A few months ago ESET researchers discovered some attacks against aerospace and military companies in Europe and the Middle East; subsequent analysis revealed some additional details about this attack variant, which had not previously been identified.
The attack, dubbed Operation In(ter)ception, was based on the use of a malware known as Inception.dll. For this attack, hackers employed social engineering through LinkedIn, offering alleged job offers, which, while attractive, were fake and part of the scam.
After establishing contact, the hackers began to send the malware, abusing some legitimate tools and functions of the target operating system. Hackers employed sophisticated techniques to evade detection, including malicious code signing, malware spoofing, and image use from well-known companies.
While the main goal of this operation was espionage, ESET experts detected that hackers even tried to make a profit using a business email engagement attack, a widely known hacking variant. This malicious campaign is still being investigated, although some of the researchers believe that these hackers might have some link to the renowned Lazarus hacker group.
Analysis of the attack
As already mentioned, the attack begins with the publication of fake job offers on LinkedIn in which threat actors pose as HR managers of major companies (usually members of the aerospace industry, although hackers can use the image of other class of companies).
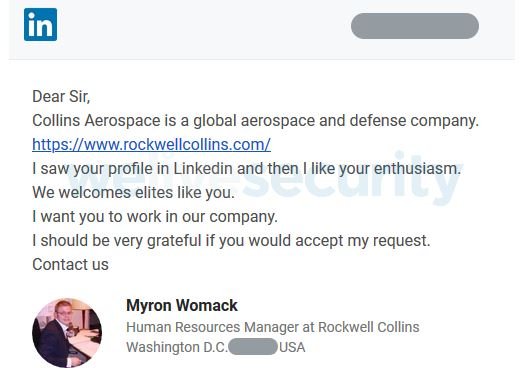
Hackers then search for user profiles in previously selected companies to send them information about fake job offers through the Messaging feature on LinkedIn.
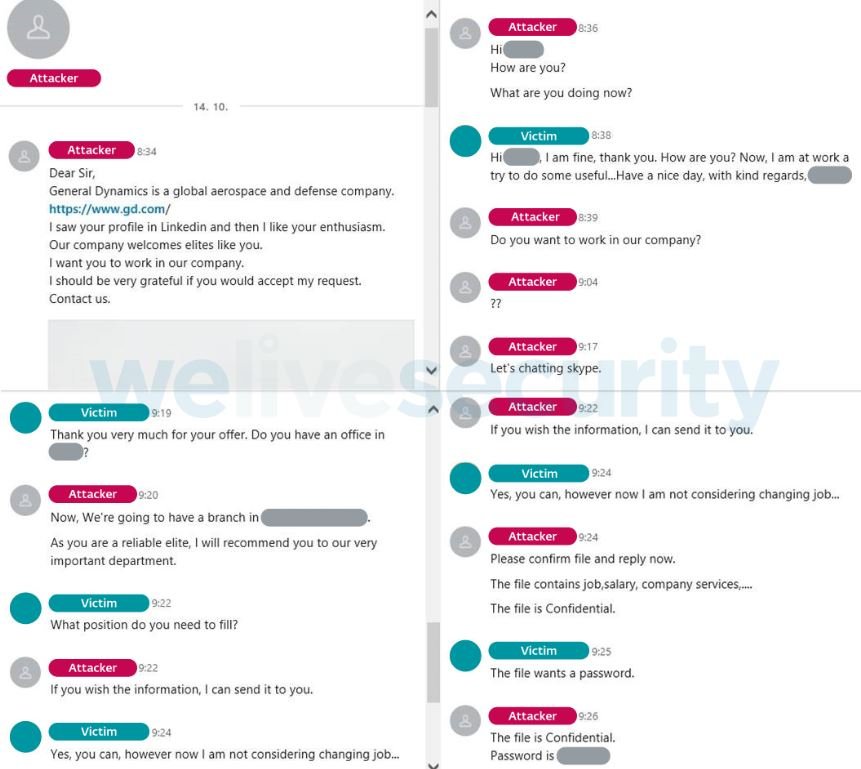
When cybercriminals get to attract the attention of the potential victim, they send malicious files through this platform. Hackers usually use PDF files or links to external sites, such as One Drive.
