In past days, cybersecurity firm Trend Micro issued an alert about five vulnerabilities detected in some of its antivirus and endpoint solutions, including Apex One and OfficeScan, noting that two of these flaws were exploited in the wild.
According to the security alert, the two exploited vulnerabilities are:
- CVE-2020-8467: This is a flaw present in a component of the Apex One and OfficeScan migration tool. The Trend Micro cybersecurity team mentions that an authenticated remote threat actor could exploit this flaw to get arbitrary code execution in the affected deployments.
- CVE-2020-8468: This vulnerability was detected in Apex One and OfficeScan agents, and exists due to content validation escape. An authenticated hacker could take advantage of this security flaw to manipulate some compromised components.
As already mentioned, Trend Micro mentions that at least one attempt to exploit these flaws has been detected in real-world scenarios. For the time being, technical details about these vulnerabilities will remain undisclosed.
In addition, Trend Micro revealed the release of security patches for three other critical vulnerabilities. These three security flaws received a score of 10/10 on the Common Vulnerability Scoring System (CVSS) scale, although no attempts at exploitation have been known so far.
- CVE-2020-8470: This flaw on the Apex One and OfficeScan server exists due to the presence of a vulnerable DLL. Successful exploitation would allow a threat actor to obtain system-level privileges, allowing him to run any file on the server.
- CVE-2020-8598: This flaw also exists due to the presence of a vulnerable DLL; an unauthenticated remote hacker could exploit the vulnerability to execute arbitrary code with high privileges.
- CVE-2020-8599: This flaw in Apex One and OfficeScan exists due to the presence of a vulnerable executable and its exploitation would allow a threat actor the ability to evade ROOT login, as well as being able to write data in an arbitrary path of the system.
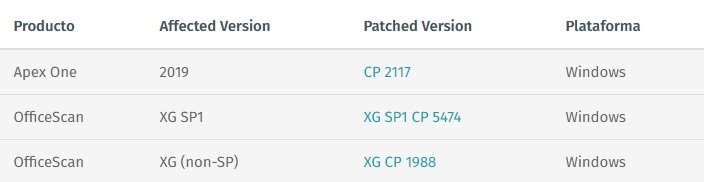
To fix these vulnerabilities, Trend Micro released updates to Apex One and OfficeScan. Users are prompted to install the latest version of their respective deployments.
Late last year, Trend Micro reported another vulnerability exploitation incident in real-world scenarios. On that occasion, the firm was referring to CVE-2019-18187, a directory traversal flaw at OfficeScan discovered last summer.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
