According to a forensic report published by Fortinet on Wednesday, an unidentified threat actor exploited a key vulnerability in the company’s FortiOS SSL-VPN product in order to attack government and government-related companies with complex custom-made malware.
This vulnerability, which has been assigned the tracking number CVE-2022-42475, is a heap-based buffer overflow that enables hackers to remotely execute malicious code. It has a severity rating of 9.8 out of a possible 10, which indicates that it is very dangerous. Fortinet, a company that makes software for network security, patched the vulnerability in the version 7.2.3 that was released on November 28. However, the company did not disclose the danger in the release notes that it provided at the time.
Fortinet offered a more comprehensive description of the exploit activity and the threat actor who was responsible for it. According to the latest update provided by Fortinet on Wednesday, company representatives said that “the intricacy of the attack implies a sophisticated actor” and that “it is heavily targeted at governmental or government-related targets.”
According to the findings of an investigation that Fortinet carried out on one of the compromised servers, the threat actor exploited the vulnerability in order to install a modified version of a well-known Linux-based implant that had been modified in order to operate on top of the FortiOS. When the post-exploit malware was deployed, it immediately deactivated specific logging events so that it would not be discovered. The implant was placed in the directory /data/lib/libips.bak after installation. It is possible that the file is pretending to be a component of the Fortinet IPS Engine, which can be found at /data/lib/libips.so. In addition, the file /data/lib/libips.so was accessible, although it displayed a file size of 0 bytes.
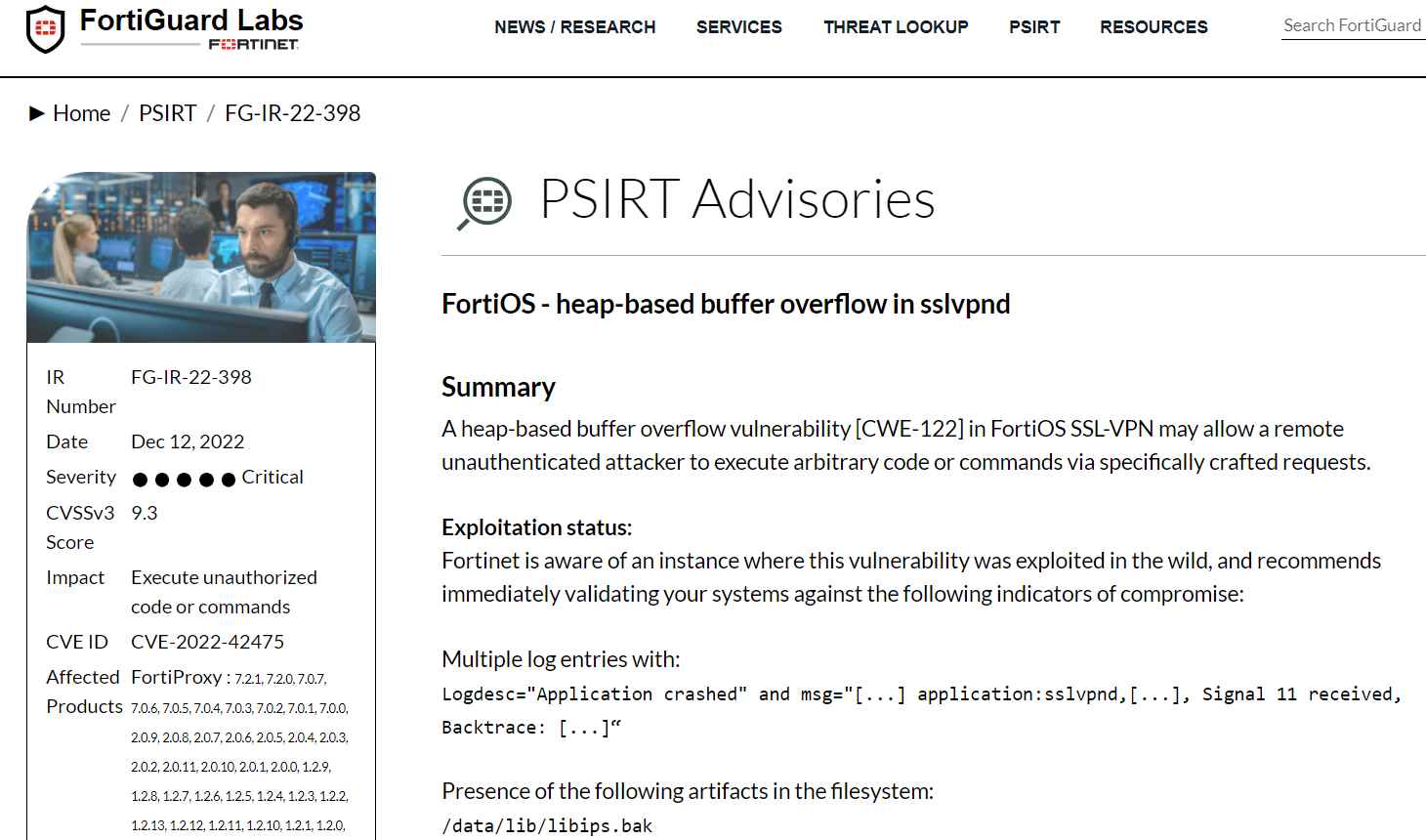
After simulating the operation of the implant, researchers from Fortinet uncovered a one-of-a-kind string of bytes in the implant’s communication with command-and-control servers. This string of bytes has the potential to be utilized as a signature in intrusion-prevention systems.
Other indications that a server has been the target of an attack include connections to a wide range of IP addresses, one of which is 103.131.189.143, as well as the TCP sessions listed below:
- Port 443 connections to the FortiGate
- Get request for /remote/login/lang=en
- Post request to remote/error
- Get request to payloads
- Connection to the FortiGate Interactive shell session in order to carry out command execution.
The forensics reveals a wide range of other evidence that the victim was compromised. Organizations that utilize the FortiOS SSL-VPN should read it carefully and examine their networks for any signals that might indicate that they have been targeted or corrupted. The business strongly suggested to its clients that they check their networks for any indications that the vulnerability had been exploited on their systems and that they make sure they were using the patched version of the software.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
