The ability to evolve is one of the main features of cybercriminals. Cybersecurity experts report that multiple hacker groups are investing a considerable amount of effort and resources to compromise the IT systems of industrial companies in dozens of countries; apparently, these attacks highlight due to their sophisticated features, such as a never seen before encryption scheme and custom exploits for each attacked company.
According to the pattern established thanks to the cases analyzed by Kaspersky experts, these attacks begin with sending personalized emails to specific users in an organization. For the exploit to work, the language in which the email is written must match the location of the target operating system: “If the target is a Japanese company, both the email and the attached document must be written in Japanese”, the experts mention.
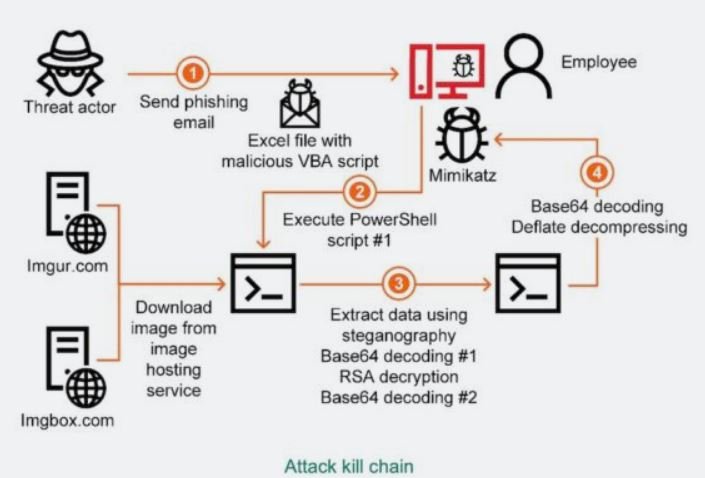
In addition to language requirements, threat actors also rely on an encrypted malware module that can be decrypted when it is confirmed that the operating system is also located in the attacked territory.
Up to this point in the attack there are no clear indications of malicious activity, even if the victims click on the request to enable the contents of the attached document; however, in the background it has already started the running of a PowerShell script with the following parameters:
- ExecutionPolicy ByPass: to override the organization’s policies
- WindowStyle Hidden. This hides the PowerShell window
- NoProfile, which runs the script without end-user configuration
This script could come to imgur.com or imgbox.com to download an image containing the malicious code that will continue with the attack, a technique known as steganography. The data is encoded in Base64 and encrypted with an RSA key to be encoded again with Base64.
Decrypted and decoded data is used as a second PowerShell script that, in turn, unpacks and decodes another Base64-encoded data blob. With that, a third PowerShell script runs the Mimikatz malware that is designed to steal the victim’s Windows account credentials. If the compromised credentials include access to Windows Active Directory, hackers could compromise all nodes on the network.
According to the report, some companies managed to disrupt the attacks before they were completed. Because few attacks have been completed, researchers are still unclear what the operators of this campaign are looking for, although they theorize that hackers might be looking for information from the business customers of the affected companies. These are similar cases to attacks detected in nuclear plants, power companies, refineries and other facilities considered critical infrastructure.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
