According to a researcher, a sophisticated relay attack may be used to quickly unlock and take possession of a Tesla Model Y by someone having physical access to the vehicle.
The flaw, which was found by Josep Pi Rodriguez, chief security consultant for IOActive, includes what is known as an NFC relay attack and calls for two criminals to work together. The owner of the vehicle must have a Tesla virtual key on their phone or NFC keycard in their pocket or pocketbook, and the other thief must be close to the owner of the vehicle. In Rodriguez’s example, thieves can take a Tesla Model Y if they can get close enough to the owner’s NFC card or smartphone with a Tesla virtual key on it—roughly two inches.
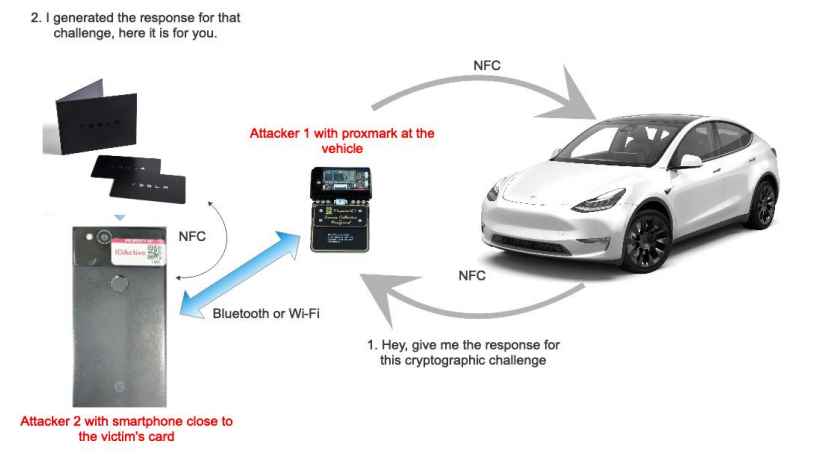
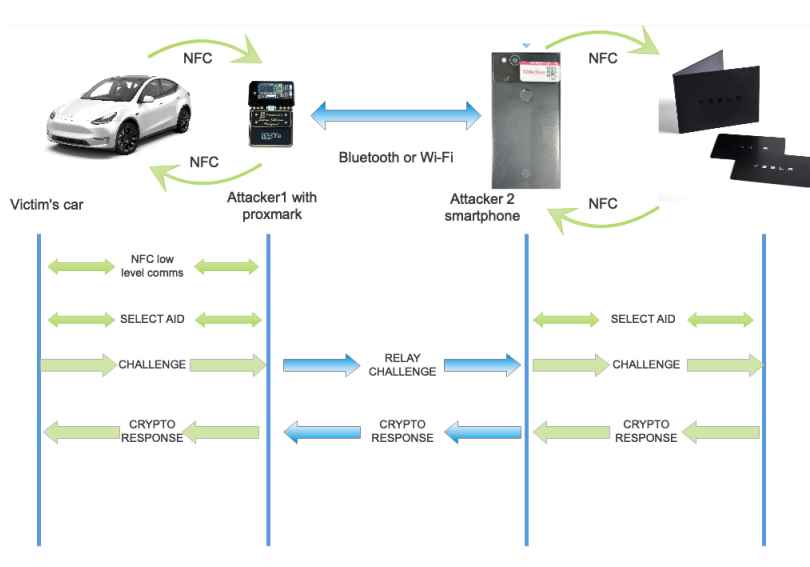
The NFC reader in the driver’s side door is initially communicated with by the first attacker using a Proxmark RDV4.0 device. The owner’s NFC card is intended to reply to the challenge that the automobile sends in response. In the hacking scenario, however, the Proxmark gadget sends the challenge over Wi-Fi or Bluetooth to the companion’s smartphone, which he or she then positions close to the owner’s pocket or purse to interact with the keycard. The Proxmark gadget receives the keycard response and transmits it to the automobile, therefore validating the thief to the car and unlocking it.
Rodriguez claims it is possible to carry out the attack via Bluetooth from several feet away or even farther with Wi-Fi by using a Raspberry Pi to relay the signals, despite the fact that the attack via Wi-Fi and Bluetooth places restrictions.
If Tesla vehicle owners turn on the PIN-to-drive feature, which requires them to input a PIN before they can operate the car, they can stop the attack Rodriguez came up with.
The plan has one drawback: after the engine is turned off, the thieves won’t be able to restart the vehicle using the original NFC keycard. According to Rodriguez, they could add a fresh NFC keycard to the automobile so they could drive it whenever they wanted. But since adding a new key involves a second relay assault, the second accomplice must be close to the owner’s NFC keycard a second time after the first accomplice has entered the car. This will enable the first accomplice to identify themselves to the vehicle and add a new keycard.
However, Rodriguez claims that when he approached the firm, they minimized the issue and said the PIN-to-drive feature would fix it. In order to start the vehicle, a driver must enter a four-digit PIN on the touchscreen of the automobile.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
