A recently released report by security researcher Adam Chester details a new method for attacking Azure cloud deployments; So far there is no known method to fix this vulnerability, so it is recommended to remain alert.
If an attacker compromises an organization’s Azure agent server, a component required to synchronize Azure AD with on-premises AD, you can create a kind of backdoor that allows you to sign in like any authorized user. A proof-of-concept was created to manipulate the Azure authentication function with the intent to:
- Get a “skeleton key” (also known as “master key”) that works for any user
- Dump all unencrypted usernames and passwords into a single file
Azure AD-Connect connects an Azure AD environment to an on-premises domain and has several authentication methods:
- Hash password synchronization: a method that synchronizes on-premises hashes with the cloud
- Pass-Through Authentication: A method that installs an “Azure agent” in a deployment to authenticate users synchronized from the cloud
- Federation: a method that is based on an AD FS infrastructure
This attack variant exploits Pass-Through authentication; the on-premises agent collects and verifies the credentials received by Azure AD for accounts that are synchronized with on-premises domains.
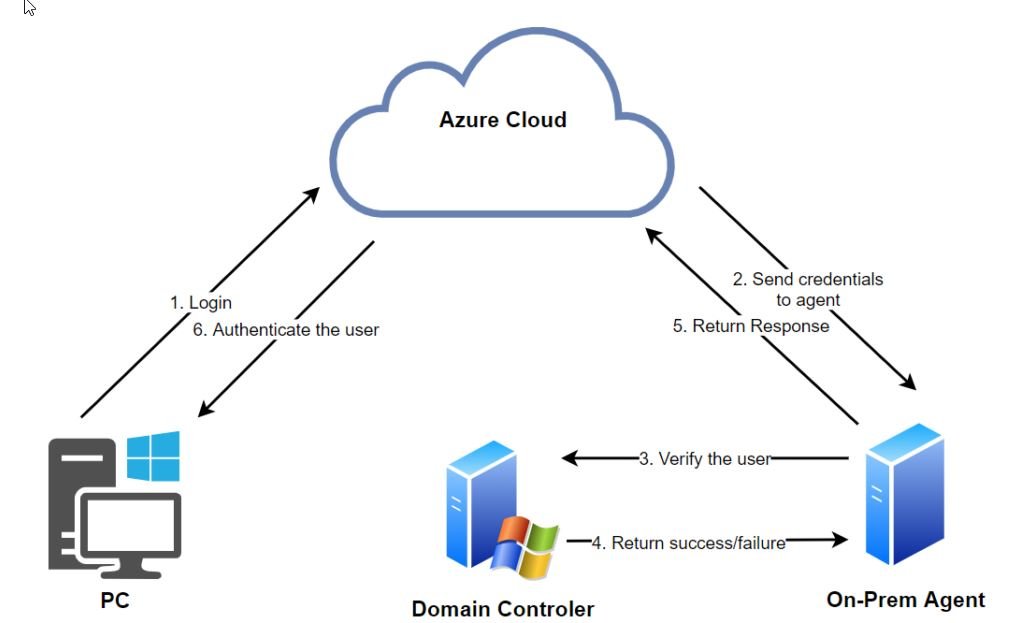
AUTHENTICATION FLOW
- User enters their username and password in Azure AD/O365
- Azure AD encrypts credentials with a public key and places them in the agent queue (a persistent connection created by the on-premises agent). The agent then collects the credentials and decrypts them with their private key
- The agent then authenticates the user to On-Prem DC using the LogonUserW API function
- The DC validates credentials and returns a response
- On-premises DC response is forwarded to Azure AD
- If the user’s login is successful, the user will log in
According to experts, installing a skeleton key on an Azure agent can be useful for:
- Perform a privilege escalation to Global Administrator, allowing you to control your Azure tenant
- Access your organization’s on-premises environment by resetting an administrator password
- Generate persistence in a compromised network
- Collect passwords in non-encrypted text
PREVENTION OF EXPLOITATION
As mentioned, a high-privilege threat actor can use this exploit to install a backdoor or collect non-encrypted plaint-text passwords. Traditional log analysis may not detect this if the attacker is skillful enough.
To prevent this attack variant, administrators can protect Azure Agent servers, monitor user activity for anomalous activity or attempts to access sensitive information, and use classification to discover files that contain clear text usernames and passwords.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
