For the fourth time in the last two months, Cisco has released security patches to fix two critical vulnerabilities detected on the Webex video conferencing platform. If exploited, these flaws could allow threat actors to execute arbitrary code on the target system. The flaws lies in two media players associated with Webex:
- Cisco Webex Network Recording Player
- Cisco Webex Player
The first of the affected players is used to play Advanced Recording Format (ARF) files on Windows operating systems; these files contain data recorded during a Webex session, such as a list of attendees and video clips. On the other hand, Webex Player works with Webex Recording Format (WRF) files, which contain audio and video samples.
The vulnerabilities, tracked as CVE-2020-3127 & CVE-2020-3128, received a score of 7.8/10 on the Common Vulnerability Scoring System (CVSS) scale, so they are considered high severity. According to the Cisco’s cybersecurity alert, these flaws exist due to poor validation of some elements in recordings of the mentioned formats. The company did not add further details about the faults.
Although the firm did not disclose technical details, some other data on the vulnerabilities, such as the possible consequences of their exploitation, were revealed. In its alert, Cisco mentions that a threat actor could exploit them by sending a malicious ARF or WRF file, using emails with attachments. Successful execution of either of these two flaws would allow arbitrary code to run on the target system with administrator privileges.
So far, there isn’t known cases exploitation of this vulnerability in the wild, although the company states that it is a priority for exposed deployment administrators to update as soon as possible to mitigate the risk of exploitation. Below is the list of vulnerable deployments with their respective updated version:
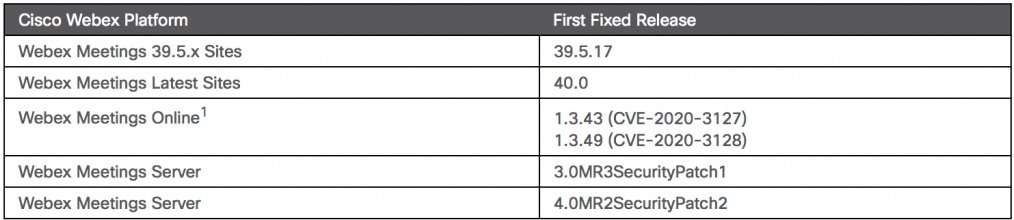
The main vulnerabilities fixed by Cisco so far in 2020 have been found in Webex. The first security patch of the year released by Cisco addressed a severe flaw in the video conferencing platform that could have allowed any user to join an unauthenticated session. Another severe code remote execution flaw in Webex was also fixed a couple of weeks ago.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