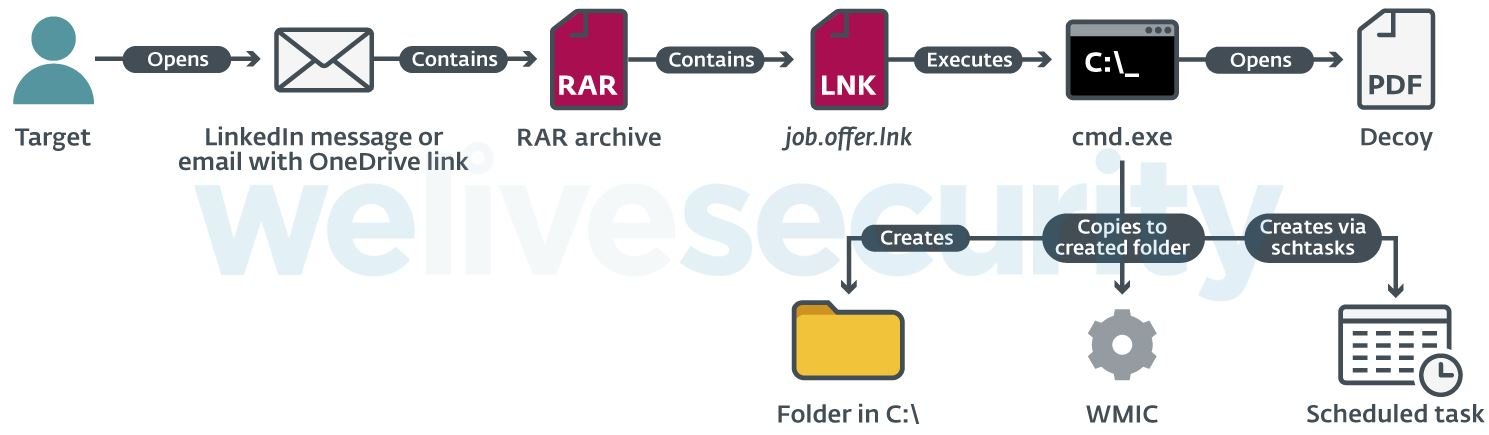
Victims receive a password-protected RAR file that contains an LNK file. When opened, this file starts a command prompt that opens a remote PDF file in the victim’s default browser.
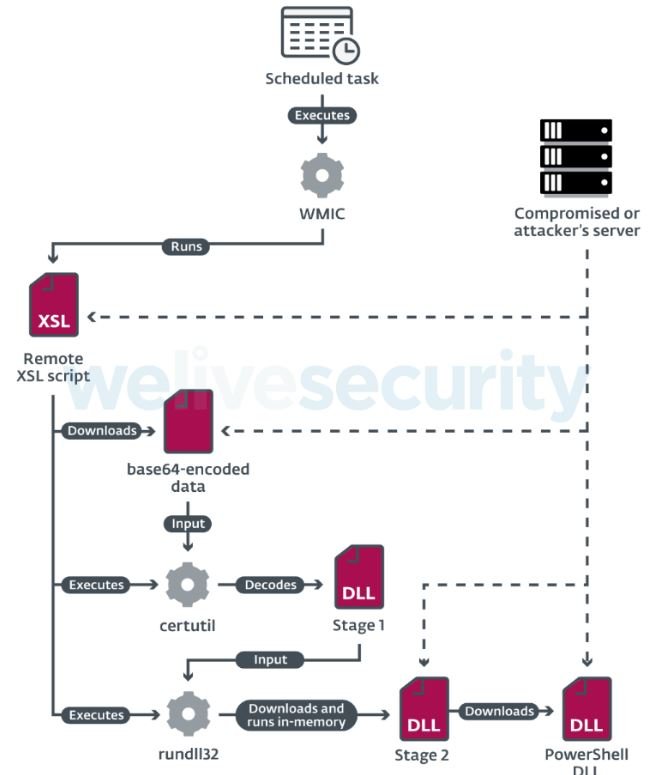
That PDF, which supposedly contains information about the work offered to the victim, only serves as a decoy, because in the background the command prompt creates a new folder and copies the WMI.exe utility and then renames it. Finally, a scheduled task is created, configured to run a remote XSL script periodically through the copied WMIC.exe.
This final step allows hackers to get an initial foothold within the attacked company’s networks and generate persistence.
Hackers’ resources
The operators of this campaign employed multiple hacking tools, including custom malware variants and modified versions of open source tools. The ESET team identified the following tools:
- Custom download tool for the first stage
- Custom download tool for the second stage
- A modified version of PowerShdll
- Custom DLL loaders to run custom malware
- Beacon DLL, used to verify connections to remote servers
- A custom build of dbxcli, an open source command-line client for Dropbox possibly used for extracting sensitive data
Hackers not only used custom malware variants, but also took advantage of some legitimate resources in the target system, a tactic known as <living off the land>> in the cybersecurity community.
A successful Operation In(ter)ception attack would pose a big risk to the target system, so system administrators must remain aware of a potential attack. The best way to prevent these kinds of attacks is to know how to identify a social engineering campaign; for security, remember to verify the authenticity of any job offers received via LinkedIn and other similar platforms.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
