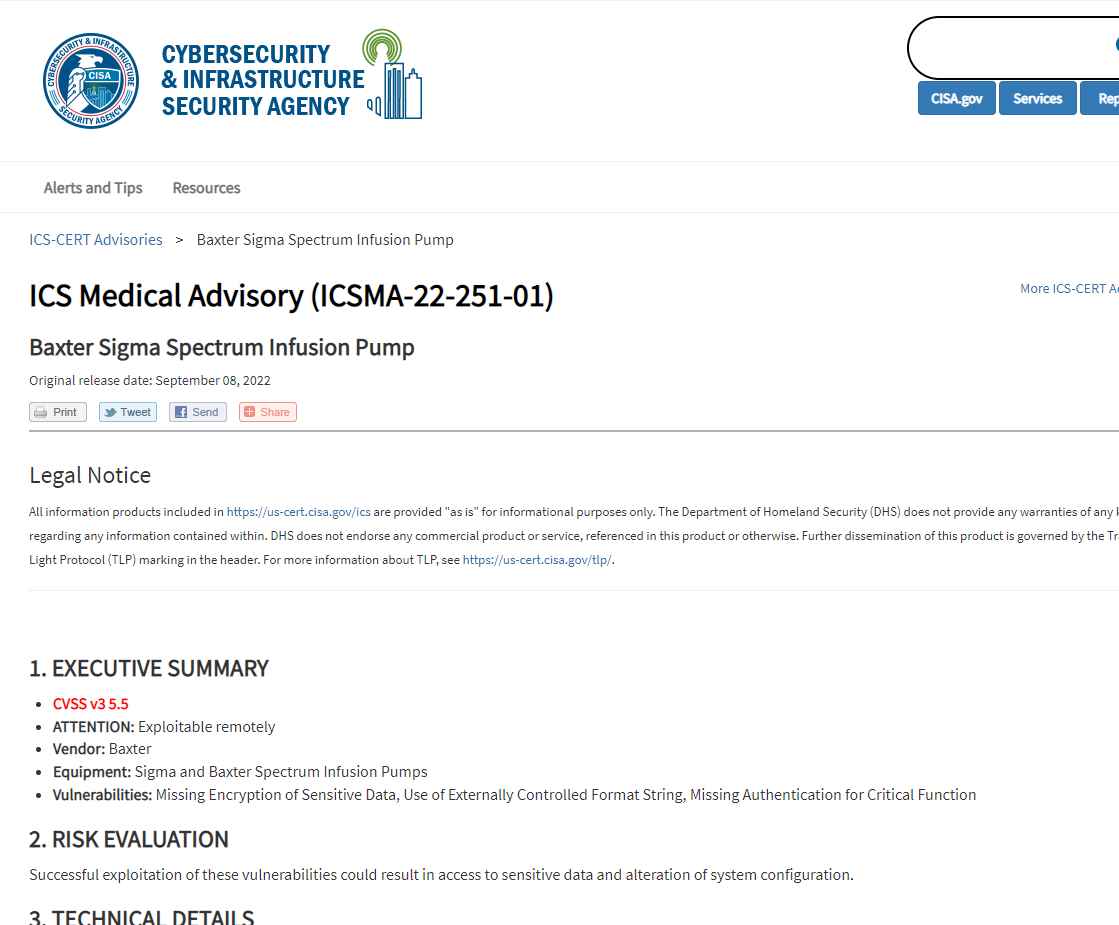
Software patches for CVE-2022-26392 and CVE-2022-26393 are now being developed, according to Baxter, which said it has not discovered any instances of the vulnerabilities being exploited.
For CVE-2022-26394, authentication is already available, and for CVE-2022-26390, the business has released instructions.
The following versions of Sigma Spectrum Infusion systems are affected:
- Sigma Spectrum v6.x model 35700BAX
- Sigma Spectrum v8.x model 35700BAX2
- Baxter Spectrum IQ (v9.x) model 35700BAX3
- Sigma Spectrum LVP v6.x Wireless Battery Modules v16, v16D38, v17, v17D19, v20D29 to v20D32, and v22D24 to v22D28
- Sigma Spectrum LVP v8.x Wireless Battery Modules v17, v17D19, v20D29 to v20D32, and v22D24 to v22D28
- Baxter Spectrum IQ LVP (v9.x) with Wireless Battery Modules v22D19 to v22D28
CISA issued its own advice about the vulnerabilities, the second of which was issued this week regarding medical equipment.
For more than a decade, companies and security specialists have worked to make infusion pumps more secure, but they have long been a source of ire.
Hackers would need to be nearby the impacted devices, at the very least within WiFi range, and in some circumstances, they would also need to have direct physical access.
The WiFi/battery device storing the WiFi credentials from the last infusion pump unit it was linked to, in his opinion, poses the most risk.
The factory reset function of the pump, he said, does not erase the credential data from the WiFi or batteries. Someone may get the data from the batteries if they were sold on the secondary market.
Heiland claimed to have verified this by getting a number of the devices from eBay and successfully extracting what looks to be legitimate WPA PSK and SSID data, which could be linked to a particular healthcare provider.
He pointed out that if an attacker gained access to a pump unit’s network, they might route all backend system communications to a host under their control by sending a single unauthenticated packet, opening the door to a possible “man-in-the-middle” attack.
This might possibly be used to intercept drug library data updates to the pumps, which could be harmful, and it could also have an influence on the accuracy of the pump data being transmitted for monitoring and recording reasons. If the drug library data is changed, the pump might not warn the operator if a risky setting was entered or it might refuse to accept a legitimate setting, which might result in drug settings being entered incorrectly, the researcher stated.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
