From our blog, we stress the significance of educating users and staff about the “phishing” and analysis that should be exercised when receiving an email in order to identify phishing campaigns and avoid falling for them, even if they come from reliable links since they may use LinkedIn Smart Links as discovered by the cofense.
How do Smart Links work?
The first thing we need to do is ask ourselves this question. Any premium user of the platform has access to the marketing feature known as “LinkedIn Smart Links,” which enables you to establish a link from a LinkedIn URL to send visitors to relevant web pages or corporate information (such as a phishing page, this being the case).
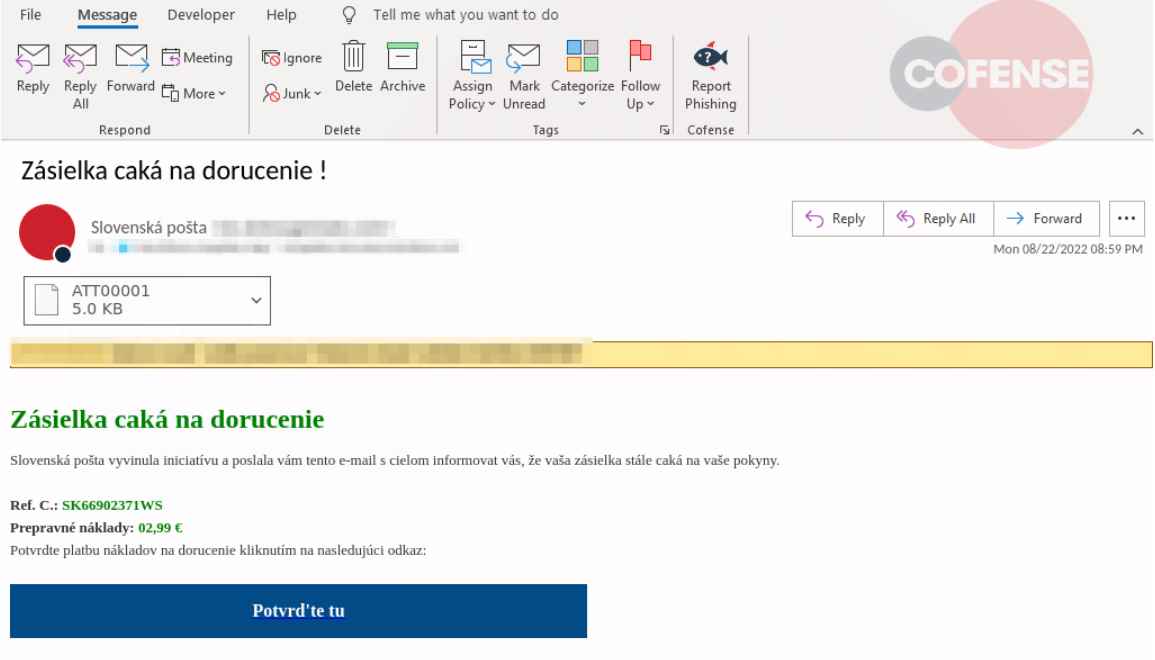
How have they used this resource to their advantage?
Exploiting a genuine LinkedIn connection, cybercriminals have been able to get past the firewalls of several email servers by using these Smart Links. All of those emails would be delivered straight to the inbox.
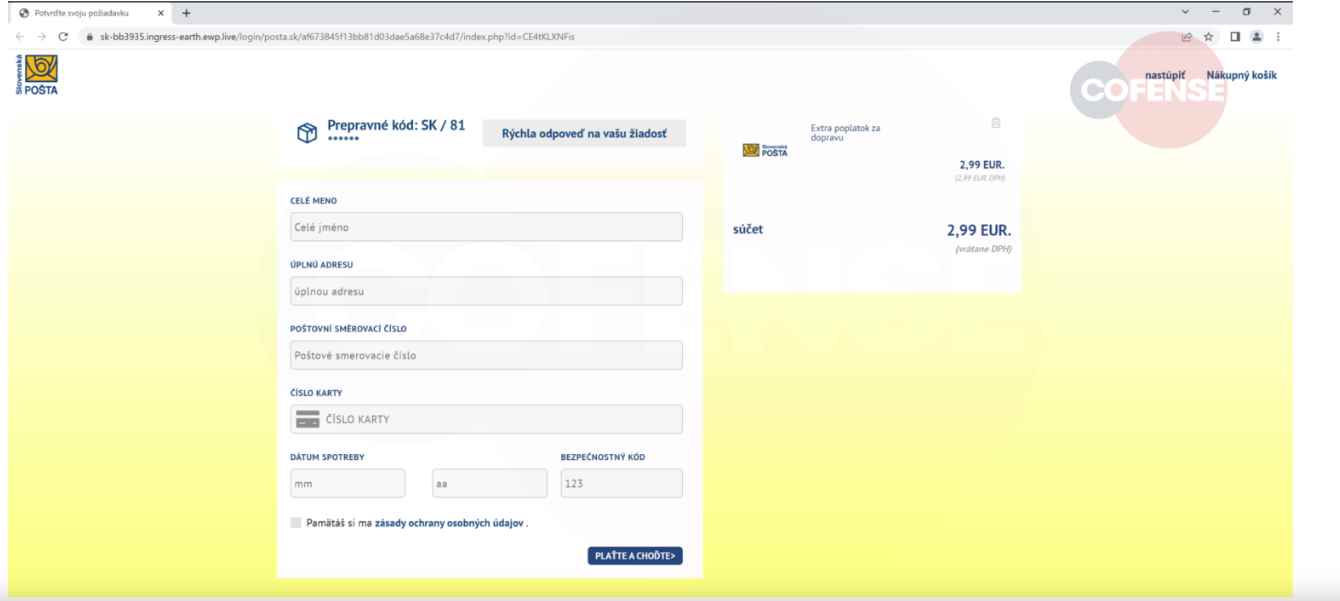
By creating a website that looked just like a payment gateway (faking the Slovenská pota firm), they were able to get around this security mechanism and ask consumers for a little payment in return for obtaining a parcel while it was being delivered. This transfer would be made with the intention of gathering the credit card information from users who desired to “get” the awaiting shipment.
Conclusions
As we stated at the outset of the article, we are raising the alarm once more to remind people to be wary of any links they get, authentic or not, especially if they ask for personal or financial information.
Keep in mind that individuals are still the most susceptible targets for attacks, and phishing efforts are still a legitimate attack channel. As an illustration, consider the recent Uber incident in which the attacker used social engineering to obtain access to the company’s internal network.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
